

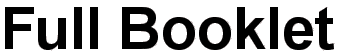
Name | |
Group |
This product is licenced to St. Mary Redcliffe and Temple CE School .
Use and reproduction of this booklet is permitted within the
institution named above, subject to the restrictions set out in the online licence
agreement. All other rights are reserved by the author.
Contents |
| Topic | Section | Topic | Section |
| Information | 1 | Copyright | 28 |
| Information Systems | 2 | Hacking | 29 |
| Hardware | 3 | Health & Safety | 30 |
| Input Devices | 4 | Security | 31 |
| Output Devices | 5 | Backups | 32 |
| Storage Devices | 6 | Viruses | 33 |
| Processing | 7 | Validate & Verify | 34 |
| Software | 8 | Data Collection | 35 |
| Word Processing | 9 | Simulation & Models | 36 |
| Desktop Publishing | 10 | User Interfaces | 37 |
| Graphics | 11 | Algorithms & Charts | 38 |
| Databases | 12 | Programming | 39 |
| Spreadsheets | 13 | Data Transfer | 40 |
| Charting | 14 | Social Issues | 41 |
| Web Design | 15 | Banking | 42 |
| Multimedia | 16 | Supermarkets | 43 |
| Operating Systems | 17 | Systems Lifecycle | 44 |
| Other Software | 18 | Analysis | 45 |
| Comms Methods | 19 | Design | 46 |
| Computer Networks | 20 | Implementation | 47 |
| The Internet | 21 | Testing | 48 |
| E-Commerce | 22 | Evaluation | 49 |
| Global ICT Services | 23 | Documentation | 50 |
| Data Logging | 24 | Thanks | 51 |
| Control | 25 | Legal | 52 |
| Control Programs | 26 | Contact | 53 |
| Data Protection | 27 |
Section 1 : Information |
Computers do not work with information. Information is something which has a meaning. As computers are machines they can not understand the meaning of sentences like "Jane was born on the 14/06/75". Instead computers just store sequences of letters and numbers. They do not know what these sequences mean. The sequences which the computer stores are called data.
Here are some examples of data and information :
| Data | Information |
| 42 190387 Sausage | Total cost of shopping is £23.40 Albert is 14. The sausage is hot. |
Data can become information when it is given a context. For example :
The link between information and data is often described like this :
Information = Data + Context
Information can be quantitative or qualitative :
| Quantitative | Quantitative information is information which can be accurately measured against a scale. e.g. temperature, height. |
| Qualitative | Qualitative information is information which involves an element of judgement or opinion. e.g. Is it better to travel by bus or train? How nice is fish and chips ? |
Knowledge is the information, skills and experiences that have been learned by a human. New knowledge can be created from existing information by applying logical rules to the information. For example if we have the information :
John is Michael's brother. Michael is Mary's brother.
and know the logical rule that :
If person A is B's brother and B is C's brother then A is also C's brother.
Then we can reason that John is also Mary's brother. We have created new knowledge from information by applying rules. Reasoning with information to produce knowledge is one way of processing information, so knowledge is sometimes described as :
Knowledge = Information + Processing
Converting information into data that a computer can process and store is known as coding information. Here are some examples of how information can be encoded as data :
| Information | Example Encoding as Data |
| 22nd June 2002 Male 5 Door Estate Car | 22062002 M 5E |
Coding reduces the amount of data storage space required, can speed up the process of typing the information in and makes it easier to validate (check) data. For coding to work properly everyone who uses an information system needs to know what the correct codes are.
In fact most computers are digital devices and can only store the numbers 0 and 1 in their memories. Letters and other numbers must be encoded as sequences of 0s and 1s (called binary) before they can be stored. This encoding is done automatically by the computer.
Decimal numbers are represented in binary by sequences of 0s and 1s :
| Decimal Number | Binary Number |
| 0 213 | 00000000 11010101 |
Letters and symbols are stored in binary using a standard coding system such as ASCII. Each letter is represented by a unique pattern of 0s and 1s :
| Letter | ASCII Code |
| A P % | 01000001 01010011 00100101 |
You may need to pass information that you have onto another person. When this happens you must choose how to present the information to make sure that the other person understands and remembers it. The same information can be presented in many different ways. For example :
1. | Information about the
profits that a company has made could be presented as a table of figures or a graph.
| 2. | Information about what
a person looks like could be presented as a photograph or a written description of the
person's features.
| |
The best way to present information will depend upon :
This table shows how the same information can be presented in different ways when used for different purposes :
| Information | Purpose | Presentation Method |
| Profits made by a company in the last twelve months. | To show the public how well the company is doing. | As a graph which will show the information simply and highlight any trends. |
| So that an accountant can calculate the tax that the company owes. | As a table of figures which can be used in the calculations. | |
| To explain to shareholders why the company has made the profits that it has. | As a typed explanation on a page possibly with graphs or tables to support it. |
Some audiences may have special needs, so the method used to present information may need to be tailored to these. For example :
| Audience | Presentation Method |
| Young Children | Short words that are likely to be in the childrens' vocabulary will need to be used. Bright colours and images will help to keep the childrens attention, as could animation. |
| Visually Impaired People | People who have impaired visual senses may not be able to see standard size text on a screen. Information could be presented in a large or simple font and in colours that are easier to perceive. Alternatively a speech synthesiser could be used to read out text. |
Computer software such as a word processor, desktop publisher, spreadsheet or graphics package can be used to help present information. Information can be presented on paper as a hard copy or on screen in the form of a multimedia presentation.
Information systems present the results of processing using an output device.
1. | Data is raw figures, text etc. which have no meaning by themselves.
|
| 2. | Information is data that has been placed in a context so that it has a meaning to a human being.
|
| 3. | Computers do not process
information, they process data.
|
| 4. | Data can become information when it is given a
context : Information = Data + Context
|
| 5. | Information can be qualitative or quantitative :
| 6. | Knowledge is the information, skills and experiences that have been learned by a human. New knowledge can be created from existing
information by applying logical rules to the information : Knowledge = Information + Processing
|
| 7. | Coding or encoding information is converting information into data so that it can
be stored and processed.
|
| 8. | Most computers store data digitally. Numbers are stored as binary patterns (0s and 1s) and characters and symbols are represented
using a standard coding system such as ASCII.
|
| 9. | Information can be presented in different ways. How you choose to present information will depend upon :
|
| 10. | If an audience has special needs then the method of presenting information must be tailored to these.
|
| 11. | Information systems present information on an output device.
| |
Section 2 : Information Systems |
Information is stored and used by organisations such as the government, companies and clubs for a variety of purposes. Some examples of people who store and use information are :
| Organisation | Information Stored | What The Information Is Used For |
| School | Name and addresses of pupils. Pupils’ marks. | Produce reports, set classes. |
| Doctors Surgery | Names and addresses of patients. Previous illnesses. Visits to hospital. Allergies. | Help doctor diagnose illnesses and prescribe treatment. |
When a system has been set up to store and carry out tasks using information we call this an information system. Today most information systems use computers, but this has not always been the case and some information systems are still operated manually.
When we talk about computerised information systems we can use a better definition of the term information system :
An information system consists of everything needed to perform a particular task using information. This will include hardware, software and the people who use the system.
This model can be used to describe the operation of any information system.
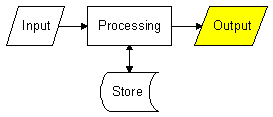
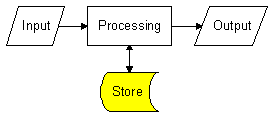
The model has three essential components :
Input : Information going into an information system.
Processing : Organisation and manipulation of data by an information system.
Output : Information produced by an information system.
Most information systems also have a fourth component :
Store : The ability to remember information temporarily or permanently.
Information systems usually include many inputs and outputs. The next pages contain two more detailed examples of information systems.
Description of System
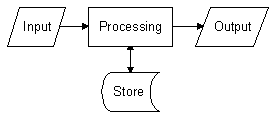
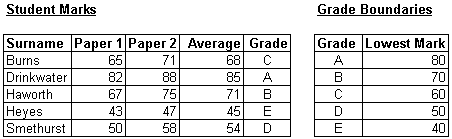
A teacher uses a spreadsheet package to help her analyse the results that her students have obtained in their GCSE Information and Communication Technology mock examination. The teacher enters the names of each student into her spreadsheet. She also enters each student's percentage scores in two different exam papers.
The teacher must decide what average mark a student will need to obtain to get a particular grade on his or her end of year report. For example she may decide that anyone who scores above 80% will get an A, anyone with a score between 70% and 80% will get a B and so on. The dividing point between two grades is known as a grade boundary. The grade boundaries must also be typed into the spreadsheet.
The spreadsheet then calculates the students' average scores and gives each student a grade based on their average. At this point a report is printed for each student to inform them of their marks and grade.
The spreadsheet now performs some further processing. It sorts the students into order so that the student with the highest mark is at the top and the student with the lowest mark is at the bottom. The teacher then prints this list for her own records.
Here is the spreadsheet that the teacher uses :
Identification of Outputs, Inputs, Processing and Storage Requirements
From this description of the system, it is possible to identify what the outputs, inputs, processing and storage requirements of this system are. They are summarised in this table :
| Outputs | A report for each student showing scores in each paper, average score and grade. |
| A list showing the marks and grade of each student in ascending order of mark. | |
| Inputs | The names of the students. |
| The scores of each student in the two examination papers. | |
| The grade boundaries for each grade. | |
| Processing | Average the marks of each student in the two papers. |
| Award grades based on the students' average marks. | |
| Sort the list of students into ascending order by mark. | |
| Storage | This system does not need to store any data permanently, but the teacher will probably find it useful to save the spreadsheet so she can reuse it later. |
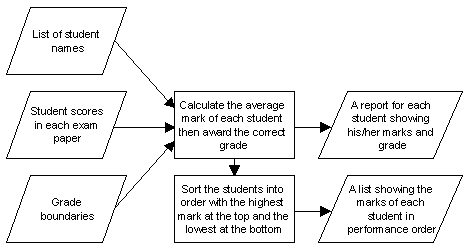
Diagramatic Model of System
This system flowchart shows the structure of this information system in diagram form :
Description of System
A small store uses a very simple stock control system. The system stores the details of all of the products that the store sells. These details are kept in a stock file on a magnetic disk. Each product that the store sells can be identified by a unique product code.
When a customer takes her shopping to the checkout the checkout operator inputs the product code numbers from the items that are being purchased using a bar code reader. If a product code is scanned correctly then the till beeps. If the code is not scanned correctly then there is no beep so the operator knows that the bar code must be rescanned. If the code will not scan a second time then the operator must manually type the product code into the till using a keyboard.
When a code is successfully entered, the checkout looks up the product code in the stock file. From the stock file the name of the product and its price is obtained. This information is printed on the customer's receipt and the total cost of the purchases is calculated.
At the same time the record that the computer keeps of how many units of each product are in stock is amended to show which items have been sold. At the end of the day the checkout will print a list of the items that are running low on stock so that they can be reordered.
Identification of Outputs, Inputs, Processing and Storage Requirements
From this description of the system, it is possible to identify what the outputs, inputs, processing and storage requirements of this system are. They are summarised in this table :
| Outputs | Itemised till receipt for each customer. |
| Buzzer noise when a product code is scanned correctly. | |
| List of products which need reordering to be printed at the end of each day. | |
| Inputs | Product code of each product that is sold to be entered using a bar code reader or keyboard. |
| List of all of the products that the shop sells to be entered when the system is first set up and amended later as necessary. | |
| Processing | As products are sold look up product codes in stock file. Print item names and prices on receipt and add up totals. |
| Monitor how many units of each product are in stock by reducing the stock level of an item when it is sold. | |
| Storage | A stock file will be held on magnetic disk. For each product the shop
stocks this file must contain :
|
Diagramatic Model of System
This system flowchart shows the structure of this information system in diagram form :

In some information systems, the outputs that the system produces can generate further inputs. When the outputs of a system affect its inputs we say that feedback is occuring. Our model can be extended to incorporate feedback like this :

Feedback occurs in two different types of information systems :
| System Type | Explanation | |
| Control Systems | Computerised control systems use sensors to gather data. They switch devices on and off based on the data gathered. A control system for a greenhouse could incorporate a temperature sensor which measures the temperature in the greenhouse and a heater to warm it when it is cold. When the system detects it is cold the heater is turned on. This changes the temperature. The output (heat) affects the input (temperature) so feedback occurs. | |
| Turnaround Documents | Some information systems produce as output forms which the user must fill in. When the user has completed a form the extra information added onto it is entered into the computer. These documents are known as turnaround documents. Because the completed output forms are used to produce new inputs feedback occurs. |
Why Computerise An Information System ?
Most organisations use computerised information systems instead of manual systems. Computerised systems have many advantages. Three of the most important reasons for choosing to use a computerised system are :
This table lists some examples of how these advantages are useful to organisations.
| Advantages of Computerised Information Systems | ||
| Category | Advantage | Example Use |
| Storage | Data stored electronically by a computer can be stored in a much smaller space than the same data would require if it was stored on paper. This makes data storage cheaper so companies can now store much more data than they would have in the past. | In the past a telephone company only stored the total cost of the calls that each customer made. Now the company can store details of each individual call that a customer makes and provide much more informative bills. |
| Electronically stored data can be retrieved very quickly. | A policeman following a car can extract information about the car from a database of over 20 million cars in just a few seconds. | |
| Processing | Computers can manipulate and analyse huge quantities of data accurately at very high speeds. As a result companies can make better use of the information they store and perform some types of analysis that would not be possible with a manual system. | A supermarket can analyse the shopping habits of its customers based on their purchases. This information can then be used to send appropriate special offers to customers who are likely to be interested in them. For example people who buy dog food every week might be sent a special offer for dog biscuits. |
| Using a Network to Share Data | The same information can be available at many different computer terminals in many places at the same time. | You can obtain information about your bank account from any branch of the bank not just your local branch. You can take money from cash machines (ATMs) around the world. |
| Information can easily be shared between different companies or different parts of the same company. | Credit reference agencies collect data about the financial status of members of the public. If you buy any goods on credit then a credit reference agency will be contacted to see if you are likely to repay the money you borrow. The agency will have collected data about you from many places such as your bank, the electoral register and any companies that you regularly pay bills to. | |
| Information can be transmitted electronically around the world almost instantly. | Electronic mail can be used to send important documents very quickly. | |
Why Not Computerise An Information System ?
Despite all of these advantages some manual information systems are still used. These systems are often kept because :
| 1. Information is stored by many organisations and companies such as banks, hospitals, libraries and schools.
| 2. | An
information system performs a particular task using information.
|
| 3. | Information systems can be either
manual (e.g. a filing cabinet) or computerised.
|
| 4. | A computerised information system
consists of everything needed to perform a particular task using information. This will
include hardware,
software and the people who use the system.
|
| 5. | Any information system can be
described in terms of this model containing input, processing, output and storage
stages.
|
|
Section 3 : Hardware |
A computer system will input, process and then output data. A computer system consists of the computer and other hardware devices that are used with the computer. A hardware device is an electronic or electro-mechanical device such as a keyboard or monitor which forms part of a computer system.
The diagrams below show one simple and one more complicated computer system.

The devices connected to the computer can be divided up into three different classes :
| Input Devices | An input device takes data from the outside world and sends it to the computer. e.g. keyboard, mouse. |
| Output Devices | An output device takes data from the computer and converts this into information in a form which is normally understandable by humans. e.g. printer, VDU. |
| Input / Output (I/O) Devices | Data flows in both directions between the computer and an I/O device. Most I/O devices are used for storage e.g. hard disk drive or communications e.g. modem. Others include MIDI keyboards. |
Some devices such as disk drives, modems and CD-ROM drives are now built into the same box as the computer. This helps to keep computers tidy. Devices connected to a computer are often known as peripherals.
Computer hardware is not very useful by itself. The hardware needs to be told what to do. A computer program contains instructions to tell the computer hardware what to do to carry out a particular task. Computer programs are produced using a programming language. Computer programs are also known as software. The most important piece of computer software that a computer system must have to function is an operating system. Other useful pieces of computer software include word processors, spreadsheets and databases.
There are separate articles on the many different items that could be included in a computer system. As a starting point, here is a brief list of the components that you would expect to find inside a typical computer :
Computer systems are designed to be flexible. It is usually possible to expand the capabilites of a computer by replacing or upgrading internal components or connecting extra devices externally. External devices are connected to a computer using sockets known as ports.
There are three main types of computer. They are :
Microcomputers (also known as PCs) are the smallest and cheapest of these and are used at home, in schools and in some businesses. Most PCs contain just one microprocessor.
Mainframe computers are the most powerful computers. A mainframe computer may contain several microprocessors. Computers which contain more than one processor are capable of doing more than one thing at a time and are described as being capable of parallel processing. A single mainframe computer can be used by hundreds of people at once. Each user has his own terminal that is connected to the mainframe. Mainframe computers are usually kept in a special cooled, clean computer room. Today many businesses are getting rid of their mainframe computers and replacing them with networks of smaller microcomputers.
Minicomputers were medium-sized computers that were more powerful than microcomputers but not as powerful as mainframes. Minicomputers where phased out in the 1990s as microcomputers became more powerful.
This table makes some comparisons between the different types of computer :
| Comparisons of Computer Types | |||
| Comparison | Microcomputer | Minicomputer | Mainframe |
| Where Used | Home, small business, on a network in a larger business. | Medium sized business. e.g. supermarket, traffic control system. | Large businesses, universities. |
| Number of Users | 1 | 1-20 | Hundreds |
| Cost | £200 - £10,000 | Not Available | £150,000+ |
A Supercomputer is a very fast mainframe which may contain many hundreds of microprocessors.
A microcomputer is a computer that is based around a microprocessor. The most common type of microcomputer is the Desktop but there are a number of other types as well :
| Type | Description |
| Desktop | The Desktop is the most common type of microcomputer. Desktop PCs are quite bulky and are usually connected to several external peripherals such as a mouse, keyboard and printer. Desktop machines are not very portable but can be upgraded fairly easily to enhance their capabilities. |
| Laptop | A laptop is a small microcomputer which is portable. Laptops are battery powered and incorporate all of the important components of a computer system such as keyboard and VDU into one unit. Most laptops are about the size of an A4 folder. Laptops are also known as notebooks. |
| Palmtop or PDA | A Palmtop or Personal Digital Assistant (PDA) is a very small microcomputer which is designed to be handheld and fit in a jacket pocket. Palmtops/PDAs can carry out general purpose computing tasks and are usually supplied with software such as a diary and address book to help the owner organise his life. |
| Games Console | A games console is a microcomputer that has been specifically designed to play computer games. It will probably incorporate a CD-ROM or DVD drive to load the games from and be supplied with an input device consisting of a joystick and small keypad. |
| Embedded System | An embedded system is a computer system which forms part of a larger device such as a washing machine, video recorder or car. Embedded systems are usually suited to just one specific task and can not be connected to general purpose peripherals such as keyboards and printers. Embedded systems are often used in control applications to perform real time processing. |
| 1. A computer system will input, process and then output data.
| 2. | A
computer system consists of
the computer and other hardware devices that are used with the computer.
|
| 3. | A
hardware device
is an electronic or electro-mechanical device such as a
keyboard or
monitor which
forms part of a computer system.
|
| 4. | The devices connected to the
computer can be divided up into three different classes :
Input Devices, Output Devices and Input/Output Devices.
|
| 5. | Devices connected to a computer are often known as
peripherals.
|
| 6. | Computer hardware is not very useful
by itself. Software is required to tell the hardware what to do.
|
| 7. | Computer systems are designed to be expanded, but a typical computer will have these items inside it when it is purchased :
|
| ||||||||||||||||||||||||||||||||||||||||
Section 4 : Input Devices |
An information system can not do anything until you give it some information to process. Input devices transfer data into a computerised information system so that it can be processed.

An input device transfers data from the outside world into a computer.
There are two different categories of input device. They are :
There are many different input devices available. Each input device is suitable for a different purpose. Select an input device from the table below to find out about it or read through the rest of this topic to learn more about all of the different input devices.
| Manual Input Devices | ||
| Keyboards | QWERTY Keyboard | |
| Concept Keyboard | ||
| Pointing Devices | Touch Screen | |
| Light Pen | ||
| Mouse | ||
| Tracker Ball | ||
| Touch Pad | ||
| Joystick | ||
| Graphics Capture | Graphics Tablet | |
| Scanner | ||
| Digital Camera | ||
| Video Capture | ||
| Sound Capture | Voice Recognition | |
| MIDI | ||
| Others | Remote Control | |
| Biometric Devices | ||
| Sensors | ||
| Direct Data Entry (DDE) Devices | ||
| Code Numbers | Bar Codes | |
| Magentic Ink Character Recognition | ||
| Magnetic Stripe Codes | ||
| Smart Cards | ||
| Optical Input Methods | Optical Mark Recognition | |
| Optical Character Recognition | ||
| Turnaround Documents / PDET | ||
Almost all general purpose computers are supplied with a keyboard. A keyboard has over 100 keys on it. When you press a key a number (code) is sent to the computer to tell it which key you have pressed. The keys are arranged in four groups :
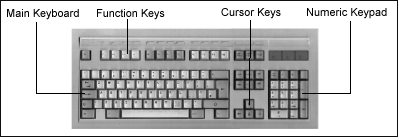
The keys on a keyboard are usually arranged in the same order as those on a typewriter. This layout of keys is called QWERTY because Q-W-E-R-T-Y is the order in which the letters occur on the top row of the keyboard. Some newer designs have the letters arranged in a different order. Most people find the QWERTY arrangement best as they have had some practise using it, but some users trained on the new keyboards claim that they can type faster than the fastest typists can on QWERTY keyboards.
A concept keyboard is a flat board which contains a grid of switches. Each switch can be programmed to do whatever you want. An overlay image is placed on top of the grid so that the user can tell what pressing on different areas of the keyboard (switches) will do.
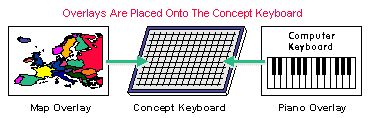
Example uses of concept keyboards include :
Concept keyboards are particularly useful for users such as children who would find using a QWERTY keyboard difficult and in locations where an ordinary keyboard might be damaged, e.g. by spillage or dust.
A touch sensitive screen is a special type of visual display unit. In front of the display a grid of light beams or fine wires criss-cross the screen. When you touch the screen the computer senses where you have pressed. Touch screens can be used to choose options which are displayed on the screen.
The main application for which touch screens are used is the provision of public information systems. Touch screen operated computers can be found in places such as travel agents and airports. Here a touch screen is being used to provide information to tourists :

The grid in front of the screen can not be seen by the user. The screen is located behind the glass in the tourist office's window so that visitors can obtain information even if the office is closed.
Touch screens are not used very often as they are not very accurate, tiring to use for a long period and are more expensive than alternatives like a mouse. The main advantage of the touch screen is that anyone can use it without having to be trained.
A light pen is a special pen which you can point at any computer monitor. When the pen is pointed at the screen the computer can work out where the pen is pointing.

Light pens can be used to "draw" on the screen or to select options from menus presented on the screen.
Light pens are extremely poor input devices. They are very inaccurate and tiring to use. Light pens were popular in the 1980s and early 1990s but most have now been replaced with other input devices.
A mouse is the most common pointing device. You move the mouse around on a mat and a small cursor called a pointer follows your movements on the computer screen. By pressing a button on the mouse (most mice have 1,2 or 3 buttons) you can select options using icons or menus on the screen. Mice can also be used to "draw" onto the screen. They are particularly useful if your computer has a graphical user interface.

Most mice use a small ball located underneath them to calculate the direction that you are moving the mouse in. As you move the mouse this ball rotates. The mouse monitors how far the ball turns and in what direction and sends this information to the computer to move the pointer.
A tracker ball (or trackball) is an alternative to a mouse. It operates in the same way as a mouse except that the ball is on top. Turning the ball with your hand moves the pointer on the screen.
Tracker balls are popular when there is not enough space for a mouse, e.g. in portable computers. Most tracker balls have buttons next to them which can be used to select options from the screen.
A touch pad is another alternative to a mouse. It is a pointing device which is used in laptop computers. A touch pad is a rectangular pad about 4cm x 4cm in size. You can move your finger around on top of the touch pad. As your finger moves, the pointer follows its movement on the screen.
Buttons are usually placed next to the touch pad. Pressing a button will select an option on the screen just like a mouse button. With some touch pads, if you tap the pad sharply with a finger this will have the same effect as pressing one of the buttons.
Joysticks are popular for playing computer games and controlling computer simulations. You can move a standard joystick in any one of eight directions. The joystick tells the computer in which direction it is being pulled and the computer uses this information to e.g. move a spaceship on screen. A joystick may also have several buttons which can be pressed to trigger actions such as firing a missile.

The best joysticks, called analogue joysticks measure how far the joystick is being moved in the direction it is being pulled. This information is used to set how quickly the object on the screen moves. The further you push the joystick the faster the object moves.
Small joysticks called trackpoint devices are sometimes built into the keyboards of portable computers and used instead of a mouse.
Graphics tablets are mainly used by professional graphics designers. Using a graphics tablet a designer can produce much more accurate drawings on the screen than he could with a mouse or other pointing device. A graphics tablet consists of a flat pad (the tablet) on which the user "draws" with a special pen called a stylus. As the user "draws" on the pad the image is created on the screen. The pad on which the user draws can be any size from A5 to A1 (eight times as large as an A4 page). Drawings created using a graphics tablet can be accurate to within hundredths of an inch. Graphics tablets are also known as graphics digitisers.

The stylus that the user draws with may have a button on it which will act like a mouse button. Sometimes instead of a stylus a highly accurate mouse-like device called a puck is used to draw on the tablet.
Graphics tablets are often used to provide input to Computer Aided Design packages.
A scanner can be used to input printed images such as photographs or pages of text directly into the computer. A scanner works by shining a light at the image being scanned and measuring how much light is reflected back using an optical sensor. The amount of light that is reflected back tells the computer how light or dark the image is at each point.

Optical Character Recognition (OCR) software can be used to read printed text from an image that has been scanned and store it as text rather than an image. You can then edit the text using a word processor or desktop publisher. OCR software is not yet sophisticated enough to read hand-written text accurately.
Digital cameras are used in the same way as standard photographic cameras. Most digital cameras look just like ordinary cameras. Unlike photographic cameras digital cameras do not use film. Inside a digital camera is an array of light sensors. When a picture is taken the array of sensors is used to input the image. The image can then be stored either in the camera's RAM or on a floppy disk. Later the pictures can be transferred onto a computer for editing using a painting package.

Digital cameras are available from about £30 upwards. The quality of the pictures that a camera can take depends upon the resolution of the camera. This is measured in millions of pixels (megapixels). Modern cameras have resolutions from about 1 to 5 megapixels. Digital cameras are extremely useful for tasks such as producing newsletters. The images can be transferred directly into a desktop publisher without having to be developed, printed and then scanned.
Computers store videos as a sequence of still images called frames. These images are displayed quickly one after the other (rather like a flick-book) to create the illusion of a moving picture. Inputting a video into a computer is known as capturing the video. When you want to capture a video sequence you must tell the computer :
If you want to capture large images you may have to settle for a slow frame rate which will make the captured video film look jittery. If you want a fast frame rate you may only be able to capture a small image size.
The three most common devices that can be used to capture videos are :
| Video Digitiser | A video digitiser takes an image from a video camera or television and converts it so that it can be stored on a computer. Video digitisers can capture large images at fast frame rates. Many video digitisers now incorporate a television tuner so that television pictures can be captured directly. |
| Web Camera | A web camera captures video images for transmission over the Internet. Web cameras capture small images at a slow frame rate. They are cheap to buy. |
| Digital Camera | Most digital cameras that take photographs can also capture short video sequences. |
Voice recognition systems listen to what people are saying and carry out the instructions given to them when people speak. A microphone is used to provide input for a voice recognition system. Currently these systems are not very sophisticated and are used only for certain applications. Existing voice recognition systems come in two different types :
In the last few years a number of voice dictation packages have been developed. These packages let the user dictate text into a computer to appear in a word processed document. Dictating like this can be much quicker than typing but the computer still makes some mistakes especially with short words and with words that sound the same but are spelt differently. e.g. there and their.
The Musical Instrument Digital Interface (MIDI) system allows a musical instrument to communicate with a computer system. The musical instrument acts as an input device to the system. As it is played computer software records information about the duration, pitch and volume of each note.
Music input into a computer by a MIDI instrument can be saved or edited by the user. It can also be printed out as a musical score. The computer can play the recorded piece of music either through its own speakers or through a MIDI instrument that is being used as an output device.
Sophisticated MIDI software can receive inputs from up to sixteen musical instruments at once and can play music back on many instruments simultaneously. The various instruments can all be sequenced together so that they play back in time with each other.
A remote control is used to operate a machine from a distance. Remote controls are used with consumer devices such as televisions and hi-fi music systems and vehicle locking systems.
Remote controls have a small keyboard on them with buttons that relate to the particular functions of the machine that is being controlled. When the buttons are pressed a signal is sent from the remote control to the machine, usually by infra-red light or radio signal.
It is more convenient to be able to operate a machine remotely than to have to move to the machine to use it.
A biometric input device measures a unique physical chracteristic of a person. The most common biometric devices are used to input a person's fingerprint into a computer. More sophisticated devices use a camera to input a description of a person's iris (the coloured part of the eye).
Biometric devices are usually used for security purposes. A record of a person's fingerprint or iris pattern is stored in a database. Later on the identity of a person can be determined
by re-scanning the finger or eye and looking up the results of the scan in the database. Biometric devices provide a very reliable way of identifying people. Real world applications of this include :
| Access Control | A biometric security system can control access to computer files or buildings instead of passwords or keys. |
| Passports | Biometric information can be included in electronic passports, making it much harder for a passport to be fraudulently used. |
A sensor is a device which measures a physical quantity such as the temperature and then sends a voltage to the computer representing the quantity. Sensors can be either analogue or digital :
Digital : Sensors are either on or off. For example a switch of pressure pad.
Analogue : Sensors can measure a range of values. The size of the voltage the sensor produces is determined by the size of the quantity that the sensor has measured. For example if a cold temperature is measured a small voltage will be sent, whilst if a hot temperature is measured a larger voltage will be sent.
There are lots of different sensors available, each of which is designed to measure a specific quantity. Examples of sensors include :
| Sensor | Type | Quantity Measured | Application |
| Temperature sensor | Analogue | How hot/cold it is. | Monitoring the temperature of a science experiment. |
| Light sensor | Analogue | How light/dark it is. | Turning street lights on when it is dark. |
| Pressure Pad | Digital | If a pad is being pressed. | Detecting cars arriving at a car park barrier. |
| pH sensor | Analogue | The acidity of a liquid. | Monitoring river pollution. |
| Button | Digitial | If the button is being pressed. | Obtaining a ticket at a car park entry barrier. |
| Light Gate | Digital | Detects an object passing through the gate. | Measuring the speed or acceleration of objects. |
Sensors are usually used in data logging and control systems.
Barcodes are often printed on products that you can buy and are used by shops and supermarkets to produce bills for customers. A barcode is made up of a sequence of bars of different widths. Different groups of bars are used to represent different numbers. A printed barcode is therefore simply a way of representing a number. The number is often printed above or below the barcode so that humans can read it.
Barcodes are read into the computer using a wand or a fixed scanner. Barcodes are not easily damaged and can normally still be read if they are creased or not stuck onto a flat surface. They can be printed using a normal printer and ink and so are cheap to produce. The information normally included on a barcode for a product is country of origin, manufacturer and item code. The price is not included in the barcode.

A scanner can read a barcode number incorrectly. A check digit is included in the barcode number to reduce the likelihood of this happening.
The Magnetic Ink Character Recognition (MICR) system reads characters printed in a special magnetic ink into the computer. The main users of MICR are banks. They use it to read information from cheques into their computers so that the cheques can be cashed. Here is some information stored on a cheque using MICR :
![]()
The information printed on the cheque using MICR is :
MICR readers can only read one special font which can represent only numbers and a few punctuation marks. They can read characters very quickly and with 100% accuracy. Information printed in magnetic ink is also very secure. It is not possible to change the information by writing over it with a pen and the printed numbers are not damaged by folding (as often happens with cheques). Both the reader used by MICR and the special ink are expensive.
Magnetic stripes (or strips) are built into many plastic cards such as cheque guarantee or credit cards. Magnetic stripes look like this :

The strip can contain up to 60 characters (numbers or digits) of information which is stored magnetically. Usually the information is put onto the stripe when the card is made and is never changed. Magnetic stripe codes can also sometimes be found on the back of railway tickets.
To be read the card is swiped through a machine which quickly and accurately reads the pattern of magnetism. The information stored on the card can be destroyed by exposure to magnetic fields, by scratching or by coming into contact with some liquids.
For many purposes cards that incorporate magnetic stripes are now being replaced with smart cards.
Smart cards are often called input devices. In fact they are actually simple storage devices. A smart card looks like a magnetic stripe card but it contains a small RAM chip. When the card is put into a machine data can be read from the card or written onto it. A smart card can store much more data than a magentic stripe card can. The most popular card in use at the moment can store up to 4Kb (about 4000 characters) of information but cards with capacities up to 1Mb (1,000,000 characters) are available.
Petrol companies and supermarkets use smart cards to store information about points that customers earn when they buy goods. Every time the customer buys something the number of points stored on the card is increased. The customer can then spend these points to buy goods. Many banks now issue debit cards that are smart cards as these are more secure than traditional magnetic stripe cards.
Some smart cards contain a small microprocessor as well as memory. These cards are practically a complete computer system on a card. They are used for applications such as decoding pictures from satellite television stations.
An optical mark recognition (also known as OMR or mark sense) system reads marks made by pencil on a printed form into the computer. OMR systems are used by examination boards to collect the answers to multiple choice examinations and to purchase lottery tickets. Here is an example answer grid for an examination :
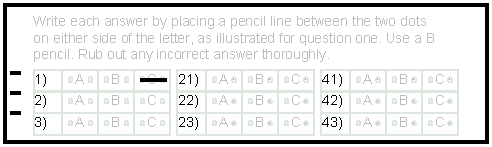
The student answers each question by drawing a line in pencil in the box that he/she thinks is the correct one. The answer grid is printed in a special coloured ink called that the OMR system will ignore. Marks down the side of the form are used to automatically line the form up in the reader so that it can be read. The reader detects where the marks are placed by shining a light at the page and measuring the amount of light reflected. Less light is reflected where the marks have been made. A pile of forms collected at the end of an examination can be put into a tray (called a bin). The reader will go through each form in turn and record the candidates marks.
Input using OMR is accurate and very fast. Problems can occur if the OMR forms get creased as the reader may jam.
An optical character recognition system consists of a scanner and some software. The scanner is used to scan an image of a page of text to be read into the computer. The software then examines the page and extracts the text from it, storing it in a form that can be processed.

OCR systems can now recognise a wide variety of computer fonts and read letters with over 99% accuracy. Some systems will recognise hand-written text reasonably well as long as it is written very neatly and usually put into boxes on a pre-printed form.
Optical mark recognition and optical character recognition are often used together in a turnaround document. A turnaround document is a document which :
Has some information printed onto it by a computer.
Has more information added to it by a human.
Is fed back into a computer to transfer the added information into the computer.
Here is a turnaround document that a gas company could use to record meter readings.
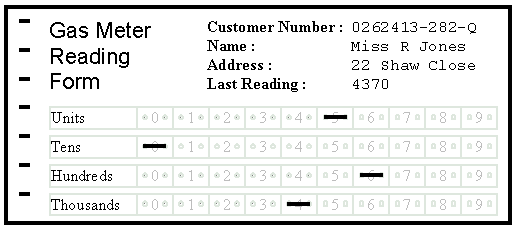
The document is printed by a computer. The name, address and customer number of the person that the meter reader should visit is printed on the form. The customer's last meter reading is also included.
The meter reader takes the document and visits the customer's house. He then marks the current meter reading onto the OMR grid on the form. In the example the meter reader has marked the reading as 4605. The form is then returned to the gas company.
At the gas company the form is fed into a special reader. Optical character recognition is used to read the customer's number from the form. Optical mark recognition is used to read the meter reading that has been added. All of the information can be read into the computer automatically. A bill can be produced and posted to the customer without any need for human intervention. Turnaround documents allow cheap, fast input of information into a computer system
The turnaround document does not contain any instructions because the meter reader who fills it in will complete hundreds of similar forms every day. He will have been trained to use the forms so printing instructions on them would simply waste space.
Data can also be printed on turnaround documents in barcode format.
Alternatives to Turnaround Documents
In some industries turnaround documents are being replaced by small handheld computers. For example many gas companies now issue their meter readers with handheld computers. At the start of the day the names and addresses of the customers that the meter reader must visit are downloaded into the computer. As the meter reader visits customers' homes, he types the meter readings into the computer. At the end of the day the readings can be transferred automatically onto the main computer to issue bills. Handheld computers used to enter data into a computer system are known as Portable Data Entry Terminals (PDET).
| 1. An input device transfers data from the outside world into a computer.
| 2. | There are two different categories of input device. They are :
|
|
| Manual Input Devices | ||||
| Input Device | Example Use | Advantage | Disadvantage | |
| QWERTY Keyboard | Word processing. | Typists can use with ease to enter any textual data. | Relatively slow. | |
| Concept Keyboard | Children's toys, tills in restaurants / pubs. | Can be operated by novices or people who can not manage a normal keyboard. | Needs to be customised for each application. | |
| Touch Screen | Information system in tourist office window. | Can be used where a mouse or keyboard might get wet or dirty. | Tiring to keep touching screen. | |
| Light Pen | Drawing on screen. | Cheap to manufacture. | Extremely inaccurate and awkward to use. | |
| Mouse | Moving a pointer on screen. | Easy for novices to use for drawing or to choose options off the screen. | Requires a lot of space to use. | |
| Tracker Ball | Moving a pointer on screen. | Does not need as much space as a mouse. | Not as intuitive to use as a mouse. | |
| Touch Pad | Moving a pointer on screen. | Does not need as much space as a mouse. | Not as intuitive to use as a mouse. | |
| Joystick | Playing games or controlling robots. | Allows fast, natural directional interaction needed for games. | Not as accurate as a mouse for selecting options from screen. | |
| Graphics Tablet | Producing technical drawings. | Allows digitising of images with great accuracy. | Expensive unless you use it a lot. | |
| Scanner | Transferring printed images onto a computer. | Cheap and fast method of getting graphics into a computer. | Images take up a lot of storage space. | |
| Digital Camera | Including photographs in newsletters and DTP work. | No film required, no delay getting negatives processed. | Camera can only store a limited number of images, resolution is usually not very good. | |
| Video Capture | Reads still or moving video images into computer. e.g. Video Digitiser, Webcam. | Can capture moving images. | Captured video files require a lot of storage space. | |
| Voice Recognition (Microphone) | Telephone banking, automatic dictation. | Can be operated by inexperience users, can be used remotely by telephone. | Can only understand a few words or one person. | |
| MIDI | Input and output of music via instruments. | Quicker and easier than entering music through computer keyboard. | Instruments and computer require MIDI ports. | |
| Remote Control | Operating a TV from remote location. | More convenient than having to move to TV to operate it. | Can be lost, some controls do not work all functions of device. | |
| Biometric Devices | Security applications where a person must be identified by fingerprint/iris e.g. passport. | More reliable identification than password, signature etc. | People are worried about personal data stored about them being misused. | |
| Sensors | Control systems. | Many types available, automatic input of physical quantities. | May require calibration. | |
| Direct Data Entry (DDE) Devices | ||||
| Input Device | Example Use | Advantage | Disadvantage | |
| Barcodes | Supermarket stock control. | Quick and easy to enter data under non-ideal condition, cheap to print bar-codes. | Only numbers can be stored in bar-codes. | |
| Magentic Ink Character Recognition | Reading information from cheques. | Very fast and secure : numbers can not be changed by overwriting and not damaged by folding. | Expensive to buy reader and ink. | |
| Magnetic Stripe Codes | Used to store a small amount of information on the back of credit cards | Simple and cheap to produce. | Can be damaged by magnetic fields or scratching. | |
| Smart Cards | Petrol station points cards, satellite TV decoder cards, debit cards. | Can store a lot of information. | People worried about what information could be stored. | |
| Optical Mark Recognition | Marking exam scripts, lottery tickets. | Fast and accurate. | Instructions have to be followed exactly by person marking the form. | |
| Optical Character Recognition | Used to read printed text into the computer, reading postcodes to sort letters. | Fast method of reading text into a computer. | Not 100% accurate, OCRed documents must be checked manually. | |
| 5. A turnaround document is a document which :
| 6. | A Portable Data Entry Terminal (PDET) is a handheld computer that can be used to enter data into a computer system as an alternative to a turnaround document. |
Section 5 : Output Devices |
Once an information system has processed the inputs it receives it must present the results of the processing for the user.
An output device takes data from the computer and converts this into information in a form which is normally understandable by humans.
There are many different output devices available. Each output device is suitable for a different purpose. Select an output device from the table below to find out about it or read through the rest of this topic to learn more about all of the different output devices.
| Soft Copy Output Devices | ||
| Monitors / VDUs | ||
| Hard Copy Output Devices | ||
| Printers | Dot Matrix | |
| Laser | ||
| Ink Jet | ||
| Thermal | ||
| Plotters | Flatbed | |
| Drum | ||
| Other Output Devices | ||
| Sound | Speakers | |
| MIDI | ||
| Microfilm (COM) | ||
| Control Devices | ||
Almost all computers have a monitor. Monitors are also known as Visual Display Units (VDUs). Most computers use this display as the main output device. There are two different types of display :
The two most important features of a screen are its size and its resolution. There is more information about these features below. They apply to both desktop monitors and LCDs.
Size : How big is the screen ? Typical sizes are 15", 17" or 21". The size is measured along the diagonal from the bottom left hand corner to the top right hand corner of the screen.
Resolution : An image displayed on the screen is made up of lots of tiny dots called pixels. If you look closely at the screen you may be able to see these pixels. The resolution of the screen is how many pixels there are up and down and from left to right across the screen. A variety of different resolutions are available. For PCs these resolutions have names. e.g. VGA is 640 x 480. This means that there are 640 pixels in each row across the screen and 480 pixels in each column up and down the screen.

The most common current resolutions are XGA (1024 x 768) and SXGA (1280 x 1024). Displays with lots of pixels are called high resolution. Displays with fewer pixels are called low resolution. High resolution displays can show much more detail than low resolution ones and are required for applications such as Computer Aided Design (CAD) and Multimedia. Here are close-up pictures of a circle, one shown on a high resolution display and one on a low resolution display :

Images displayed on the screen are temporary, i.e. they do not last forever. For this reason they are called soft copy.
People often prefer to get printouts of the work they have done rather than to look at it on a monitor. Printouts are called hard copy. Unlike images on a screen hard copy can provide a permanent record of work and can be looked at away from the computer. Hard copy can be obtained using a printer or a plotter. There are lots of different types of printers and plotters available. They vary in the method they use to produce hard copy and the cost and the quality of the hard copy they produce. Different devices are suitable for different applications.
The main types of plotters and printers are listed here :
| Printers | Dot Matrix | |
| Laser | ||
| Ink Jet | ||
| Thermal | ||
| Plotters | Flatbed | |
| Drum |
A dot matrix printer is known as an impact printer because it makes an image on the page by hitting a hammer against a ribbon. Printers which do not do this are known as non-impact printers.
Dot matrix printers are impact printers. They produce an image by hammering a column of 9 or 24 pins against a ribbon. Characters are produced as the print head (which contains the pins) moves across the page.
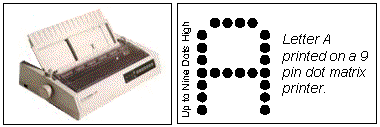
Dot matrix printers are cheap to purchase and have low operating costs. Most can run in either draft mode (quick but very low quality) or Near Letter Quality mode (slower but better quality). If carbon paper is put into the printer then a dot matrix printer can print more than one copy of a document at a time. This feature is often used by companies when they print invoices, bills etc. The company can keep one copy themselves and send the other copy to the customer. Dot matrix printers typically print at speeds around 300 characters per second (cps).
The disadvantages of dot matrix printers are that the output quality is poor, it takes a long time to print a document and the noise can be annoying.
Laser printers are called page printers because they print a whole page at a time. A laser beam is used to draw the image to be printed onto a light sensitive drum. After the image has been drawn on the drum a fine powder ink called toner is put onto it. The toner only sticks where the laser has drawn the image. The paper then passes over the drum and the toner is transferred onto the paper.

Laser printers produce very high quality output, are very quiet and very fast. Typical home laser printers can print 16 pages per minute (ppm). Some industrial versions print over 100ppm and can print on both sides of a piece of paper at the same time. The main disadvantage of this type of printer is the high purchase cost. Small laser printers cost from £80 to buy and are more usually about £600. Colour laser printers cost £500+. Running costs are higher than dot matrix printers but lower than most ink jet printers.
Ink jet printers are the most popular type of printer for use at home or in a small business. This is because they are relatively cheap to purchase and can print in colour. Ink jet printers generate output by squirting tiny jets of ink at the paper to be printed on. A column of ink jets in the print head moves across the page squirting dots onto the paper to make the image.

Typically ink jet printers can produce 1200 to 4800 dots per inch (dpi). Because these dots are made with liquid ink photographs usually look better when printed on an ink jet printer than on a laser printer printer, but the quality of printed text is not quite as good. Ink jet printers nearly always print in colour and cost from £30 upwards. They are slower than laser printers (8 pages per minute+) and cost more to run as the ink cartridges they use are expensive.
Thermal printers are no longer used as printers for microcomputers. They are however still used in some computer control systems, tills and in many fax machines. These printers print on special heat sensitive paper which is relatively expensive. The image is produced from small black dots which are made on the paper by heating it up. The quality is reasonable and graphics can be printed. Documents printed on a thermal printer usually fade over time.
A plotter can be used to produce very large drawings on paper sizes up to A0 (16 times as big as A4). A plotter draws onto the paper using very fine pens. There are two types of plotter. They differ in the way that the pen can be moved about on the piece of paper to draw lines :
Flatbed Plotter : The paper is fixed and the pen moves left and right and up and down across the paper to draw lines.
Drum Plotter : The pen moves up and down on the paper and the paper is moved left and right by rotating a drum on which the paper is placed.

Plotters can automatically change their pens and so can produce colour output. The lines drawn by a plotter are continuous and very accurate. Plotters are very slow but produce high quality output. They are usually used for Computer Aided Design (CAD) and Computer Aided Manufacturing (CAM) applications such as printing out plans for houses or car parts. The quality of the output produced by ink jet printers is now very good and large format (big) ink jet printers are steadily replacing plotters for most tasks.
Sound can be output through loudspeakers or headphones. On microcomputers you also need to install a sound card to be able to output sound. If you want you can connect the computer to a hi-fi to get louder, better quality sound than you would if you plugged the loudspeakers straight into the computer. The sound produced by microcomputers is now better quality than sound that is recorded on a CD.
Sometimes a computer can read out text that has been entered into it by using a computerised or recorded voice. This type of system is known as speech synthesis.
The Musical Instrument Digital Interface (MIDI) system allows a musical instrument to communicate with a computer system. The musical instrument can act as an output or input device. As it is played computer software records information about the duration, pitch and volume of each note.
Music input into a computer by a MIDI instrument can be saved or edited by the user. It can also be printed out as a musical score. The computer can play the recorded piece of music either through its own speakers or through a MIDI instrument that is being used as an output device.
Sophisticated MIDI software can receive inputs from up to sixteen musical instruments at once and can play music back on many instruments simultaneously. The various instruments can all be sequenced together so that they play back in time with each other.
Microfilm is a special type of photographic film which can store images at greatly reduced sizes (about 1/50th of the original size). Traditionally companies that needed to store a lot of documents would photograph the documents and store the images on microfilm. The original documents would then be destroyed and the microfilm photographs of the documents would be kept instead. The microfilm photographs were much smaller than the original documents so they could be stored more efficently and cheaply.
Images stored on microfilm can be viewed using a special reader that magnifies the images and projects them onto a screen. Suitable readers are fairly cheap to buy.
Computers can output information directly to microfilm for long-term storage. This is known as Computer Output on Microfilm (COM).
Microfilm is rarely used today. Documents which need to be stored are usually scanned and saved electronically on high capacity storage media. Documents stored electronically can be indexed and searched more efficiently than documents stored photographically on microfilm.
Computers can also be used to control other devices such as motors and lights which can be switched on and off. These devices are activated by electrical signals sent to them by a computer.
There are lots of different devices available. Examples of common devices include :
| Device | Action Produced | Application |
| Bulb | Lights up an area. | Lighting up a garden when a person walks into the area. |
| Motor | Rotation of a shaft. | Moving a buggy. |
| Buzzer | Makes a short beep noise. | Warning a pilot of a dangerous situation. |
| Pump | Moves gasses or liquids from one place to another. | Keeping a fish tank supplied with oxygen. |
| Heater | Produces heat. | Keeping a house warm in a central heating system. |
| LCD Display | Displays short sequences of numbers or letters. | Information readout on a till. |
The action of many devices will depend upon how high or low the analogue voltage that is sent to the device is. For example :
Devices like these are used by computerised control systems.
Computer Assisted Manufacturing (CAM) systems can control devices such as CNC lathes and robots and use these to make items.
| 1. An output device takes data from the computer and converts this into information in a form which is normally understandable by humans.
| 2. | Soft copy output devices produce temporary output, whereas hard copy output devices produce permanent output.
|
| 3. | There are two types of
Visual Display Unit (VDU). They are desktop monitors
which use a cathode ray tube like a
television and liquid crystal displays. Important factors when selecting a VDU are size,
resolution and cost.
|
| 4. | Printers or
plotters are hard copy output devices. Printers are either
impact printers (produce output by striking a ribbon) or non-impact printers.
|
| 5. | The table below compares the main types of printers and plotters.
|
Abbreviations : PPM = pages per minute, CPS = characters per second
| 6. | Speakers
can produce sound output such as music or synthesised speech.
|
| 7. | MIDI
instruments can be controlled by a computer. Music can be played back through up to 16 instruments simultaneously.
|
| 8. |
Microfilm is a special type of photographic film which can store images at greatly reduced sizes (about 1/50th of the original size). In the past documents were stored on microfilm but it is rarely used now.
|
| 9. | MIDI
instruments can be controlled by a computer. Music can be played back through up to 16 instruments simultaneously.
|
| 10. | A wide variety of
control devices such as motors, lights and pumps can be
switched on and off by a computer.
| | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Section 6 : Storage Devices |
All information systems need to store data. This may be done temporarily whilst inputs are processed to produce outputs or for much longer periods of time.
For example :
A computerised information system must be able to store both programs (e.g. a word processing package) and data (e.g. a word processed letter).
A storage device stores programs and data either temporarily or permanently. All information systems contain two different types of storage :
| Immediate Access Store (IAS) | Immediate access store holds programs and data that the user is currently working with. | |
| Backing Store | Backing store keeps data and programs when the computer is turned off. |
Immediate access store is also known as main store or primary store. Backing store is also known as secondary store.
The capacity (amount of data) that a storage device can hold varies significantly between different devices. Units such as bytes, kilobytes and megabytes are used to describe a storage device's capacity. Other factors such as speed of data access, cost and portability will also determine which storage device is the most appropriate one to use for a particular application.
Select a storage device from the table below to find out about it or read through the rest of this topic to learn more about all of the different storage devices.
| Immediate Access Store | |||
| RAM | |||
| ROM | |||
| Backing Store | |||
| Magnetic Disks | Floppy Disk | ||
| Hard Disk | |||
| Zip Disk | |||
| Jaz Disk | |||
| Optical Disks | CD-ROM | ||
| CD-R | |||
| CD-RW | |||
| DVD-ROM | |||
| DVD-RAM | |||
| Magnetic Tape | |||
| Flash Memory Devices | |||
Various units of measurement exist to describe the capacity of storage devices. The smallest unit of storage is the bit. A computer can only store data as binary numbers (0s and 1s). A bit of storage can hold either a 0 or a 1. Devices such as computers which can only use binary information are described as digital devices.
Eight bits are grouped together to form a byte. Using 8 bits it is possible to represent any character on the keyboard with a byte. The characters are represented in 0s and 1s using a code called the ASCII code. Here are some example codes :
| Character | ASCII Code |
| A | 01000001 |
| B | 01000010 |
To store the sentence "Hello World" in a computer would require 11 bytes (one for each character), which is 11*8 = 88 bits.
Describing the capacity of a storage device in bytes would be silly. A typical home microcomputer can store 536870912 bytes in its immediate access store and 128849018880 bytes in its main backing store (probably a hard disk). Therefore there are a number of other related units that are used :
| Unit | Equivalent To |
| 1 Bit | A single storage location which can hold either a 0 or a 1. |
| 1 Byte | 8 Bits |
| 1 Kilobyte (Kb) | 1024 Bytes |
| 1 Megabyte (Mb) | 1024 Kilobytes |
| 1 Gigabyte (Gb) | 1024 Megabytes |
Typical Storage Capacity of a Microcomputer
A typical new home microcomputer has 512Mb of immediate access store. This is equivalent to :
The same computer is likely to have three backing storage devices, a floppy disk drive (capacity 1.44Mb), a CD/DVD drive (capacity 650Mb-18Gb) and a hard disk drive (capacity 120Gb+).
Immediate Access Store ( IAS ) holds programs and data that the user is currently working with. For example :
There are two different types of IAS :
Read Only Memory (ROM) : The contents of ROM is permanent. It can not be altered by the user. The content is written onto the ROM when it is first made. ROM keeps its contents even when the computer is turned off and so is known as non-volatile memory. On some computers a special piece of software called the BIOS which is used to configure the computer is stored in ROM. ROM is also often used in embedded systems where a small built-in computer is used to control a device such as a washing machine. The program that controls the machine is stored on ROM.
Random Access Memory ( RAM ) : RAM is used to store programs and data that are being used by the computer. When the computer is turned on the RAM is empty. Data and programs can be put into RAM from either an input device or backing store. The data in RAM is lost when the computer is turned off so it is known as volatile memory. To keep data the user must save it to backing store before the computer is turned off.
It is easy to add extra RAM to a microcomputer by inserting extra RAM cards called SIMM or DIMM cards :

IAS is located inside the computer. Data can be written to and read from IAS electronically at very high speeds, much faster that it can be written to or from backing store. IAS is much more expensive to buy per Mb than backing store is.
If data needs to be kept whilst a computer is turned off then it must be stored on backing store. Any programs or data that are not currently being used by a computer will be kept on backing store. When programs or data are used they are copied (loaded) into immediate access store for faster access.
Information stored on backing store is placed on a storage medium. The most common media which are used for backing store are :
Magnetic Disks
Magnetic Tapes
Optical Disks such as CD-ROMs and DVDs
Flash Memory Devices
The data is read from or written to the storage medium by a piece of hardware known as a drive or a storage device.
It takes much longer to access data which is on backing store than data which is in immediate access store, typically 100 to 1000 times as long. This is because most backing storage devices operate mechanically. Computers have much more backing store than immediate access store for two reasons :
IAS only needs to store programs and data that are currently being used whereas the backing store needs to hold all of the programs and data that can be used on the computer.
Backing store is much cheaper per Mb than IAS.
Programs and data can not be used directly from backing store. They must be copied (loaded) into immediate access store before they can be used. Any data which needs to be kept must be transferred back to the backing store from the immediate access store before the computer is switched off. This is called saving.
Sometimes data is compressed before it is stored. Compressing data reduces the storage space that a file uses without losing any of its contents.
Magnetic disks are the most common backing storage device. Data is stored using magnetised spots called domains on the disk. Each domain can store one bit of data (a 0 or a 1). A 3.5" 1.44Mb floppy disk used on a PC contains 16,777,216 such spots. A 3.5" 120Gb hard disk drive contains over 120 billion spots!
Data stored on disks is arranged along a series of concentric rings called tracks. Each track is divided up into a number of sectors. Data is read to and written from a disk one sector at a time. A sector usually contains 512 or 1024 bytes of data.
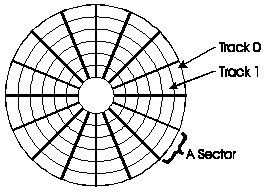
The process of dividing a disk up into tracks and sectors so it can be used on a computer is known as formatting. You must format a new disk before you can use it.
Data is read from the disk using a disk head which moves mechanically about the disk (rather like a record player tone arm). The disk head can move directly to any sector on the disk. Because of this a computer system can load a file or a record from a file very quickly. The system can move directly to the location of the record/file and read it without having to read any other data from the disk. This is known as direct access. For most applications using a direct access medium is much faster than using a serial access medium.
The two main types of magnetic disks are floppy disks and hard disks.
Floppy disks are magnetic disks. They are portable (can be moved between computers) but have a small storage capacity. Reading and writing data from a floppy disk is very slow. The most common type of floppy disk is the 3.5" disk that can store 1.44Mb of data when it is used on a PC. Older disks were 5.25" or 8" in size but could store much less data.
A floppy disk is manufactured from a flexible plastic disk. This disk is coated with a magnetisable material. For protection the disk is encased in a plastic shell. All sizes of floppy disk have a write protect tab built into the shell. If this tab is set then data can be read from the disk but not written to it. The write protect tab can be used as a security measure to prevent important data being deleted or changed accidentally.
Floppy disks are used for three main purposes :
| Transferring Information | Files can be transferred from one computer to another using a floppy disk. This is possible because floppy disks are portable. Unfortunately the small storage capacity of a floppy disk means that large files can not easily be transferred this way. |
| Backups | Floppy disks can be used to make extra copies (backups) of files that are stored on a computer's hard disk. If the copy of a file on the hard disk is lost or corrupted than the backup copy can be used instead so the file is not lost. Increasingly other media such as magnetic tapes or optical disks are being used instead of floppy disks to store backup files. This is because they are faster at reading and writing data and have much greater storage capacities. |
| Distributing Software | Software can be distributed (sold) on floppy disks. A package may be supplied on up to thirty floppy disks. CD-ROMs are now a more common medium for distributing software because an entire package can be stored on one CD-ROM and a CD-ROM is less vulnerable to physical damage. |
Some hardware companies now produce storage devices which are very similar to floppy disks but can store 100Mb or even 750Mb of data. These devices are also much faster than standard floppy disk drives. An example is the Zip disk.
Hard disks are magentic disks. They have much larger storage capacities than floppy disks. Data can be transferred to and from a hard disk much more quickly than from a floppy disk. Hard disks are usually fixed inside a computer and can not be moved between different machines. Some expensive hard disks can be moved between computers. These are called exchangeable hard drives. An example of this is the Jaz drive.
A hard disk is made of a rigid disk which is coated with a magnetisable material. The magnetic material used is of a much higher quality than that found on floppy disks. Hard disks spin much more quickly than floppy disks and the disk head is positioned very close to the disk (thousandths of a millimetre away). Because the disk head is positioned so close to the disk hard drives can easily be damaged by dust or vibration. Therefore the disk, the drive head and all the electronics needed to operate the drive are built together into a sealed unit. This picture shows a hard disk drive with the case removed.

Usually (as in the picture above) several physical disks are contained in one hard disk unit. Each disk is known as a platter. Typical hard disk capacities for a home PC now start at 80Gb and units storing up to 300Gb are available. If larger storage capacities are required then multiple hard drives can be combined. Using appropriate hardware or software many hard disks can be made to look like one very large hard disc to the user.
Zip and Jaz disks are examples of removable magnetic disks. They can be used to transfer data from one computer to another, to backup data, or as an alternative to a hard disk for storing files.
| Comparison | Zip | Jaz | ||||||
Capacity
| 100Mb, 250Mb and 750Mb
| 2Gb (2048Mb)
| Type
| Removable Floppy
| Removable Hard
| Available
| Yes
| No Longer Made
| |
Optical disks store data by changing the reflective properties of a plastic disk. Binary computer data (0s and 1s) are represented by the way the disk reflects light when a low power laser is shone at it. A 0 stored on a disk reflects light differently to a 1 stored on a disk.
Like floppy disks, optical disks can be moved from one computer to another. They have much larger storage capacities than floppy disks but can not store as much data as a hard disk. Data can be read from an optical disk more quickly than from a floppy disk but hard disks are much quicker. As with a hard disk the drive head in an optical drive can move directly to any file on the disk so optical disks are direct access.
There are five types of optical disks that are currently in use. They are all the same physical size. It is possible to purchase a Combo drive that can read and write most of these different types of disks.
The five types of optical disk are :
CD-ROM (Compact Disk - Read Only Memory)
This is by far the most widely used type of optical disk. A CD-ROM disk can store up to 800Mb of data. The data is written onto the CD-ROM disk before it is sold and can not be changed by the user. Because of this CD-ROMs are often described as Write Once Read Many times (WORM) disks. CD-ROMs are used for applications such as distributing software, digital videos or multimedia products.CD-R (Compact Disc - Recordable)
A CD-R disk can store up to 800Mb of data. A CD-R disk is blank when it is supplied. The user can write data to it just once. After data has been written to the disk it can not be changed. A special CD-R drive is required to write to the disk. CD-Rs are often used for making permanent backups of data and distributing software when only a small number of copies are required.CD-RW (Compact Disc - Rewriteable)
A CD-RW disk can store up to 800Mb of data. CD-RW disks can be read from and written to just like a hard disk. CD-RWs can be used for any application that a hard disk can be used for but the time taken to access data is much longer than that for a hard disk.DVD-ROM (Digital Versatile Disk - Read Only Memory)
DVD is the new standard for optical disks. By using a shorter wavelength laser, storing data on both sides of the disk and having more than one layer of data on each side of a disk DVD disks are able to store much more data than CD disks. The DVD standard includes disk capacities up to 18Gb. Current DVD disks store far less than this. DVD-ROM disks can be read from but can not be written to.Because of their high capacity, DVD-ROM disks are used to store high quality video such as complete movies. Often extra data such as information about the making of the film or the actors and actresses who star in it are also stored on the disk. Unlike movies recorded on video tape, DVD-ROM movies can be interactive. The user can make selections on the screen and change what they see.
DVD-RAM (Digital Versatile Disk - Random Access Memory)
DVD-RAM disks have all of the benefits of DVD-ROM disks and can be written to as well. These very high capacity disks are ideal for producing backups. They are starting to replace video tapes for recording television programmes. DVD-RAM disks typically store about 5Gb of data.
Magnetic tape comes in two different forms :
| Reels | Large reels of tape (1/2 inch wide and 2400 feet long) which must be loaded into a reel-to-reel tape drive. This type of tape is usually used by mainframe computers. |
| Cartridges | The tape is supplied in a small cartridge rather like a music tape. The tape is typically 1/4 inch wide and 300 feet long. This type of tape is used on PCs (microcomputers) and the device used to read/write the tapes is called a tape streamer. The picture below is of a tape streamer for a PC. Capacities of cartridges vary from 20Gb to 1400Gb. |
The storage capacities of tape cartridges are now so great that reels of tape are not used in new computer systems.

A computer tape is divided up into many blocks. A block on a tape is like a sector on a disk. To read data from a particular block on the tape all of the blocks that come before it must be read first. This means that finding a particular file/record on a tape can take much longer than finding a particular file/record on a disk. However once the file or record has been located it can be read more quickly from a tape than in could be from a hard disk. Having to read through all of the files/records that are stored before the file/record you want to access is known as serial access.
Often files or records are stored on a tape in a particular order (e.g. sorted alphabetically by a key field). If this is the case then the tape is described as having sequential access. Because locating data on a tape takes a long time, magnetic tapes are not used as general purpose storage devices. They are only useful for a few applications. The two main applications tape is used for are :
| Applications for Magnetic Tapes | ||
| Backup | Often a tape streamer is used to make copies of data stored on a hard disk in case the data becomes corrupted. If this happens then the correct data can be restored from the tape. A backup copy of the contents of the hard disk could be made once every week. Tapes are more suitable for making backups than floppy disks or CD-ROMs. This is because the entire contents of a hard disk can be written onto one tape, producing the backup will be much quicker and tapes are cheaper to buy. It does not matter that tapes are serial access because when a backup is made or restored every file on the tape has to be accessed. | |
| Batch Processing | In a batch processing system when processing occurs the whole master file and the whole transaction file are read to produce a new master file. Because the master file and transaction file are both sorted into the same order the data can be read sequentially from each file. A batch processing system does not have to move backwards and forwards through a tape looking for records. The system is designed so that the next record to be read is stored immediately after the current record on the tape. Therefore using a serial access medium instead of a direct access medium will not slow down processing. Tapes are preferred to disks in batch processing systems due to their relative low costs and fast read/write speeds. | |
Flash Memory devices store data electronically in a type of memory that can have data written to it and (unlike RAM) can retain the data when the power to the memory is turned off. Commonly flash memory devices store data in Flash Erasable Programmable Read Only Memory (FEPROM).
Several different types of flash memory device are available. These include Compact Flash, SmartMedia, Secure Digital and USB Pen Drives.
Flash memory devices are very compact, most being a similar size to a postage stamp or coin. For this reason they are often used as backing storage in small devices such as digital cameras and PDAs. Typical storage capacities are from 32Mb up to about 2Gb. The cost per Mb of flash memory storage is high compared to other backing storage devices.
Accessing data stored permanently in backing store is much slower than accessing data in RAM. A common technique that is used to speed up access to data on backing storage devices is caching.
A cache is a part of a computer's RAM that is set aside to store copies of frequently used sectors on a backing storage device such as a hard disk drive. As files are accessed from the hard disk the computer will determine which sectors of the disk are being used most frequently. Copies of the data that is located in these sectors are transferred into the cache.
After this whenever the data in these sectors is read or changed the computer will use the copies of the sectors in the cache rather than the original sectors on the disk. Since the cache is located in RAM these accesses will be many times quicker, so the operation of the computer system will be speeded up.
The contents of the cache are lost when the computer is turned off. This is because cache is located in RAM which is volatile. To ensure that any changes made to sectors in the cache are saved permanently to the hard disk drive the computer system will copy these sectors back to the hard disk drive at a time when the drive is not being used or when the computer is properly shut down.
There are three different methods which can be used to access (locate) data stored on a backing storage device. They are direct access, serial access and sequential access.
Direct Access
When direct access is used the head that reads data from the storage medium can move directly to any point on the storage medium. If a particular record or file must be loaded or saved then the head can move directly to the record/file's position on the storage medium and read the data. Records and files can therefore be located very quickly.
Magnetic disks such as hard disks and floppy disks and optical disks such as CD-ROMs use the direct access method. Direct Access is required if transaction processing is taking place.
Serial Access
When a serial access medium is being used, the head that reads data from the storage medium has limited freedom of movement. The only serial access medium is magnetic tape.
To read a particular record/file from a serial access medium, all of the data that comes before the record/file must be scanned through. The tape head can not move to a particular record/file on the tape without reading through all of the other records that come before it.
Because of this it can take a very long time to locate a record/file on a tape and so tapes are only used for specific applications such as backup and batch processing. For these applications the speed of locating data is not important and the other advantages of magnetic tapes outweigh the slow access speed.
Sequential Access
Sequential access is a slight modification of the serial access method. This method is identical to serial access except that the records are stored on the storage medium in a particular order, e.g. by customer number. Sorting the data into an order may speed up operations such as searching the tape. The sequential access method is usually used by batch processing systems.
When data is stored it occupies space on a storage device such as a hard disk or floppy disk. Buying storage space costs money. To reduce the cost of storing data users often attempt to reduce the size of the files they want to store without losing any of the data.
Data compression is the act of reducing the size of a file without losing any of the data it contains. Decompression (also known as uncompression or expansion) is the act of taking a compressed file and converting it back to its original size and format. Because compression alters the format of the data in a file a compressed file must be decompressed before it can be used.
How much a file can be compressed by will depend upon the method being used to compress the file and the data that is stored in the file.
The three most common applications for which data compression is used are :
Distributing Software
Software is often distributed on CD-ROMs. The software must be installed onto a hard disk before it can be used. Software manufacturers usually compress the files that make up a package on the CD-ROM. When the software is installed onto a hard disk the files are decompressed by the installation software.
| Advantages | Because the software is compressed it is possible to fit extra data onto the CD such as help and tutorial information or demos of other programs. |
| Disadvantages | Because the software is compressed it can not be run directly off the CD-ROM. It must be installed first. |
Hard Disk Compression
Files stored on hard disks can also be compressed. Some utilites will compress and decompress individual files whilst others can compress an entire hard disk automatically as files are saved and loaded.
| Advantages | Files take up less space so you can store more files on a hard disk. |
| If a file takes up less space to save then the cost of storing the file is reduced. | |
| Disadvantages | You must buy a compression program to compress or decompress files. | The compression program will use up some of the computer's memory, leaving less available for other programs. |
Compressed files may load more quickly or more slowly than files that are not compressed. This will depend upon how well compressed a file is and the speed of different components of your computer hardware.
Data Transmission
Compression is also used when data is transmitted over a telephone line. Modems will only allow the transmission of data at very slow speeds (e.g. 3Kb per second). To transmit a picture the size of an A4 page can take over ten minutes. If data that is to be transmitted can be compressed before it is sent then there can be considerable advantages :
| Advantages | Faster transmission time. |
| Reduced transmission costs. | |
| Disadvantages | Compression can only be used if both the transmitting and receiving modems support the same compression procedure. |
There are a variety of agreed standards for compressing data that is sent over telephone lines. Some modem manufacturers claim compression ratios of 1:4 (i.e. data can be reduced to a quarter of its original size before being transmitted). Such high compression rates are rarely achieved.
Two common methods of processing saved files are sorting and merging. These are often used by batch processing systems which store data as records in files. For example a file might contain records about people who are employed by a company. There would be one record per employee.
Sorting
Sorting is arranging the records in a file into a particular order, such as by employee number.
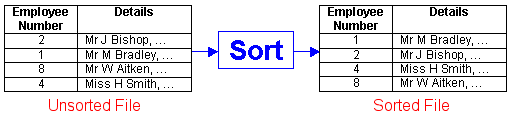
Merging
Merging is combining the contents of two files into one file. The simplest method of merging two files together is to just take the contents of one file and add them to the end of the other. This is known as appending :
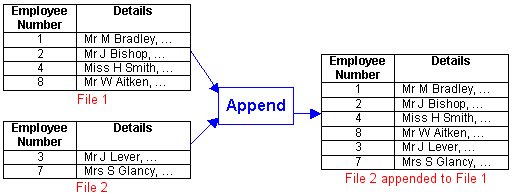
If the records in a file must be kept in a particular order (a sequential file) then the merge process is more complex. To carry out a merge the algorithm shown in this flowchart must be followed :
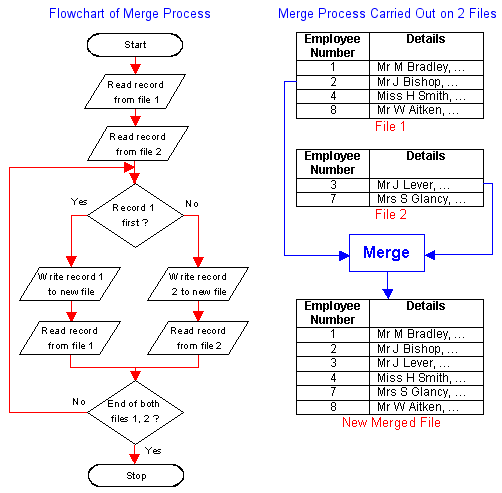
The results of the merge are also shown in the above diagram. Note that unlike a simple append, this more sophisticated merge has produced a new file that maintains the required order. The records in two files that are to be merged must have the same record structure.
1. | Computerised
information systems have to store
programs and data.
|
| 2. | A storage device stores programs and data either temporarily or permanently.
| 3. | The capacity of a storage device is described in terms of bits, bytes, kilobytes, megabytes and gigabytes.
| 4. | There are two different types of storage device :
|
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Section 7 : Processing |
Processing is the act of doing something (e.g. organising and manipulating) with data to produce output. Processing is at the centre of our model of an information system :

There are three distinct methods of processing data : batch, transaction and real-time processing. In a computerised information system most of the processing is carried out by a hardware device known as a microprocessor.
The microprocessor is the hardware device that processes data. The microprocessor contains electronic circuitry which can :
Most personal computers (known as microcomputers) contain just one microprocessor. Minicomputers and mainframe computers may contain many microprocessors. All of the microprocessors that are contained in one computer are known as the computer's Central Processing Unit or C.P.U. A computer that contains more than one microprocessor is able to carry out more than one task at the same time and is described as being capable of parallel processing.
Using batch processing input data is grouped together into batches . No data is processed until a complete batch has been collected. Then all of the data in a batch is processed in one go. There may be a long time delay between data being input into the system and the data being processed.
In this type of system the important data that the computer stores all of the time is kept in a file called the master file. The data in the master file is sorted into order using one of the fields in the records in the file, known as the primary key field. The primary key field must uniquely identify each record in the file.
Each piece of input data (which will update the contents of the master file) is known as a transaction. All the input data is put together into a batch in a file called the transaction file. There are three different types of transaction that any processing system will have to cope with. They are :
At some predetermined time (e.g. the end of the day or week) the computer system will process the data stored in the transaction file and make any changes that are necessary to the master file as a result of the transactions. This will produce an updated master file and an error report detailing any transactions that could not be processed for some reason. Generating a single updated master file from the old master file and the transaction file is known as merging files.
Before this processing can take place the transactions must be prepared for processing. To do this two operations must be carried out :
Validating : Each transaction that is entered is validated to check that it is unlikely to halt processing by causing an error. It is very important that processing is not halted in a batch processing system because processing often takes place overnight without a human operator being present. If an invalid transaction caused the processing to stop then a whole night's processing time could be lost. Transactions are usually validated as they are keyed in by the operator. Any errors that are found can be reported and corrected straight away.
Sorting : The data in the transaction file is sorted into order using the same primary key field as the master file. Sorting can not take place until the whole batch of transactions entered and stored in a file. The transaction and master files need to be put into the same order before processing occurs because the two files are processed sequentially. The files are usually stored on a serial access medium such as magnetic tapes. If the records on the tapes were not sorted into order then whenever a transaction record was read from the transaction file the computer system would have to waste a lot of time searching for the matching record in the master file.
How often batches of data are processed will depend upon the application (i.e. the job that is being done). Batch processing is usually only carried out on mainframe computers and when very large volumes of data have to be processed in a database.
| Advantages of Batch Processing | Disadvantages of Batch Processing |
| For large systems the hardware required to implement a batch processing system can often be cheaper than that required to implement a transaction or real-time system to do the same job. | The master file is not always kept up to date. This makes batch processing unsuitable for some applications. e.g. booking seats on an aeroplane where the data must be kept constantly up to date. |
| Batch processing can be carried out automatically at a time when the computer system would not normally be used, e.g. overnight. By doing this a company can get more work out of the computer hardware it owns. | There is always a delay before work is processed and output is obtained |
This system flowchart shows what happens in a batch processing system :
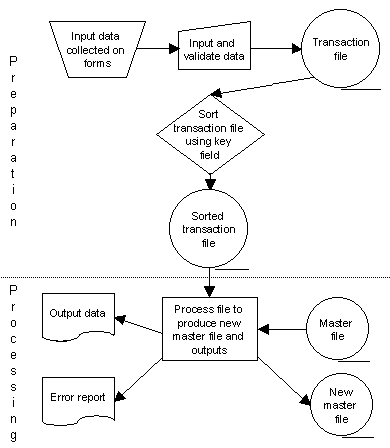
Batch Processing Algorithm
During the processing phase (represented in the bottom half of the flowchart above) all of the records are copied from the master file to the new master file. Any changes that must be made to the master file are detailed in the transaction file and carried out when the records are copied to the new master file. The processing that takes place for each transaction in the transaction file will depend upon the type of transaction :
| Transaction Type | Processing |
| Add new record | Use details in transaction file record to insert a new record into the new master file at the correct position in the file. |
| Delete record | Do not copy the record that is to be deleted from the master file to the new master file. |
| Update record | Use details in transaction file record to update the record read from the master file then write the new record to the new master file. |
There is nothing to stop a batch processing system being implemented using disks for storage rather than magnetic tapes. Tapes are usually used because they are cheaper to purchase, can store more data and can read and write data faster than disks.
Payroll systems are often implemented using batch processing :
The master file would contain the records for all of a company's employees, including their employee number, rates of pay and how much they have been paid so far this year. The records in the master file would be sorted using the employee number as the primary key field.
Here is an example record for an employee called Anna Jones in a master file together with an entry in the transaction file which will update her record with the number of hours she has worked this week.

After the transaction file was processed, Anna's record in the master file would show that her pay so far this year was £5762.50. This would include the £187.50 (25 hours at £7.50) she had just earned.
The transaction file would be processed at the end of each week as workers are paid weekly. Before processing it would have to be sorted into the same order as the master file, i.e. the records would be sorted into order by employee number.
The computer would then process the transactions, using the information about how many hours each employee has worked this week (from the transaction file) and their rates of pay (from the master file) to calculate the employee's wages for the week. Payslips can then be printed and the master file can be updated to increase the amount paid so far this year by the wages paid this week. An error report will also be produced.
This system flowchart shows the operation of the payroll system :

For some applications the master file needs to be kept up to date all of the time. For example in a travel agents whenever a seat is booked on a flight the number of seats that remain available on the flight must be reduced by one immediately. If this update was not done until the end of a day (as might happen in a batch processing system) then the flight could become overbooked with the same seat being booked more than once.
Transaction processing systems are used whenever the master file must be kept up to date. A transaction processing system operates like this :
When a transaction is entered it is placed in a queue of transactions waiting to be carried out. The transactions are processed in the order that they are placed into the queue. If there are many people using the system at the same time then there could be lots of transactions being made from different computer terminals.
Under normal circumstances a well designed transaction processing systems will process a transaction within a few seconds of the transaction being inputted. During peak processing times (e.g. Saturday morning in a travel company) the time that it takes for a transaction to be processed will increase. For most systems this is acceptable. When it is not acceptable, a real time processing system must be used instead.
Transaction processing systems need to use direct access files. In a direct access file any record in the file can be updated directly, without having to read through all of the records that come before it in the file. Serial access media such as magnetic tape can not be used. The time required to find the record in the master file that a transaction related to would make processing incredibly slow.
Transaction processing is interactive, i.e. processing takes place as a "conversation" between the user and the computer : The computer responds to the user’s input by outputting some data before the user can input any more data. This means that the user's input can depend on the computer's previous output.
Transaction Processing is also known as Interactive, On-Line or Pseudo Real Time Processing.
A supermarket uses a Point of Sale (POS) terminal to keep track of the goods that it has in stock and to produce bills for customers. Whenever an item is sold the product code of the item is read into a till by a barcode scanner. Sometimes the barcode is not scanned properly. If this happens the product code must be rescanned or entered using a keyboard.
Once the product code has been entered the till looks up the price and name of the product in the supermarket's stock database. This information is printed on the customer's receipt. It also updates the product's record in the stock file to indicate that the product has been sold.
This system can be depicted by this system flowchart :

The system has to be a transaction processing system because a customer at a till would not be prepared to wait for a batch processing system to look up the price and name of the product. It is not worth spending a lot more money to purchase a real time system to carry out this task because small delays at peak times can be tolerated.
For some tasks a computer must process information to meet some real world time deadline. The time deadline must be met regardless of how much work the computer has to do. Usually real time computer systems are required to process information very quickly. Most real time systems appear to process data instantly.
A computer system which must process data extremely quickly to meet a real world deadline is known as a real time system.
For example, consider a control system that is used to fly a guided missile to hit a target. Once the missile is launched the control system must guide it to its target. The missile's guidance system identifies its position by examining the contours / features of the ground it is flying over. This input data is used to ensure that the missile follows the path it has been programmed with. Using the inputs the system will decide how to move ailerons/fins to change direction and control the speed of the rocket motor.
Because a missile flies very fast the inputs must be processed very quickly to affect the outputs. If it took two seconds for the missile to change its direction to avoid an unexpected object then the missile would probably hit the object before the change of direction could take place. The data must be processed in thousandths of a second to avoid a disaster. There is a real world time limit on how long the computer system can take to process data without having terrible consequences. Therefore a missile control system has to be a real time system.
Most real time systems are control systems. Other examples include the cooling system in a nuclear reactor which prevents the reactor overheating or any system which must control a dangerous chemical reaction.
Real time systems are very fast but they do not process data instantly. Any processing will take some time. However real time systems will process data very quickly. To ensure that any input data can be processed sufficiently quickly real time systems must incorporate a lot of redundancy. This means having much more hardware than is required to process the expected amount of input data. The extra hardware is known as redundant hardware because it is not normally used. Under normal circumstances only a small fraction of the hardware is required. In extreme circumstances when there is an unusually large amount of input data to process the redundant hardware can be used. Therefore the system will not slow down and will still be capable of meeting deadlines.
Redundant hardware can also be used as backup hardware to reduce the likelihood of a computer system failing if some of its hardware fails.
Having to incorporate lots of redundant hardware makes real time systems very expensive. They are usually only used in safety critical situations.
| Advantage of Real-time Systems | Disadvantage of Real-time Systems |
| If real-time systems were not available then certain tasks e.g. missile guidance would be impossible. | Real-time systems are very expensive to produce and require lots of development time and backup hardware (redundancy). |
| 1. Processing is the act of doing something (e.g. organising and manipulating) with data to produce output.
| 2. | Processing is carried out by a microprocessor.
Microcomputers usually contain one microproccesor. Minicomputers and mainframe computers
may contain more microprocessors. Together all of the microprocessors in a computer are
known as the Central Processing Unit (CPU).
|
| 3. | There are three different types of processing. They are
batch, transaction and
real time.
|
| 4. | This table compares the different types of processing.
| |
| Comparison of Processing Methods | |||
| Comparison | Batch | Transaction | Real Time |
| Identifying Features | Input data is collected into batches in a transaction file which is sorted and validated before being processed with the old master file to produce a new master file. | The master file is always kept up to date. Transactions are placed in a transaction queue and processed in the order that they are added to the queue. | Data is processed extremely quickly to meet a real world deadline. |
| Example Applications | 1. Payroll 2. Printing Bills 3. Multiple Choice Exams | 1. Ticket Booking 2. Seat Booking 3. Stock Control 4. Banking | 1. Missile Guidance 2. Nuclear Reactors 3. Chemical Processes |
| Speed of Response | No data is processed until a complete batch is collected. It may be a long time e.g. a day before data is processed. | Under normal loads data is processed within a few seconds. Under heavy loads processing times can be longer. | Data processed very quickly to meet a real world deadline. Processing often appears to be instant. |
| Storage Media Used | A serial access medium such as magnetic tape. | A direct access medium such as magentic disk. | Usually immediate access store. |
| Cost | |||
Section 8 : Software |
A piece of software is a computer program which has been written to carry out a particular task. Without software the hardware that is used to build a computer system would not be very useful. A software program contains the instructions that the computer must follow to carry out a task. Sometimes more than one program is required to complete a task. When this is the case the group of programs which together complete the task are known as a software package.
Software programs are originally produced by computer programmers who will write the instructions that form the program in a programming language.
Example pieces of software are :
A piece of software is usually classified as being either systems software or applications software.
A piece of software is usually classified as being either systems software or applications software.
Systems Software
Systems software controls the operation of a computer. Without systems software a computer would not function. The most important piece of systems software is the operating system. The operating system will perform vital tasks such as :
Other pieces of system software will perform less essential tasks such as backing up files. These programs are known as utilities. Example utility programs are :
Applications Software
Applications software is software that is written to solve a particular problem or carry out a particular job. Application software can be either generic or application specific.
(1) Generic (General Purpose) Software
A generic software package is a package that can be put to a wide variety of uses. For example a spreadsheet package can be used for any task involving calculations or graph plotting. The most common generic software packages are :
| Word Processor | Used to produce simple documents such as letters and essays. | |
| Desktop Publisher | Used to produce complicated documents such as leaflets, posters and newspapers. | |
| Graphics Package | Used to produce pictures and diagrams. | |
| Database | Used to store information so that it can be easily searched. | |
| Spreadsheet | Used to perform calculations and draw graphs. |
Some generic packages are described as being integrated packages. This means that they incorporate more than one program. For example an integrated package may include a word processor, spreadsheet and database. The individual programs in an integrated package are designed to work well with each other. Information can easily be transferred between each program. Additionally the user interface of each program will be similar so that if you have learnt how to use one program it will be relatively easy to learn how to use another.
(2) Application Specific Software
An application specific package is produced to perform one specific task. For example a program that was written to produce invoices and manage stock levels for a garage would be application specific software.
If you have a task to carry out on a computer you will need to choose the most appropriate software to use for the task. For example, is a spreadsheet or a database more suitable for keeping records of all of the members of a club ? Factors such as ease-of-use, speed, availability of software, your familiarity with the software, staff training, and the features of a software package will influence your choice.
The three important points you must cover when selecting software are :
If you have to select software for a project then one possible way of writing up your software selection is to draw up a table like this example.
Sometimes there is no software package available which will let you carry out the task properly. If this is the case then you must develop a completely new system.
In this example a student has to select an appropriate package to write up a science experiment. The write up must include text, a table of results and a graph showing the results.
Having considered the task I have identified a number of different activities that I will need to carry out to write the essay. I have also identified some other activities that would help me write the essay but are not essential. In order of importance these activities are :
I have considered two possible methods of producing the essay. They are (i) using Microsoft® Notepad and (ii) using Microsoft® Works™. Both of these methods are available for me to use. In the table below I have explained how each of the activities can be carried out using each of the methods.
| Activity | Microsoft® Notepad | Microsoft® Works™ |
| Enter and Output Ordinary Text | Text is typed onto the screen. It can be output by selecting Print from the File menu. | Text is typed onto the screen. It can be output by selecting Print from the File menu. |
| Produce Neat Tables | Entries in tables can be lined up neatly using the TAB key. | Tables can be created by Selecting Insert Table from the Insert Menu. Entries are automatically aligned. Borders can be put around the table to improve its presentation. Rows and columns can be easily added or deleted. |
| Draw Graphs | There is no facility to produce a graph. | Works includes a spreadsheet which can be used to produce graphs. They can be cut and pasted into the word processor. |
| Correct Errors | Errors can be corrected before printing by deleting the incorrect text using the DELETE key. Extra information can be added at any point in the document. | Errors can be corrected before printing by deleting the incorrect text using the DELETE key. Extra information can be added at any point in the document. |
| Check Spelling | The essay will have to be read on-screen and any difficult words looked up in the dictionary. If there are any mistakes they can be corrected before the essay is printed. | Spellings can be checked automatically using the Spell Check option. This will identify most mistakes and can suggest the correct spellings. |
| Use Different Styles for Headings | The font can not be altered. Titles can be highlighted by double spacing letters or typing in capitals. | The font and font size can be changed for headings. They can be underlined or made bold to make them stand out more. |
| Number the pages. | The page numbers will have to be typed manually at the bottom of each page. | Page numbers can be included in the footer and will appear on each page. The software works out the number of each page. |
| My Familiarity with the Method | I have used Notepad to edit text files on my PC. | I have previously typed a number of small articles on Microsoft Works. |
The best option is to use Microsoft Works. It will allow me to carry out all the tasks I want to. I can correct my text on screen before printing and Works will help me find my spelling mistakes - saving a lot of time. Tables can be easily created and edited in a range of attractive styles. The spreadsheet can be used to incorporate a graph. A number of different fonts can be used to make titles stand out. Works will also automatically number my pages for me.
Microsoft® Notepad and Microsoft® Works™ are trademarks and/or registered trademarks of Microsoft Corporation in the United States and other countries.
Usually if you want your computer to perform a particular job then you can go to a shop and purchase a software package that will do that job. Software packages that are readily available from shops are known as "off-the-shelf" packages.
Sometimes more than one package will be available which could perform the job you need to do. If this is the case then you will need to look at the features of the different packages to select the most appropriate package.
If no package exists that will do the job you need then there are two options available to you :
| Customise a Generic Software Package | Sometimes a generic package such as a database can be customised (modified) to carry out the job you want. For example a database could be customised to act as a rentals system for a video shop. |
| Custom Written Software | A computer programmer could produce a completely new program in a programming language to do exactly what you want it to. This option is usually very expensive as much more work is required to write a new piece of software from scratch than to customise a generic software package. It will also take longer to produce a system this way. However the resulting system will do exactly what you want it to. This may not be possible when a generic package is customised. |
1. | A piece of
software is a computer
program which has been written to carry out a particular task.
|
| 2. | Software programs are originally produced in a programming language.
| 3. | Software is usually
classified as being either
systems software or
application software.
| 4. | Systems software controls the operation
of a computer. The operating system and utility programs are systems software.
|
| 5. | Application software is software that is written to solve a particular problem or carry out a particular job. Application software can be either generic or application specific :
| 6. | If you need a piece of software that
will perform a specific task then you will have to choose from one of three
options :
|
|
Section 9 : Word Processing |
A word processing package is used to prepare and edit text. Word processors are used to create all types of documents such as letters, reports and essays. Using a word processor you can type, revise and correct a document on the screen before printing it out. The layout of the page can be changed and a wide variety of different styles of text can be used to improve the presentation of a document. Tools such as spelling checkers can help ensure that the contents of a document is accurate.
The functions of a word processor can be divided up into several different categories :
| Page Layout | The page layout functions let you decide how each page will be set out. | |
| Text Presentation | The appearance of text can be easily altered. Different fonts and styles can be used and the size of text can be varied. Text can be neatly lined up on the page. | |
| Editing of Text | Text editing functions are used to revise and change text that you have entered. | |
| Blocks of Text | The style and position of selected blocks of text can be changed. | |
| Text Analysis | The word processor can look at your document and try to highlight any errors such as spelling or grammatical mistakes that you have made. | |
| Templates | Template files let you save favourite document layouts that you have created so that you can use them over and over again. | |
| Other Features | Most modern word processors will offer lots of extra features such as tables, bullet points and fancy text effects. | |
| Mail Merging | A database of names and addresses can be used to personalise letters that have been created in a word processor. |
A word processor is not always the best package to use to produce a document. Sometimes you may require more control over the layout of a page or you may wish to include a lot of graphics in a document. If this is the case then a Desktop Publishing (DTP) package would be more suitable. Desktop Publishers are often used to produce newspapers and books. As extra features are added to word processors it is becoming increasingly difficult to distinguish between a word processor and a desktop publisher.
Size
Computer printers will let you print word processed documents on several different sizes of paper. Most printers can use Letter and A4 size paper. Bigger printers will also print on A3 paper. Letter size paper is the standard in America and A4 is the standard in Europe.

It is important that the word processor is set to use the correct size of paper for your printer. This will ensure that all of your text will fit onto the page and that there will not be a large unused gap around the edge of the page.
Orientation
You can print onto a piece of paper in one of two orientations, which are usually known as portrait and landscape. These two orientations look like this :
Sometimes portrait is known as tall and landscape is known as wide.
Margins
It is usual to leave a small gap between the writing on a page and the edge of the page. This gap is called a margin. Leaving a margin is especially important when you need to bind a document together. Even if you do not want to leave a margin you will probably have to. Most printers can not print right to the edge of the page.
You can normally set the size of the top, bottom, left and right margins separately by typing in the distance from the edge of the page to the text.
Headers and Footers
When writing a document containing many pages such as a report you may want the same information to appear at the top and bottom of each page. For example you may want the name of the document and your name to appear at the top of each page. You may want to print each page's number at the bottom of the pages.

Many word processors will let you type special codes which will automatically insert information such as the current date or current page number into the header or footer of a document.
Columns
A page can be divided up into a number of columns. This is particularly useful if you want to produce a newspaper, newsletter or a leaflet which will be folded.
The text presentation functions let you specify what printed text will look like and how it will be positioned on the page.
Fonts
A font is a style of writing. Modern word processors are supplied with a wide range of fonts for you to choose from. Different fonts are useful for different purposes. Plain fonts such as Arial and Times New Roman are good for writing letters and reports. Fancier fonts such as Keystroke and Lincoln are suitable for use on posters.
Font Size
Most fonts are scalable. This means that you can use them at any size you want. The size a font appears at is specified by a number known as the font size. Sizes 10 and 12 are the most common for writing letters and reports. Fonts sizes are specified in 1/72ths of an inch. So fonts at size 72 are one inch tall and fonts at size 36 are half an inch tall. Larger fonts can be used for headings, posters etc.
Font Style
Each font can have a range of extra styles applied to it. The six common styles are :

Alignment
Alignment describes the position at which text appears on a line on the page. Alignment is sometimes known as justification. There are four different type of alignment :
Indentation
Text on the first line of a paragraph is often indented a short distance from the left hand margin. The first line of this paragraph has been indented :

One of the biggest advantages of using a word processor over preparing text manually is entered text can be easily edited. This means that mistakes can be corrected without spoiling the presentation of the final document. There are three main methods that you can use to edit text :
Many word processor functions can be applied to selected blocks of text. A block of text can be selected by using a mouse or the cursor keys. The selected text is usually highlighted by the word processor. When a block of text has been highlighted its properties can be changed. For example :
Word processors provide tools which will check the text that you have typed and highlight and possibly correct any errors that it contains. Almost all word processors will include a spelling checker. More sophisticated packages also include thesaurus dictionaries and grammar checkers.
Spell Check
A spelling checker will examine the text that you have typed and identify any spelling mistakes. When a mistake is found most spelling checkers will attempt to "guess" what the correct word should be and make some suggestions to you. You can accept one of the suggestions or retype the word correctly yourself.
Spelling checkers have quite large dictionaries, typically 80,000 words. However there will be some words that are not in the dictionary such as peoples' names. You can usually add extra words to the dictionary that is supplied with the word processor.
A spelling checker can not spot mistakes where you have typed the wrong word, e.g. it will not spot "their" instead of "there" or "the" instead of "they".
Thesaurus and Grammar Check
Advanced word processors may also offer thesaurus or grammar check features :
When you have designed a document layout that you like you may want to use it again for other documents in the future. For example :
If you have designed a document layout that you want to reuse then you can save it as a template file. When you start a new document you should load the template file to begin with. The template file will contain all the layout information for the new document. Using templates can ensure that the appearance of the documents you produce is consistent. It can also improve your productivity as you do not have to recreate the layout you want every time you start a new document.
Word processors are often supplied with a variety of templates for common tasks such as letter writing, reports and producing curriculum vitaes.
Most modern word processors will include lots of extra features in addition to those described above. Some common "extras" include :
Mail merging is a technique used mainly by companies and clubs to send personalised letters to customers or members. Using a standard (or form) letter and a database of names and addresses personalised letters addressed to the people in the database can be easily produced. The names and addresses of the people are automatically put onto the letters :

There are four main steps that must be followed to create mail merged letters. They are :
Companies believe that personalising letters in this way will increase the probability that customers will respond to advertisements. The customer is fooled into believing that the company has sent an advert specifically to him. In fact many thousands of people could receive the same letter.
Selective Mail Merges
Mail merged letters can be sent to every person whose name is recorded in a database. Alternatively a query can be used to select only some of the people in a database to send the letter to. For example :
When letters are sent to only some of the people in a database this is a selective mail merge. Selective mail merges are much more useful than simple mail merges which produce letters for everyone in a database. If you intend to use a database to carry out a selective mail merge then you must register the database with the Data Protection Commissioner to comply with the Data Protection Act.
1. | A word processing package is used to prepare and edit text.
|
| 2. | The most important features of a word processor package are listed in this table.
| |
| Page Layout | ||
| Orientation | Which way round the paper is printed on (portrait or landscape). | |
| Margins | The gaps between the text and the edge of the page. | |
| Header and Footer | Text which appears at the top and bottom of each page. | |
| Columns | Pages can be divided into columns for producing leaflets, newsletters etc. | |
| Text Styles | ||
| Fonts | Different styles of text. | |
| Font Size | Text can be printed at many different sizes. | |
| Font Style | Styles such as bold, underline and italic can be applied to text. | |
| Alignment | Text can be lined up on the left, right or center of the page or be fully justified. | |
| Editing Text | ||
| Copy / Cut and Paste | Blocks of text can be duplicated or moved using the copy, cut and paste options. | |
| Search and Replace | A word or phrase can be automatically replaced with another wherever it occurs. | |
| Text Analysis | ||
| Spell Check | The spelling in a document can be automatically checked and corrections suggested. | |
| Thesaurus | A thesaurus will suggest alternative words with the same meaning as a word that you have typed in. | |
| Grammar Checker | A grammar checker will examine the structure of any text you have typed. | |
| Templates | ||
| Templates | Templates let you store favourite document layouts to reuse. | |
| Other Features | ||
| Tables | Tables can be used to set data out neatly in rows and columns. | |
| Bullets & Numbering | Bullets and numbers can be used to present lists of data. | |
3. | A form letter produced
in a word processor can be linked to a
database of names to produce mail merged letters.
|
| 4. | A desktop publisher (DTP) package is an
alternative package which can be used instead of a word processor when more sophisticated
features are required.
| |
Section 10 : Desktop Publishing |
Desktop Publishing (DTP) software is used to produce professional-looking documents such as reports, books, posters or leaflets. DTP software gives you more control over the layout of a page than a word processor and lets you easily integrate graphics into your publications. In addition to the features of a word processor you should also expect a desktop publisher to offer you these facilities :
| Page Layout | The ability to define the layout of a page using frames to place text and pictures in. | |
| Fonts and Styles | A wide range of fonts and styles. | |
| Drawing Tools | Some drawing facilities, although these may be limited. | |
| Importing Pictures and Text | The ability to incorporate pictures and text from other packages in a document. | |
| Clipart | A library of pictures for you to include in your documents. | |
| Accurate Positioning | The ability to position objects extremely accurately on the page using guidelines or a grid. |
Many desktop publishers include wizards. A wizard is an interactive tool that guides the user through a potentially complex task. Using a wizard lets the user complete a common task more quickly and straightforwardly than starting from scratch.
A page in a desktop published document is set out as a group of frames which are positioned onto the page by the user. Here is an example page layout for the front page of a newsletter :

This layout includes two text frames which will contain the article that is to appear on this page. There is one picture frame which will contain a photograph to illustrate the article. The top frame will contain a header which will appear on every page in the newsletter. A frame can usually contain either text or a picture (but not both). A frame can be positioned and resized independently of all of the other frames.
This diagram shows the layout of all of the pages in the newsletter :
Although the exact layout of each page is not the same, the designers of the newsletter have adopted a consistent design for each page, i.e. :
The page designers will also have chosen consistent font styles so that text on each page has a standard appearance.
Linking Frames
Often an article on a page will not fit into one text frame. An article may have to be split between two or more text frames which may or may not be on the same page. So that this can happen desktop publishing packages will let you link frames together. You can link any number of frames together in any order to form a chain. When one text frame is filled up the text in the frame will automatically flow into the next text frame in the chain.
This diagram shows how the newsletter frames will be linked together :
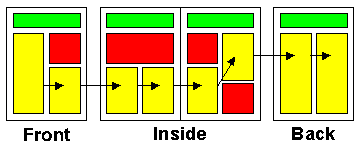
The facilities to draw frames anywhere on a page and link them together in any order make a desktop publisher a far more powerful package for setting out documents than a word processor.
A desktop publisher should provide a wider range of fonts and styles than a word processor would. For example many DTP packages incorporate a "fancy" text function. This function may let you :
The text below was created using the fancy text feature of a DTP package.

All desktop publishers incorporate some drawing facilities. Some will include most of the features of a drawing package. Others will have much more limited facilities. As a minimum most DTP packages will let you :
If the drawing features of your desktop publisher are not very good then you may find it easier to produce any drawings in a graphics package and then import the results into the DTP program.
Desktop publishing packages will let you assemble work from a variety of other packages into one document. For example :
The work produced in each of these packages can be brought into the desktop publisher which is used to lay out the information on the page as you want it to appear. A user may choose to produce work in another package rather than directly using a desktop publisher as the other package may offer better features than the desktop publisher. For example a spreadsheet will probably be capable of producing better charts than a DTP program could.
The process of bringing work produced in another package into a DTP program is known as importing.
Importing can be achieved by either copying and pasting data from one package to another or loading a file produced by another package into the desktop publisher. Desktop publishers will usually import files produced by a wide variety of other packages.
Sometimes special standard file formats such as Rich Text Format (RTF) or JPEG graphic file formats are useful. Most packages can output information in one of these common formats. All desktop publishers will be able to import information in these formats.
Hardware devices such as a scanner or a digital camera are often used to transfer pictures onto a computer for use in desktop published documents.
Clipart images are provided as libraries of pictures either with a desktop publishing package or separately. A clipart library will typically contain thousands of images relating to commonly used subjects. These images can be used within the desktop publisher to improve the appearance of work. Example categories might include :
Clipart images can usually be resized and moved about on the page but can not usually be edited by the user. The use of clipart can greatly speed up the production of documents.
To achieve a truly professional appearance it is important to be able to position objects such as text frames or pictures accurately onto the page. If a picture is placed above a text frame but they do not quite line up then the appearance of a document can be spoiled. Two tools are usually provided to help you position objects accurately. They are guidelines and grids.
Guidelines
Guidelines are lines which are placed onto the page to help the user position objects. The user can place guidelines anywhere on the page. Any object placed near to a guideline will "jump" or "snap" to the guideline. i.e. the object will move to line itself up exactly with the guideline. The guidelines will appear on the screen but will not appear on the final printed page.
Grids
A grid of points can be placed over a page. The points are placed at regular intervals specified by the user, for example every one centimetre. Whenever an object is placed on the page it will jump to the nearest point on the grid.
Many users of desktop publishing software want to carry out very similar tasks such as creating newsletters, posters, greetings cards and certificates. Completing these tasks from scratch can be very time consuming, so most desktop publishers include a wizard tool to allow common tasks to be complete more quickly and straightforwardly.
A wizard is an interactive tool that guides the user through a potentially complex task, such as creating a newsletter. The wizard will ask the user questions about the layout of the newsletter and create a basic document that matches the users requirements. The user can then edit the document manually to complete the creation process. The type of question that a newsletter wizard might ask include :
The questions asked by a wizard will depend upon what the wizard does. Other software packages such as databases and spreadsheets may also include wizards to help the user complete common tasks.
1. | Desktop Publishing (DTP) software
is used to produce professional-looking documents such as reports, books, posters or
leaflets.
|
| 2. | A DTP package gives you much more
control over the layout of pages in a document than a word processor would.
|
| 3. | In addition to the tools provided
by a word processor, most DTP packages will provide the tools detailed in this table.
|
|
|
| 4. | Many desktop publishers include wizards. A wizard is an interactive tool that guides the user through a potentially
complex task. Using a wizard lets the user complete a common task more quickly and straightforwardly than starting from scratch.
| |
Section 11 : Graphics |
Computer graphics or images are often used either by themselves or to enhance the quality of other documents, for example a desktop published document. There are three distinct types of package which can be used to create images on a computer. They are :
| Painting Packages | This is the most basic type of graphics package. These packages allow you to paint onto the screen as if it was a canvas. Unfortunately they produce files which take up a lot of storage space and painted images are difficult to edit. | |
| Drawing / Vector Drawing Packages | These are more sophisticated than painting packages. They store images as a set of objects which can be easily edited. | |
| Computer Aided Design (CAD) Packages | Very advanced, highly accurate packages which can be used for designing three dimensional objects such as houses and machinery. |
Many special hardware devices are available to help in the production of computer graphics. These include :
Painting packages allow you to paint onto the screen as if it was a canvas. Many tools will be provided to help you do this. The most common tools are :
| Palette | Using the palette you can select the colours that you want to draw with. There will be a current colour which will be used when you draw anything onto the screen. |
| Freehand Brush | By moving the pointer around the screen you can draw directly onto the page using a brush. The width of the brush can be altered to produce thick or thin marks. |
| Straight Lines | It is very difficult to draw straight lines with a freehand brush. You would need a very steady hand to do this. Therefore a special straight line tool which will join up two points that you click on is usually available. |
| Shapes | Most painting packages also provide tools to draw a range of mathematical shapes such as circles and rectangles. These can be either filled in or drawn as outlines only. |
| Text | The text tool will let you enter text and place it onto the page in a variety of fonts. |
| Flood Fill | This tool will fill in an area of the screen with the current colour. If you click on a point on the image then all of the points surrounding it that are the same colour as the clicked on point will be filled with the current colour. |
| Zoom | You can zoom in on a particular area of the drawing so that you can see it in more detail. This will enable you to produce more accurate drawings by adding finer detail. |
Painting packages are the best type of package to use if you want to edit scanned images such as photographs.
Painting packages store images as a series of small dots called pixels. If you zoom far enough into the image you will be able to see the individual pixels. The colour of each individual pixel on the screen must be remembered and saved. Files storing the colours of each pixel in an image are known as bitmap files. Because so much information has to be stored files saved by painting packages are usually very large. An image the size of a typical computer screen (800*600 pixels) would take up over one megabyte of memory. Therefore images produced by painting packages are often stored in a special compressed format such as GIF or JPEG.
Painting packages have one major limitation. It is the same limitation that you will find if you try to paint a picture on canvas. This limitation is that once a mark has been placed onto an image it is extremely difficult to change it. The only way to erase a mark is to paint over it in the same colour(s) as the background. There is no simple way to move a mark from one position in an image to another. Most packages provide an undo feature so that you can erase one unwanted mark immediately after you have made it. But in general it is very difficult to edit an image with a painting package.
A further limitation of images produced by a painting package is that if you enlarge them too much then you will be able to see the individual pixels that make up the image. The image will look very blocky or pixelated.
Drawing packages overcome many of the limitations of painting packages. They make it easier to edit images and can store images in much smaller files. Images produced this way do not look blocky (pixelated) if enlarged. Drawing packages are also known as vector drawing packages.
Drawing packages do not store images by remembering the colour of each pixel in the image. Instead an image in a drawing package is built up from a number of shapes or objects. The drawing package remembers the position, size, shape and colour of each object that you place onto the image.
For example this image :
would be stored as a definition similar to this one :
Basic Features of a Drawing Package
Because a drawing package remembers all of the information about each object you can easily change the appearance of the objects and hence the image.
A drawing package will provide these extra editing features :
| Resize Object | Using the mouse an object can be stretched or shrunk in any direction. |
| Rotate Object | Using the mouse an object can be rotated to appear at a different angle in an image. |
| Move Object | Objects can be moved around the screen to see how they look in different positions. |
| Delete Object | Unwanted objects can be easily deleted. |
| Change Object Properties | Each object will have a number of properties. The properties will depend upon the type of object. For example a rectangle will have two colours (fill colour and line colour) as properties. These properties can easily be changed. |
A drawing package will also offer all of the tools that a painting packages does with the exception of a freehand brush and flood fill which will not be available.
Layering Objects
Objects stored as part of a drawing are stored in layers on top of each other. In the example image above, the layer that the green line is stored in must be on top of the layer that the red circle appears in because the line is in front of the circle. Drawing packages usually provide functions to move objects between layers.
| Move to back | Moves the selected object to the layer at the back of the image so it will appear behind all of the other objects. |
| Move to front | Moves the selected object to the layer at the front of the image so it will appear in front of all o the other objects. |
Grouping Objects
Several objects can be grouped together so that they can edited as if they were a single object. For example several objects may be used to build up an image of a car. These objects could then be grouped together. Once grouped together all of the objects in the car image could be stretched, copied and moved as if they were one single object.
Accurate Positioning of Objects
To achieve a professional appearance it is important to be able to position objects very accurately onto the page. Two tools are usually provided to help you position objects accurately. They are guidelines and grids.
| Guidelines | Guidelines are lines which are placed onto the page to help the user position objects. The user can place guidelines anywhere on the page. Any object placed near to a guideline will "jump" or "snap" to the guideline. i.e. the object will move to line itself up exactly with the guideline. The guidelines will appear on the screen but will not appear on the final printed image. |
| Grids | A grid of points can be placed over an image. The points are placed at regular intervals specified by the user, for example every one centimetre. Whenever an object is placed on the image it will jump to the nearest point on the grid. |

Computer Aided Design (CAD) packages are the most sophisticated computer graphics packages. They are used by architects to design buildings and engineers to design machinery. CAD packages operate in a very similar way to drawing packages. They store information about each object that makes up an image so that the image can be easily manipulated. A fully featured CAD package may cost several thousand pounds.
The most notable features that are present in a CAD package which are not present in a drawing package are :
| 3D Objects | Objects and drawings can be created in three dimensions rather than just two. This is vital for producing plans of houses etc. Images can be viewed from any angle. |
| Accuracy | Objects can be positioned much more accurately using a CAD package. Accuracy can easily be to within one thousandth of an inch. |
| Libraries of Components | Libraries of frequently used objects, such as bolts or windows can be stored and reused in many designs. |
| Costing of Designs | Using a database of object costs a CAD package can estimate the cost of producing a design that has been drawn. |
Computer Aided Design programs can sometimes be connected directly to automatic machinery such as a lathe which is controlled by the computer. A design made on the program could then be manufactured automatically using the lathe. When a CAD program is used like this it is called Computer Assisted Manufacturing (or CAM).
1. | There are three different types of
computer graphics packages which can be used to produce images. They are painting packages,
drawing packages and
computer aided design (CAD) packages.
|
| 2. | Many specialist hardware devices
such as scanners, digital cameras,
high resolution monitors,
plotters and printers
are available to assist in the production of computer graphic images.
|
| 3. | This table compares the three
different types of computer graphics packages.
| |
| Comparison of Graphics Packages | ||||||||||||||||||||||||
| Comparison | Painting | Drawing | CAD | |||||||||||||||||||||
| Image Storage Method | Images are made up of thousands of small dots called pixels. The colour of each pixel is stored in a file known as a bitmap. This makes image files very large and difficult to edit. | Two dimensional images are stored as groups of objects. This makes image files small and easy to edit. | Three dimensional images are stored as groups of objects. Images are easy to edit and can be viewed from any position. | |||||||||||||||||||||
| Tools | 1. Palette 2. Freehand Brush 3. Straight Lines 4. Shapes 5. Text 6. Flood Fill 7. Zoom | As for a painting package, but :
Objects can be :
| As for a drawing package, but all tools will work with 3D objects and
be more accurate. Many CAD packages can also :
| |||||||||||||||||||||
| Advantages | 1. Cheap to purchase. 2. Easy to use. |
|
| |||||||||||||||||||||
| Disadvantages |
|
|
| |||||||||||||||||||||
| Cost | ||||||||||||||||||||||||
Section 12 : Databases |
A database is a computerised record-keeping system. Databases are used when a large quantity of information has to be stored. A database is very useful because it will provide tools to let the user search through the data that has been stored to find particular pieces of information. The data stored in the database must be organised so that the computer can analyse and search it automatically.
Data in a database is usually organised into one or more files storing information relevant to the organisation that has created the database. For example a database keeping information for a doctors surgery may contain the following files :
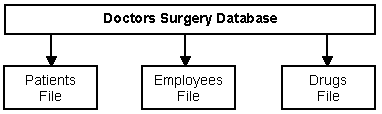
Each file is identified by a filename (e.g. "Patient", "Employees"). Sometimes a file in a database is known as a data table.
When setting up a database it is usual to define a set of queries which will be used to answer questions from the data in the database. The output that is produced by the database is called a report.
There are two different types of database package that you are likely to find in a school. They are flat file databases and relational databases.
| Flat File | A flat file database is the simplest kind of database. With a flat file database package each database that you create can only contain one file. |
| Relational | A relational database can store more than one file within a database. The files can each have a different structure and relationships (or links) can be created between the files. Queries can answer questions by examining and comparing data in more than one file. A relational database management system ( RDBMS ) is a piece of software that can be used to help you create a database consisting of multiple files and link them together. |
Data entered into a database is stored in files (also known as tables). A file is a collection of records, each of which contains information about one person or thing. The data in the records is separated into fields which each hold just one item of data. Each field is identified by a field name.
The following diagram shows examples of a file, records and fields that might be used in a doctors’ surgery to keep information about patients. There is a file containing information about all of the patients. Within this file there is one record for each patient.
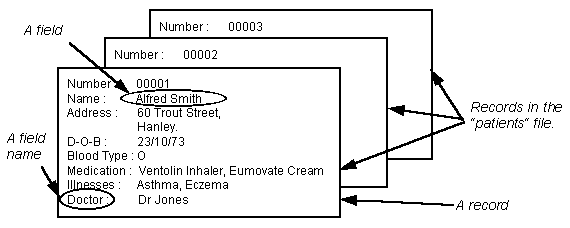
To create a file you need to tell the computer the names of the fields that will be stored in the records in the file. All of the records in a file must contain the same fields. You will also have to specify what type of data can be stored in each field and how much space should be reserved to store the data. Together, this information is known as the structure of the record (see example).
You should know and understand these important database terms :
Field
| A field is a single item of data stored in a database such as age or car registration number. Each
field is identified by a field name.
| Record
| A record is all of the information that is stored about a person or thing.
| File
| A file (or table) is a collection of records, each of which has the same structure.
| |
Remember that a flat file database can store just one file, whereas a relational database can store many files in one database.
Each field in a record must have a type The field type refers to the kind of data that can be stored in the field. Possible field types include :
| Type | Description | Example Data |
| Numeric | Numbers only | 1545, 1.23, 12303 |
| Alphabetic / Text | Letters only | hello, Hi, TEST |
| Alphanumeric | Letters and numbers | robot 23, area 12, WA13 9IJ |
| Boolean / Logical | True or false | true, yes, false, no |
| Date | A date | 12/02/98, 1/12/71 |
Only data that matches the type of a field can be stored in a field. For example you could not store the word "cricket" in a field which is set to be numeric. Some databases will also let you store images and sound recordings in fields.
Each field in a record can be of either fixed or variable length. When you create a file you must decide whether each field will be of fixed or variable length :
| Fixed Length Field | A fixed length field contains a set number of characters. |
| Variable Length Field | A variable length field can contain any number of characters. If a field is of fixed length, you must decide how many characters it can contain. |
If a field is of variable length then an End-Of-Field marker must be put after the data stored in the field to show where it ends.
If a record contains some fields which have variable lengths then the record length will be variable. If a record contains only fixed length fields the record length will be fixed.
The main advantages of variable over fixed length fields or records are:
The main advantages of fixed over variable length fields or records are :
Usually one particular field of each record contains an item which is used to identify the record. This field is called the key field . The value in the key field must uniquely identify each record.
A patient number could be used as a key field to uniquely identify each patient’s record in the doctors’ patient file. The patient’s name could not be a key field as there may be more than one patient with the same name.
Sometimes a record may contain more than one key field. For example the doctor’s patients file may contain both a patient number and a National Insurance number for each patient. Both of these are key fields. We therefore choose one of them and call it the primary key field.
Often records are stored in a file sorted into order using the primary key field. When records are stored in a file in a particular order we say that the file is a sequential file. This is especially likely to be the case if the files are stored on a serial access medium such as magnetic tape.
Sometimes information is coded before it is typed into a database. For example consider a library database where books are classified as being fiction, non-fiction or reference. This information could be stored in an alphabetic field of fixed length 11 ("non-fiction" is 11 characters long). Alternatively the classifications could be coded like this :
Using these codes the information can be stored in an alphabetic field of length one. Coding information reduces the amount of storage space required and speeds up the process of typing the information in. It also makes it easier to validate data as coded information must usually be in a specific format. For coding to work properly everyone needs to know what the correct codes are.
If you are using a relational database then you will be able to create more than one file within a database and link the various files together. Links between different files in a database are known as relationships.
Here is an example showing the relationship between a Products File and a Suppliers File in a stock control database. The names of the fields in each file are shown in the example, but the record structure (data types, field lengths) is not.
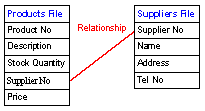
The relationship between the files is made through the Supplier No field which appears in both files. The supplier of a particular product is identified by the Supplier No in the Products File. To find the details of this supplier (name, address etc.) this Supplier No can be looked up in the Suppliers File. Through the user creating a relationship between these two files the database software is able to automatically look up details related to the supplier of a product and to prevent the user accidentally entering a Supplier No in the Products File that does not match a supplier in the Suppliers File.
To create a link between two files the fields that are linked must have the same data type. It is also common for fields in a relationship to have the same name and for one of the fields in the relationship to be the primary key field in a file.
A library database is being set up. The database will be created with a relational database package.
The database needs to store information about three different things. These are the library's members, books and the loans it has made. The database designer has therefore identified these three files that the system will require :

For each of the three files the designer must now decide what information the file should contain. This will include the field names, types and lengths. A primary key must also be identified for each file.
Members File
The members file will store information about each borrower. The primary key field must be Membership Number as it is the only field which will uniquely identify each person. Member Name can not be a key field as two borrowers could have the same name.
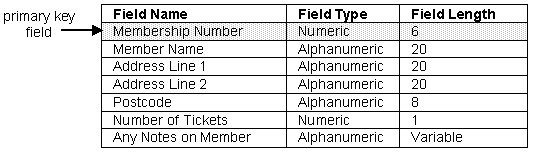
Books File
The books file will store information about each book the library owns. The primary key field must be Copy Number which can uniquely identify each copy of each book.
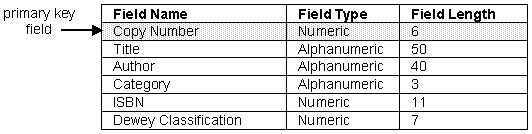
The category of each book, e.g. "History", "Geography", "Science Fiction" will be coded as a three letter code e.g. "HIS" or "GEO" to reduce storage space and speed up data entry.
Loans File
The loans file will store details of who has which books on loan at the moment. When a book is borrowed a record will be created in the loans file which will store the Membership Number of the borrower, the Copy Number of the book and the date the book is due back. Copy Number must be the primary key field. Membership Number can not be a key as a borrower may borrow more than one book at a time.
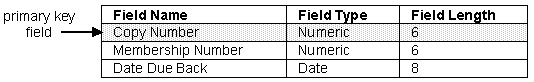
The following relationships exist between the three files :

These relationships can be used to find out information using the data in the database. For example to find out who has the book "100 Facts about Animals" the database software must :
When the database structure has been created you will want to put data into the files in your database. You may also want to change data that is stored in your database. There are three important operations that you may carry out on data in a database :
| Add a Record | Put a new record into the database. |
| Ammend a Record | Change the contents of a record that already exists. |
| Delete a Record | Remove a record from the database. |
In a simple database package you will probably have to type the data directly into the files. More sophisticated database packages let you develop your own user interface through which data can be entered and manipulated. This is done by the creation of forms (or views) that let the user enter and view data simply. Here are two example forms that are part of a library system :

The buttons on the forms (Add, Cancel and Go) will cause the database to carry out specific actions when they are pressed. The user may be able to define these instructions with macros.
Sophisticated database packages will also let you specify rules that can be used to check data as it is entered. These rules can check that entered data is sensible but not that is correct. They are known as validation rules.
Sophisticated database packages can validate data that you enter into a database to ensure that it is sensible. Data can be validated as it is typed into a file or
form. Validation checks on fields in a file are usually specified at the time that the file is created. Here are some common types of validation checks that can be carried
out by database software :
| Validation Checks | ||
| Presence Check | Checks that data has been entered into a field and that it has not been left blank. e.g. check that a surname is always entered into each record in a database of addresses. | |
| Type Check | Checks that an entered value is of a particular type. e.g. check that age is numeric. | |
| Length Check | Checks than an entered value e.g. surname is no longer than a set number of characters. | |
| Range Check | Checks that an entered value falls within a particular range. For example the age of a person should be in the range 0 to 130 years. | |
| Format Check | Checks that an entered value has a particular format. e.g. a new-style car registration number should consist of a letter followed by 1 to 3 numbers followed by 3 letters. | |
| Table Lookup Check | Checks that an entered value is one of a pre-defined list of valid entries which should be allowed. | |
A query (also known as a filter or search) is used to answer a question from the data in a database. Queries look through the database and find all the records that match a particular condition (or criterion). They are normally defined in a very basic language called a query language. When a query is run it produces as output a list of all of the records that match the condition that defined the query. A common query language is called SQL which stands for Structured Query Language.
Recall the patients files in the doctors surgery database :

The following condition could be used to search this file to locate all of the patients who see Dr Jones :
![]()
Here are some other examples queries :
| Question to Answer | Query |
| Which patients have blood type O | Blood Type = "O" |
| Which patients were born before 1980 ? | D-O-B < 01/01/80 |
| Which patients live in Hanley ? | Address contains "Hanley" |
The comparisons that you can make in queries will depend upon the database program that is being used. Common ones are :
| equals (=) | greater than (>) | less than (<) | greater than or equal to (>=) |
| less than or equal to (<=) | contains | does not contain | sounds like |
Reversing Queries
Sometimes you may want to search for records which do not match a particular criterion. For example you may want to find everyone who is not a patient of Doctor Jones. The keyword NOT is used to do this.
Queries Using More Then One Field
More complicated queries can be created by linking together more than one search condition. For example this condition can be used to find all of Dr Jones’ patients who have blood type O :
Blood Type = "O" AND Doctor = "Dr Jones"
This condition will find all of the patients who live in Hanley or were born after 1985 :
Address contains "Hanley" OR D-O-B >= 01/01/86
The words AND and OR are the only ones that can be used to link two simple conditions together to make a more complicated query. The difference between using AND or OR to join two conditions is :
Using Brackets In Queries
For very complicated queries you may need to use brackets to tell the database what order to use to evaluate the conditions that make up the query. Brackets are used for the same purpose in mathematics :
e.g. (2*3)+4 does not give the same result as 2*(3+4)
The brackets tell the person doing the sum which order to use to calculate its different parts. Similarly when writing a query :
would produce different results. Query (1) would find everyone who lives in either Hanley or Stoke who was born after 1985. Query (2) would find everyone who lives in Hanley (not just those born after 1985) as well as anyone who lives in Stoke who was born after 1985.
Queries Using More Than One File
So far all of the queries that we have looked at use data from one file only. With a flat file database this is not a limitation because flat file databases can only use one file at a time. However when working with relational databases this is a significant limitation. One of the important advantages of a relational database is that queries can be written which use data from more than one file. To enable this a much more sophisticated query language is required than the one we have used. SQL or Structured Query Language is one such language. The language must specify what data to look for and which file to look in.
Consider a database that stores information about which forms the students at a school are in. The database has two files. The first contains information about students and has the fields Student and Form. The second contains information about forms and has the fields Form and Form Tutor. Here is the contents of the two files :
Students File
| Student | Form |
| A. Freeman | 4LA |
| B. Purves | 4UD |
| C. Date | 4UD |
| H. Darwen | 4LA |
Form Tutors File
| Form | Form Tutor |
| 4LA | Mr J. Smith |
| 4UD | Mr J. Bloggs |
To find out the names of all of the students in Mr J. Smith's form the database would have to :
In SQL one way to express this query would be :
SELECT *
FROM [Students File], [Form Tutors File]
WHERE [Form Tutors File].[Form Tutor] = "Mr J. Smith" AND [Form Tutors File].Form = [Students
File].Form
A detailed knowledge of a powerful query language such as SQL is not required for a GCSE course.
Often you may only want to display some fields from the records that are in your database or display the records in a particular order. A report defines how the records in a database (or those found by a query) will be displayed. Typically a report will let you specify these things :
Standard reports can be either tabular (set out as a table) or columnar (set out as a form). Alternatively a report designer can be used to define exactly how a report should be set out.
Tabular Reports
When a tabular report is printed multiple records are printed on each page. Each record takes up one line in a table. The names of the fields are printed at the top of the table.
Here is an example tabular report :

The report sorting options will determine in what order the names are printed on the report. Grouping could be used to divide the people on the report into groups. For example the patients could be put into groups by the name of the doctor they usually see. Most databases will print each group on a separate page.
Columnar Reports
Columnar reports print each record on a separate form. Usually each form is printed on a different page. Here is an example of a columnar report :

Columnar reports are often used for printing items such as tickets.
Report Designer
A report designer lets the user decide exactly how a report will appear. The designer works much like a desktop publisher. The user can use tools from a toolbox such as a text tool and drawing tools to define how the report will appear. Fields of information from the database can be positioned anywhere on the report.
Report designers can produce much more advanced reports than simple tabular or columnar reports. Some report designers can also perform calculations using the data in a report and even draw charts from the data.
Most databases will let you sort data so that it is displayed in a particular order. To sort a database into an order you must specify :
Sometimes you may wish to use more than one field to sort a database. For example if a database contained a list of names and addresses then you might choose to sort it by surname. However some people will have the same surname, so you may decide to tell the computer that if two people have the same surname they should be put in order by their forenames.
If you do this then the fields that you choose to use to sort the database are known as the 1st sort field, 2nd sort field and so on.
A macro is a short sequence of instructions that will automate a task. People who make databases often create macros to simplify the use of a database.
A macro in a database is a short sequence of instructions that the database will carry out. Writing a macro is like writing a program in a high level language. The user writes the instructions that will carry out the actions required of the macro. Common tasks that macros are used to perform in a database include opening and closing forms, printing reports and running queries.
Once a macro has been written it must be saved. The macro can then be executed (or run) whenever the user requires it. Often macros are associated with buttons on forms so that when a button is pressed a particular macro is excecuted.
Importing Existing Data
Sometimes the data that you want to store in a database is already available somewhere else such as in a another database, a spreadsheet or word processed document. If this is the case then instead of manually typing the data in again it will be quicker and easier to import it automatically from the existing source.
Before you can import data into a database you will need to save it in a standard file format such as a Comma Separated Value (CSV) or Tab Separated Value (TSV) file. The database package will then be able to read the data out of the file and store it within the database. You may need to create the record structure that will hold the data manually before importing the file or the database may be able to do this itself by analysing the imported data.
Exporting Data
Databases contain tools (such as queries) that let you analyse the data they contain. Sometimes however you may wish to take some data from a database and use it in another package. For example :
To do this you must save the data that you wish to use in the other package in a standard file format such as a Comma Separated Value (CSV) or Tab Separated Value (TSV) that the other package can read. This is known as exporting data.
In a flat file database data can only be stored in one file. Here is an example of a flat file database that stores information about students in a school including what form they are in and who their form teacher is :
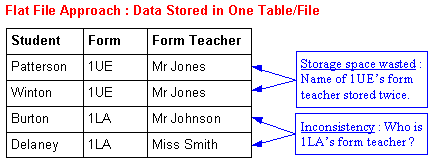
There are two serious problems that have been caused by trying to store this data in a flat file database :
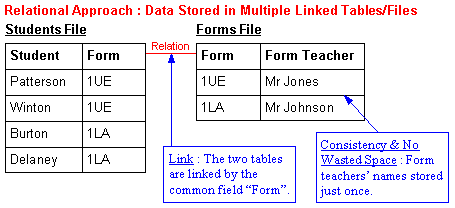
Relational databases have two important advantages over flat file databases :
You should follow these ten steps to help you design a database :
| 1. | Decide what outputs you want the database to produce - what questions must it answer ? |
| 2. | Use the information about the outputs you want to decide what files/tables you need to set up to store data and what fields you will have to put into these files/tables. What will the key field be for each file ? |
| 3. | Decide what types each field should have and whether the fields will be fixed or variable length. Could data be coded to reduce field size ? |
| 4. | If you are using a relational database then decide which files/tables will be linked together and which fields will be used to do this. |
| 5. | If the database you are using allows you to design forms through which the user can access and enter data then sketch these and decide how they will operate. |
| 6. | If the database you are using supports them decide what validation rules to use to ensure entered data is sensible. |
| 7. | Design the queries and reports that you will use to get information out of the database. Determine what conditions the queries will use and sketch how the reports will be set out. |
| 8. | If the database you are using supports them plan any macros that you will use to automate tasks such as opening forms, sorting, printing reports etc. |
| 9. | If appropriate design data collection forms to gather the information to put into the database or identify where the data can be imported from. |
| 10. | Identify the data that you will use and the tests that you will perform to check the database is working, and write this down in a test plan. |
What To Test
After you have created a database you need to test it to ensure that it is working properly. There are three main areas that you need to test. They are :
| 1. | Test that the database will accept reasonable inputs and (if you have carried out validation) rejects inputs that are not sensible. |
| 2. | Test that the outputs the database produces are correct. These outputs might be on forms or reports or be the results of running queries. |
| 3. | If you have created any macros you will need to test that these perform the correct actions at the correct times. |
The Test Plan
You should created a test plan that lists all of the tests you will carry out on your database. In the test plan you should state :
If your database is being produced as a piece of coursework it is a good idea to give each test a number.This will allow you to link the tests in your plan to evidence you later produce to show that you have carried them out.
Test Results
When you carry out the tests of your database you need to check that the actual results you obtain match the results you expected to get. If they do not then you will need to work out why not and try to correct the problem. You will then need to carry out the test again.
If your database is being produced as a piece of coursework you should collect evidence to show that you have carried out the tests and cross-reference this evidence to the descriptions of the tests in the test plan.
1.
| A database is a computerised record-keeping system.
|
| 2.
| Databases let you search through large quantities of data very quickly to
answer questions.
|
| 3.
| Data stored in a database must have a standard, regular structure.
|
| 4.
| It is likely that you will encounter two different types of database package :
| 5.
| A field is a single item of data stored in a database such as age or car registration number. Each
field is identified by a field name.
|
| 6.
| A record is a collection of fields that store all of the information about a person or thing.
|
| 7.
| A file (or table) is a collection of records, each of which has the same structure.
|
| 8.
| The structure of a record refers to :
|
|
Section 13 : Spreadsheets |
A spreadsheet package is used for performing calculations and drawing charts. When you open a spreadsheet package the screen displays a very large table similar to this :
The table is divided into a number of boxes called cells. You can type information into each cell. Going across the table are many rows each of which is identified by a number. Going down the table are many columns each of which is identified by a letter.
Each cell is identified by a unique name called a cell reference. The cell reference is formed by writing down the letter of the column that the cell is in followed by the number of the row that it is in.
Groups of joined cells are known as a range. A range can be described by writing down the cell references of the cells at the top left and bottom right corners of the range with a colon to separate them.
You can enter three different types of information into a cell. The three types are :
Whenever any numbers are changed the calculations worked out by the formulas will be recalculated.
This simple spreadsheet is used to calculate exam marks. The marks of each pupil in the two separate papers which make up the exam must be typed in. Formulas are then used to calculate each pupil’s total mark and the average mark for the whole class in each paper.
The first diagram shows the numbers, labels and formulas that were typed in. The second shows the answers that were calculated by the spreadsheet.
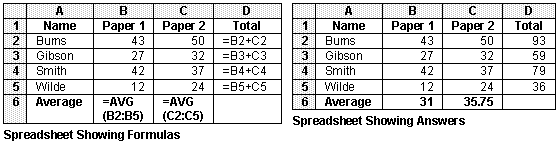
A formula carries out a calculation using numbers that have been typed into the spreadsheet. The answer appears in the cell you type the formula into. In most spreadsheets formulas always start with a special symbol such as the equals sign. Some simple example formulae are :
| Formula | Explanation | Formula | Explanation |
| =A1+B7 | Add up numbers in A1 and B7. | =A2/C8 | Divide number in A2 by C8. |
| =B2-C2 | Subtract number in C2 from B2. | =A1*B1 | Multiply numbers in A1 and B1. |
| =A1+B7-C2 | Add number in A1 to B7 then subtract number in C2. | =(A1+A2)/B7 | Add together number in A1 and A2. Then divide by number in B7. |
When you change any numbers the results of the formulas that use the numbers will be recalculated.
Formulae can sometimes become very long if you want to include a lot of numbers in the calculation. Long formulae are tedious to type and can lead to errors. Consider a formula to add up fifty numbers in column A :
= A1 + A2 + A3 + A4 + … + A50
Functions can be used in formulae to make some calculations simpler to carry out. Functions often act on ranges of numbers. Important functions supported by most spreadsheets include :
| Function | Explanation |
| =SUM(A1:C2) | Adds up the contents of the cells in the range A1:C2. These cells are A1,A2,B1,B2,C1 and C2. |
| =AVG(A1:C2) | Averages the contents of the cells in the range A1:C2. |
| =MIN(A1:C2) | Finds the smallest number in the cells in the range A1:C2. |
| =MAX(A1:C2) | Finds the largest number in the cells in the range A1:C2. |
| =CNT(A1:C2) | Counts how many numbers are in the range A1:C2. |
| =PI() | Gives the value of PI. |
| =RAND() | Gives a random decimal number between 0 and 1. |
| =INT(A1) | Gives the integer (whole number part) of the contents of A1. |
Most spreadsheets have many more functions than this. They will include financial, statistical and database functions.
Often you will want to use several similar formulae in a spreadsheet. In the spreadsheet below a formula which is nearly the same is used to calculate each student’s total mark. The formula is changed slightly for each pupil because their marks are on different rows.

To avoid the need to type a similar formula in the three formulas in rows 3 to 5 can be generated automatically using the formula in row 2. To do this you must :
Copying a formula like this is known as replication. If you want to copy a formula along a row rather than down a column you can use the fill right option instead. Because the formula changes as you copy it is known as a relative formula, or relative reference.
Sometimes you may not want a reference to a cell to change when a cell is copied in this way. To prevent a cell reference in a formula changing when you copy it you should precede the letters and numbers in the reference by a $ sign. Look at this formula :
=D3* $A$1
If you chose the fill down option with this formula the next row will contain the formula =D4*$A$1, the one after the formula =D5*$A$1 and so on. The first cell reference D3 changes but the second, A1, does not. Because the A1 reference does not change it is known as an absolute reference.
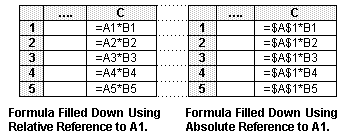
As well as fill down and fill right, the usual cut, copy and paste operations can be used to copy (or replicate) formulas.
You may wish to put a series of numbers or values that follow on from each other into a row or column on your spreadsheet. Most spreadsheets have a fill series operation to do this. Example series include :
To put a series of values into a cell you will need to :
Type the initial (first) value into the cell you want it to appear in.
Select the cells you want the series to be put into, including the first value.
Choose the fill series option.
You may then have to enter the step that the series should increase by each time.
The spreadsheet can use a condition function to make a decision based on a value stored in the spreadsheet. The formula :
= IF(A1>=100,"Boiling","Not Boiling")
will output the message "Boiling" if the contents of cell A1 is greater than or equal to 100 and will output the message "Not Boiling" otherwise.
If statements can be nested (put inside each other) to give more than two responses based on several conditions. The formula :
= IF (A1<=0,"Frozen",IF(A1>=100,"Boiling","Liquid"))
will display "Frozen" if A1 contains a value less than or equal to 0. Otherwise, if A1 contains a value greater than or equal to 100 it will display "Boiling". If neither of these are true it will display "Liquid".
Most spreadsheets include database functions which can be used to treat a table in the spreadsheet as if it were a database. These functions typically let you search through the table to lookup information. A common spreadsheet has a VLOOKUP function which looks down a table to find a value. It is most easily understood by using an example.
This section of a spreadsheet is a table containing information about cars.

The column titles are the field names. Each row (apart from the top one) contains a record.
The formula =VLOOKUP("Corsa",A2:C4,2) will look down column A cells A2 to A4 for the value "Corsa". If it finds it, it will return the value in the same row but two columns to the rights, which is the price of a Corsa, £8,295. If the value "Corsa" was not in the list then the formula would display an error message.
The HLOOKUP function is similar to VLOOKUP except it looks along rows for data instead of looking down columns.
A spreadsheet's sort function will let you put the data in a table into order using any of the columns of data in the table. To sort data in a spreadsheet you will need to :
The data in this table has been sorted :

To perform the sort the table range (A2:C4) was selected. The table was then sorted using the data in column A into ascending order. Note that row 1 was not included in the sort range because it contains the titles for the table rather than data.
Information in spreadsheet cells can be formatted like text in a word processor. The font can be changed and information can be aligned to the left, right or centre of a cell. Titles can also be centered across multiple columns. Borders can be placed around cells to make distinct tables and cells can be filled with colour to make a spreadsheet clearer. Changing the appearance of the information in a cell like this is known as changing the cell format.
The appearance of numbers in cells (called the data format) can also be controlled. Example formats you may want to apply to a value in a cell are :
You should also be able to change the width of columns and the height of rows to suit the data that has been typed in. If necessary extra rows or columns can be inserted into the spreadsheet and unwanted rows or columns can be deleted.
Charts can be created from data in a table in a spreadsheet. To create a chart you will need to :
To draw a chart you will need to set a number of options such as :
When you save a spreadsheet the charts you have drawn from it will be saved with it. If you change any of the figures on your sheet the charts should change automatically.
Alternatively, a specialised charting package could be used to produce a chart.
A macro is a short sequence of instructions that will automate a task. Using macros can save you a lot of work when you are using a spreadsheet by carrying out repetitive tasks for you. Not all spreadsheet programs will let you use macros.
Consider a spreadsheet which shows the league positions of some football teams in a league. Whenever a team plays a match the team's points score and position in the league may change. You will need to sort the data in the spreadsheet to put the teams into points order after each match. To sort data in most spreadsheets you will need to follow these three steps :
Manually completing this process every time a team played a match would be very time consuming. Instead a macro can be created that will automatically carry out the three steps for you. Once a macro is created you can carry out the entire process by simply executing (or running) the macro.
Creating A Macro
A macro can be created by either programming or recording it.
| Programming A Macro | A macro is stored as a sequence of instructions in a macro language. Programming a macro is like writing a program in a high level language. The user writes the instructions that will carry out the actions required of the macro. The macro instructions to sort the football league table might look something like this :
Most computer users do not have time to learn how to program macros, so a simpler method of creating basic macros is available. |
| Recording a Macro | To record a macro you simply show the computer what you want the macro to do.
A macro can be recorded like this :
When this process is followed the spreadsheet will automatically generate the macro instructions as if the macro had been programmed. |
When a macro is being designed a flowchart is often used to show the sequence of actions that the macro should carry out.
Executing A Macro
Every macro must have a name to identify it. When a macro is selected and its macro instructions are carried out the macro is said to be executing or running. There are two ways that you can execute a macro :
Sophisticated spreadsheet packages can validate data that a user enters into a spreadsheet to ensure that it is sensible. Data is validated as it is typed into a cell.
Validation checks are specified at the time that the spreadsheet file is created. Here are some common types of validation checks that can be carried out by spreadsheet software :
| Validation Checks | ||
| Presence Check | Checks that data has been entered into a cell and that it has not been left blank. | |
| Type Check | Checks that an entered value is of a particular type. e.g. check that age is numeric. | |
| Length Check | Checks than an entered value e.g. surname is no longer than a set number of characters. | |
| Range Check | Checks that an entered value falls within a particular range. For example the age of a person should be in the range 0 to 130 years. | |
| Format Check | Checks that an entered value has a particular format. e.g. a new-style car registration number should consist of a letter followed by 1 to 3 numbers followed by 3 letters. | |
| Table Lookup Check | Checks that an entered value is one of a pre-defined list of valid entries which should be allowed. | |
Spreadsheets are used for applications (jobs) which involve calculation or graph-plotting. Some example application areas are :
| Financial Modelling | Organisations like the treasury model mathematically the effect that changes in economic variables such as the rate of interest will have on the economy. Simple versions of such models can be set up using a spreadsheet. Such models are often known as simulations. |
| Optimisation Problems | Spreadsheet models can be used to find optimal solutions to problems. For example what should the dimensions of a can be to store a fixed volume of liquid at the cheapest possible price ? Or how many architects should be employed for how long to find the largest number of items at an archaeological site within a fixed budget ? |
| Book-Keeping | Spreadsheets can be used for general financial tasks such as stock control, payroll, profit calculations etc. |
| Presentations | Graphs produced using a spreadsheet can be incorporated into printed publications or presentations. |
Spreadsheet models (a type of simulation) can be used to investigate what happens when variables in a model are changed. For example here is a simple model of the cost of producing a packed lunch :
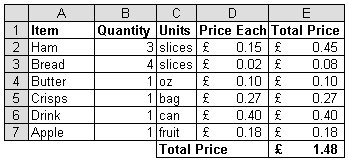
The model uses formulas to calculate the total cost of producing a packed lunch from the individual costs of the items and the quantities required. It could be used to answer questions such as :
| Question | How Answered |
| What would happen to the cost of a lunch if the number of slices of ham required fell to 2. | The number in cell B2 is changed from 3 to 2. |
| What would happen to the cost of a lunch if crisps rose in price from 27p to 29p ? | The number in cell D5 is changed from £0.27 to £0.29. |
| What would happen to the cost of a lunch if an apple was no longer required ? | The number in cell B7 is changed from 1 to 0 or row 7 is deleted. |
Because the values in column E are calculated using formulas when the values typed into the spreadsheet are changed the totals are automatically recalculated. It is for this reason that spreadsheets are often used to answer "what-would-happen-if" (or "what-if") problems. Once the formulas have been created, the effects of changing values can be determined easily and quickly.
Spreadsheets can be used to answer much more complicated questions. Typical "what-if" problems could be :
1.
| What would happen to the school tuck shop's profits if the cost of buying sweets rises by 10%?
|
| 2.
| If a company made two workers redundant, what would happen to the company's
wage bill and profits?
|
| 3.
| What would be the effect on an airline's profit if the number of passengers flying
with it rose by 50% as a result of a 15% reduction in ticket fares ?
|
| 4.
| What would be the effect on the economy of a 1% rise in the interest rate ?
| |
There are many reasons why you might want to use a spreadsheet to perform some calculations rather than carry them out by hand. Some good reasons to use a spreadsheet include :
1.
| If you have to carry out several calculations by hand (or using a calculator) then
it is easy to make a mistake. If you use a spreadsheet then, providing you get the
formulas right, the computer will not make any calculating mistakes.
|
| 2.
| Information presented using a spreadsheet is usually neater than handwritten
calculations. The results of such calculations can be easily graphed with a
spreadsheet.
|
| 3.
| Sometimes you have to perform the same calculation on a lot of data (e.g.
convert lots of different amounts from one currency to another) or on data that
changes frequently. Once you have set up the correct formulas the
spreadsheet can use them again and again on different sets if data.
|
| 4.
| Some calculations would be extremely difficult to perform by hand. For example can
you imagine the number of calculations that would have to be performed to predict
the effect of a rise in interest rates of 0.25% on the economy. If a spreadsheet
model is set up then you can simply change the interest rate and it will
automatically perform all the calculations to show you the predicted effect.
|
| |
You should follow these eight steps to help you design a spreadsheet :
| 1. | Decide why you are setting up the spreadsheet - why is it needed ? |
| 2. | Decide what outputs you want the spreadsheet to produce - what must it calculate ? |
| 3. | Use the information about the outputs you want to get to decide what inputs you must put into the spreadsheet. |
| 4. | Plan the calculations that you will need to perform with the inputs to work out the outputs. It may help to split the calculations up into different parts to make this stage easier. |
| 5. | Plan the layout of the spreadsheet including where information will be placed and how it will be formatted to make it easy to use. Consider how replication can be used to create the spreadsheet efficiently. |
| 6. | Plan any macros that you are going to create to automate tasks such as sorting. |
| 7. | If the spreadsheet you are using supports them decide what validation rules to use to ensure entered data is sensible. |
| 8. | Identify the data that you will use and the tests that you will perform to check the spreadsheet is working, and write this down in a test plan. |
What To Test
After you have created a spreadsheet you need to test it to ensure that it is working properly. There are three main areas that you need to test. They are :
| 1. | The most important thing to test is that the formulae in the spreadsheet produce the correct answers. |
| 2. | If you have carried out any validation you need to check that valid inputs are accepted and invalid inputs are rejected. |
| 3. | If you have created any macros you will need to test that these perform the correct actions at the correct times. |
There are two different methods that you can use to test your formulae. They are :
The Test Plan
You should created a test plan that lists all of the tests you will carry out on your spreadsheet. In the test plan you should state :
If your spreadsheet is being produced as a piece of coursework it is a good idea to give each test a number.This will allow you to link the tests in your plan to evidence you later produce to show that you have carried them out.
Test Results
When you carry out the tests of your spreadsheet you need to check that the actual results you obtain match the results you expected to get. If they do not then you will need to work out why not and try to correct the problem. You will then need to carry out the test again.
If your spreadsheet is being produced as a piece of coursework you should collect evidence to show that you have carried out the tests and cross-reference this evidence to the descriptions of the tests in the test plan.
1.
| A spreadsheet is a package used for performing
calculations and drawing graphs.
|
| 2.
| A spreadsheet is divided into cells.
Rows run across the screen and
columns run down the screen. Each cell
has a name called a cell reference.
A group of cells is known as a range.
|
| 3.
| Numbers, labels and formulas are the three different types of information that
you can put into a cell.
|
| 4.
| Formulas such as =A1+B1, =A7*A8/100 can be used to get the spreadsheet to
perform calculations.
|
| 5.
| Functions such as SUM, MIN, RAND can perform calculations on ranges of data.
|
| 6.
| Most spreadsheets contain many functions. They are divided up into classes such
as mathematical, financial, statistical,
condition and database functions.
|
| 7.
| You can replicate (copy) formulas using Fill Down, Fill Right and Copy and Paste.
Relative references change as they are copied.
Absolute references do not change
as they are copied.
|
| 8.
| A series of numbers such as 1,3,5,7 can be generated using
fill series.
|
| 9.
| A condition function like IF can use data in the spreadsheet to make a decision.
|
| 10.
| Database lookup functions can search through a
table in a spreadsheet as if it were a database.
|
| 11.
| Data in a spreadsheet can be sorted into a particular order.
|
| 12.
| Data in spreadsheet cells can be formatted (e.g. bolded, underlined, left and right justified). Numbers can be
formatted to fixed numbers of decimal places or to be displayed as currency.
|
| 13.
| Extra rows and columns can be added to a spreadsheet and unwanted ones can be deleted. The width of columns
and height of rows can be adjusted to fit the data in them.
|
| 14.
| Spreadsheet data can be used to plot graphs.
|
| 15.
| Some spreadsheets will let you create macros to automate common tasks.
|
| 16.
| Some spreadsheets can validate data as is entered to ensure it is sensible.
|
| 17.
| Typical applications of spreadsheets include simulations,
optimisation and book-keeping.
|
| 18.
| Spreadsheet can be used to answer what-if problems
of the form "what would happen to X if y changed ?".
|
| 19.
| Spreadsheets are useful because, once you have set up the
formulas, they will carry out calculations quickly without making calculating errors.
The results of spreadsheets calculations can be presented more neatly than
handwritten ones and as charts. If you change any data the calculations will be
automatically carried out again, so spreadsheets are particularly useful if the
data is likely to change or if the same calculations have to be performed
on several sets of data. For some very complicated simulations it would be
impossible to perform all the necessary calculations by hand.
|
| 20.
| It is important that you design and test properly any spreadsheets that you create. Comparing the output of a spreadsheet with manual calculations using the data or
noting the effects of changing the data in the spreadsheet are both methods of testing
a spreadsheet.
| |
Section 14 : Charting |
Numerical information can often be presented more simply as a chart (or graph) than as a table of numbers. Patterns in a series of numbers can be identified more easily when the numbers are represented visually. Charts can be produced using a specific charting package or by a spreadsheet.
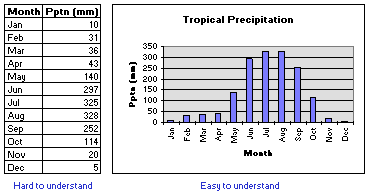
A computer package can automatically draw a chart from a table of numbers that you have entered or calculated. You will need to decide on what type of chart you want and how the axis should be set up and labelled. If you change any of the numbers in the table then the computer will update the chart. A finished chart could be printed or included in a desktop published document.
There are many different types of chart such as pie charts, bar charts, line charts and scatter graphs. The most appropriate type of chart to use will depend upon what the data is that you are using and what you are trying to find out or show.
| Pie Chart | |
| Purpose |  |
| Used to show how a quantity is divided up between a number of options. | |
| Example Use | |
| Show what proportion of people travel to school by each of five different methods e.g. bus, car, walk, bike, other. | |
| Line Chart | |
| Purpose |  |
| Used to show how a continuous quantity changes over time. | |
| Example Use | |
| Chart of how the temperature changes throughout the year. | |
| Bar Chart | |
| Purpose |  |
| Used to show how frequently a particular option is selected from a list. | |
| Example Use | |
| Chart showing how many people choose to shop at each of three different locations. | |
| Scatter Graph | |
| Purpose |  |
| Used to investigate relationships between two sets of data. A best fit line or curve is often drawn to show a relationship if one exists. The package may be able to produce this line for you. | |
| Example Use | |
| Investigate if taller people have bigger feet. | |
Most charting packages will produce other types of chart such as stacked bar charts or 3 dimensional pie charts. When choosing the best type of chart to use the most important point to consider is that the information can be clearly understood.
Once a chart has been created it is important that appropriate labels are added to it so that it is clear what the chart shows. All charts need a title to state what the purpose of the chart is.

If a chart has axis then each axis should have also a label. The axis running along the bottom of the chart is the X axis and the axis running up the side of the chart is the Y axis. An axis label should clearly state what the axis measures and what units have been used on the scale.
When you draw a chart by hand you need to decide what range the axis will cover, i.e. what will be the lowest value you will plot on the axis and what will be the highest value. You also need to decide how you will divide the axis up, i.e. into steps of 5, 10, 50 etc. This axis has a range of 100 to 200 and goes up in steps of 50 :
![]()
If you use a charting package to produce a chart then it will automatically set the axis ranges and steps for you by looking at the data you have entered. However in some circumstances you may want to adjust these manually. Most charting packages will let you do this. You need to be careful that when you adjust the axis ranges you do not move any data points off the chart.
Sometimes you may want to show more than one set of data on the same chart. For example :
If this is the case then both sets of data are plotted on the same chart using different colours or patterns to distinguish them. A legend or key is then added to identify the two sets of data.

1. | Numerical information can usually be more
easily understood if it is presented as a chart
(or graph).
|
| 2. | Charts can be created in a specialised
charting package or a spreadsheet.
|
| 3. | The most popular types of chart are :
| |
| Type | Use | |
| Pie Chart | Shows how a quantity is divided up between a number of options. | |
| Line Chart | Shows how a continuous quantity changes over time. | |
| Bar Chart | Shows how frequently a particular option is selected from a list. | |
| Scatter Graph | Used to investigate relationships between two sets of data. | |
4. | A chart should have a main title and titles on the X and Y axis.
|
| 5. | The
scales on the axis are usually
set automatically by the charting package but can be adjusted.
|
| 6. | A
legend can be use to identify two sets of data plotted on the
same chart.
| |
Section 15 : Web Design |
The World Wide Web (or simply Web) is the most popular service on the Internet. The development of the web was partly responsible for the rapid increase in the number of people who used the Internet in the late 1990s. The World Wide Web consists of millions of different sites, each of which contains information. Each site is identified by a unique address called a Uniform Resource Locator or URL.
The information at a site is stored in the form of pages which can contain text, pictures, sound and video. Because web pages can contain so many different types of information they can be designed to be attractive, informative and interesting.
The different pages at a site can be linked together so that the user can move easily between them. A hyperlink is placed on a page to create a link to another page. Clicking on a hyperlink will move you to the page that the link joins to. Links can be made between pages at the same site and pages at different sites.
To view the information at a web site you must use a browser package. Web pages are stored in a special code called Hypertext Markup Language or HTML. To create a page you must either :
1. | Write the HTML code
yourself. This can be very complicated. You need to know all of the valid codes that
can be used and type them exactly.
| 2. | Use a web design
package. The package will work like a desktop publisher.
You will be able to use a
range of tools to design the page on screen. The package will produce the HTML code
required for the page from your design.
| |
For must users the best option is to use a web design package. This will do most of the technical work for you. You simply design your page on the screen and the web design package creates the HTML code for the page you have made.
Whilst you are developing a web site you will probably store it on the hard disk of your computer. When it is complete you will need to upload it onto a web server so that other people can access it.
A web site is usually made up of many pages. The first steps in designing a web site are to decide :
1. | What the purpose
of the web site is.
| 2. | What individual pages
will be needed to build the site.
| 3. | What information will
appear on each page.
| |
You will then need to decide how the pages will be linked together. You can use hyperlinks so that a person viewing the web site can move between the individual pages. You can also link your web site to other sites.
One way to show how your web site will be organised is to draw a diagram showing what will be on each page and how the pages will be linked. The diagram below shows how a web site for a football club could be organised.
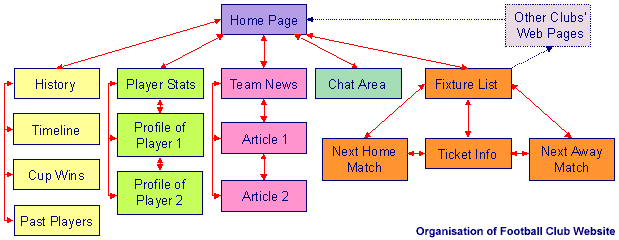
The main page that the user starts at is the home page. The web site has been divided into five different sections which are club history, player statistics, team news, chat area and fixtures. In each section there are a number of pages. The arrows indicate links between the pages. The club will also make links to the web sites of other clubs that it will be playing. It hopes that in return these other clubs will create links to its web site.
Once the structure of the web site has been decided, you can start to create the individual pages. If there are a lot of pages to make then different people could work on each one. It is a good idea to make all of the pages on a site look similar. You can do this by using a standard page layout for each page.
Most web sites are made up of many pages. It is a good idea to make all of the pages at a site look similar. This means that a person viewing the pages can tell that they are part of the same site.
You can make a page look consistent by using the same colours and styles for the text and the same background on each page. This diagram shows an example layout for a web page :

The designer of the web page has made these decisions about its layout :
The basic layout of each web page on the site will be the same as this. Some pages will have more or less pictures. Some may have more options and some will have several headings, but they will all conform to the design points listed above.
Every time you create a web page you can specify what the background will be like, what the title will be and what normal text and hyperlinks will look like.
Background
You can choose a background colour for a page or you can put an image in the background. If you choose to use an image in the background then it should be a small one. If the background image is too large it will take a long time to load the page. Many web users will not be prepared to wait. The image should also be simple so that it does not interfere with the text that appears in front of it.

The background image is repeated up and down the page to fill up the whole screen. This is called tiling.
Page Title
A web page needs a title. This does not appear on the page itself. Instead it is displayed in the title bar of the web browser when the page is viewed.
Default Colours
You can set the default colours that should be used on a page. As well as the colour of the background you can also specify :
When you produce a word processed document you can choose what fonts and sizes to use from a list of fonts that are installed on your computer. You can get your document to look exactly how you want it to.
Designing a web page is more difficult. This is because different computers have different fonts installed. If you use a particular font on a page you can not be sure that a person reading the page will have the same font. Web design packages use two different approaches to overcome this problem.
| Styles | A range of pre-defined styles which each have a name can be selected. As well as normal text there are six types of heading and several other styles. When you design a web page you use these styles. You do not know exactly how the text will appear when it is looked at but you know that heading style one will stand out more than heading style two and so on. |
 |
|
| Font Matching | Using font matching you can pick the font and font size that you want to use for your text from the fonts that are installed on your computer. If a person who looks at your web page does not have the same font his web browser will use the most similar font that is available. To increase the probability that another person has the same font as you it is a good idea to only use common fonts such as Times New Roman or Arial. Font matching only works with newer web browsers. |
Font Style
Each font can have a range of extra styles applied to it. The three common styles that can be used on a web page are :
![]()
Underline style can also be used on web pages but this is not normally done. This is because hyperlinks are underlined so underlined text could easily be mistaken for a hyperlink.
Alignment
Alignment describes the position at which text appears on a line on the page. On a web page, text can be aligned to the left, center or right of the page.
Font Colour
The colour of text can be specified. Most web pages make use of lots of colour because they are displayed on monitors which can easily show colour. If it is likely that your page will be printed out then you should check how the colours you have chosen look on a black and white printout as some colours do not show up very well.
Web design packages do not usually include a facility to let you create images. Instead you must obtain an image from another piece of software and bring this into the web design package. This is known as importing. The three most likely sources of images are :
Images take up a lot more storage space than text does. When a person looks at a web page the files that make up the page must be transferred over the Internet to his computer. If a web page contains an image it will take a lot longer to access than a text only page.
To speed up page loading, images on a web page must be stored in one of two special formats. These formats are GIF and JPEG. Both formats compress the image data so that it can be loaded more quickly.
| GIF | A GIF file is a compressed graphics file. GIF files store information about sequences of pixels. An image saved as a GIF file will look exactly the same as the original image. GIF files usually take up more space than JPEG files. GIF files are often used for banners and icons. |
| JPEG | JPEG files are highly compressed graphics files. JPEG files can store an image in a very small space. However some detail can be lost from an image when it is stored as a JPEG file. For this reason photographs are usually stored as image files but icons and banners can not be stored in this format. |
Images in other formats such as bitmaps must be converted to one of these formats before they are put on a web page. A web design package will probably do this automatically.
A hyperlink is a connection between two web pages. If you select a hyperlink on a page then you will be taken to the page that the hyperlink joins to. Hyperlinks can be represented as either text or a small image known as an icon.
 | |
| A Text Hyperlink | An Icon Hyperlink |
This diagram shows three web pages which are part of a site about the North West of England.

Clicking on the Manchester hyperlink on the main North West page would take you to the page about Manchester. Clicking on the cotton hyperlink would tke you to the page about cotton.
Most web browsers display links that you have visited in a different colour to links that you have not visited. Unvisited links are normally blue.
![]()
To create a hyperlink on a web page you normally type the text that you want the user to click on or import the image for the icon. Then you select the text or icon and identify which page the link goes to.
Sometimes when you click on a hyperlink it does not work because the page that it should link to does not exist. Most web design packages will automatically test the web site that you create to make sure that all of the links work.
A hot spot is an area of an image which acts as a hyperlink. When a person clicks on a hot spot a hyperlink is followed to another page. The person viewing the web page can not see where the hot spots are but when the mouse pointer moves over a hot spot it will change shape.
This image of a computer could be used on a web site about computers. It contains five hot spots but they are invisible.

This is the same image but with the hot spots highlighted in colour. They would not normally be visible.
If the user clicked on the image over the light blue hot spot he would be taken to a page about monitors. Clicking over the yellow hot spot would take the user to a page about keyboards.
Hot spots are either rectangular or elliptical in shape. To create a hot spot on an image you simply need to select the area that the hot spot should cover and then specify what page should be loaded when the mouse is clicked in this area. You can create any number of hot spots on an image but they should not overlap with each other.
Tables can be used to set data out neatly like this :
| Model | Processor Speed | RAM Capacity | HDD Capacity |
| Fasta | 1000Mhz | 256Mb | 18Gb |
| Moderata | 500Mhz | 64Mb | 6Gb |
| Slowa | 66Mhz | 8Mb | 2Gb |
When you create a table you specify :
The height of each cell will automatically adjust so that the information that you type into it will fit. It is also possible to merge adjacent cells in a table together to form merged cells which cover more than one row or column.
| Merged Cells |
|||
| Merged Cells | |||
Using Tables For Page Layout
Tables can also be used for a second purpose. When you create a web page you can not simply position text and pictures wherever you want on the page as you could with a desktop publisher. If you want to create complicated page layouts with multiple columns of text then you can use tables to achieve this effect.
Suppose that you wanted to create a page like this :
This can be achieved by creating a table and merging the cells in the table together to form the shapes required for the different sections of the page.

The information that is to appear on the page can be typed into the cells of the table. You can place any type of information, including pictures and other tables in a cell.
Frames are used to create web pages where one section of the page can be changed independently of another section.
This is often done when web sites have a navigation panel at the side or bottom of the page. The panel contains icons which can be used to switch between the pages on the site. Selecting one of the icons will change the page that is displayed on the main part of the screen, but the navigation panel will remain the same.

Each frame is identified by a name. When a hyperlink is created the web designer can specify which of the frames to load the link page into when it is selected.
A form is used to obtain feedback from the people who use a website. Forms can be used to gather people's opinions about a site or to gather information that a company or organisation might want.
Forms can be built up from several different types of controls. Some of the most important ones are shown in this table.
| Short Text Entry | A short text entry box lets the user type in information. The web designer can specify the maximum number of characters that can be typed. | |
| Long Text Entry | A long text entry box lets the user type in information. The text input area can be scrolled to allow a lot of text to be entered. | |
| Radio Button | Radio buttons let the user select one or more options from a list. The web designer chooses how many options can be picked at once. | |
| List Box | A list box lets the user choose one option from a list. | |
| Push Buttons | Buttons are used to start actions such as sending the contents of the form or clearing the form. |
When a form has been completed the data that the user has entered must be sent to the person who runs the website. This can be done by transmission by email or by saving the form contents to a file on a web server.
There are many different technologies which can be used to enhanced a web page. Some of these will only work with newer web browsers. Others require an extra piece of software called a plug-in to be installed in addition to the browser. Some of these additional technologies are listed below.
| Javascript | Javascript is a simple programming language. Programs (or scripts) written in this language are often used to validate data entered onto a form before it is sent. |
| Java | Java is a complete programming language. Programs written in Java can be used in a web browser on any type of computer. |
| Animated GIFs | An animated GIF is a sequence of images which are displayed one after the other in rapid succession. This has the effect of displaying an animation. |
| Sound | Sound can be added to web pages. This can be in the form of music playing in the background whilst a page is displayed or noises which are made when options are selected. |
| Video | There are many different systems which can be used to display video over the Internet. Videos require a lot of storage space and take a long time to transmit. Therefore video over the Internet is usually poor quality with a small image size and just a few frames per second. Good quality video can be broadcast with a fast broadband connection. |
Whilst you are developing a web site you will probably store it on the hard disk of your computer. When it is complete you will need to upload it onto a web server so that other people can access it.
A web server is a computer which stores web pages. It responds to requests to view pages from other computers by sending the required pages to them. Many web servers are connected to the Internet.
Some web servers are not connected to the Internet but are connected to a private network that is owned by a company. If this is the case then only people within the company will be able to view the pages on the server. This is known as an Intranet.
The process of transferring your web site onto a web server is known as uploading. A service called File Transfer Protocol (FTP) is used for this purpose.
1. | The
World Wide Web (or simply Web) is the most popular
service on the Internet.
|
| 2. | Each site on the World Wide Web is
identified by a unique address called a Uniform Resource Locator or URL.
|
| 3. | A web site is made up of pages. Pages
are joined together by hyperlinks.
|
| 4. | To view a web site you need to use a web browser package.
|
| 5. | Web pages are stored in a language
called HTML. To produce
a web page you can either write the HTML code yourself or use a web design package.
|
| 6. | The
structure of a web site refers to the organisation of
the pages at the site and which pages are linked to which other pages.
|
| 7. | Usually all of the pages that are part
of a web site have the same page layout. They will share
a common background, colour scheme, text styles etc.
|
| 8. | It is possible to choose the
fonts
that you want to use on a web page, but these may not be present on every computer.
Often special text styles are used instead.
|
| 9. | Images can be included in web pages.
These need to be fairly small so that they do not take too long to download. Images on web
pages are usually stored in
compressed
GIF or
JPEG format.
|
| 10. | Hotspots
can be created on images. A hotspot is an area of an image which acts as a
hyperlink.
|
| 11. | Tables
can be included in web pages. They are often used to create complicated page layouts such as
multi-column pages.
|
| 12. | A page can be divided up into
frames so that the contents of one section of the page can
be changed independently of the other section(s).
|
| 13. | A form
can be included on a web site. The form can be filled in by a person visiting the site and the
information entered on it can be sent back to the page's owner.
|
| 14. |
Advanced tools such as Javascript, Java and
Video can be used to enhance the appearance of a web page.
|
| 15. | Whilst you are developing a web site
you will probably store it on the hard disk of your computer. When it is complete you will
need to upload it onto a web server so that other people
can access it.
File Transfer Protocol (FTP) is
usually used for this purpose.
| |
Section 16 : Multimedia |
The term multimedia literally means using more than one medium. In the context of computer software the term multimedia means that information is conveyed using more than one method. Methods widely used to convey information include :
The use of advanced methods of information display such as video and music can significantly enhance the quality of computer packages and presentations.
Text and drawings can be displayed by practically any computer. To play sound and music a computer may need to have a sound card fitted. To play video a computer will need a fast microprocessor and quite a lot of RAM.
Text and drawings take up very little storage space. Sound takes up more storage space and video needs a lot of storage space. Because multimedia information requires a lot of storage space packages which use multimedia are usually supplied on CD-ROM or DVD. If you create your own multimedia work then you will need a lot of free space on your hard disk.
Here are some common uses of multimedia presentations.
Reference CD-ROMs
Reference works such as encyclopaedias are now available on CD-ROM. Tens of thousands of pages of written information can be put onto a single CD-ROM disk. Videos and animations can be used to explain important concepts and show important events. Sound can be used to play famous pieces of music and important speeches. Most reference CD-ROMS include a search facility where you can type in a description of what you want to find out about and the computer will search the encyclopaedia for you. A CD-ROM encyclopaedia is usually much cheaper to purchase than an equivalent encyclopaedia provided as a set of books.
The Internet
Information displayed on the World Wide Web is usually presented as a mixture of text and pictures. Sometimes sound is also used. Video can be incorporated into World Wide Web pages but this is not done very often. As video files are very large it is usually too expensive to transmit them over the Internet because it would take a long time.
Presentations
A multimedia authoring package lets the user put together many different types of information to make a single presentation. Multimedia authoring packages are rather like desktop publishers but they let the user include extra types of information such as videos which could not be included in a desktop published page. It does not make sense to print out multimedia presentations like this (you can not see sound) so multimedia presentations are usually viewed either on a computer monitor or using a projector.
Here are some common uses of multimedia presentations :
| Company Promotion | Companies often have to make presentations about themselves to potential customers. Many companies do this using multimedia presentations. A salesman will talk the customers through the presentation. Diagrams can be used to present information such as profit figures as graphs. Videos can be used to present information about company products etc. |
| Training | Another type of presentation lets the user decide what information to see and in what order to see the information. Using this type of presentation is like viewing a site on the World Wide Web. This type of presentation is often used to train people. In the first stage of training users can watch a training video. They can then try out their new knowledge by selecting options within the presentation to see what the effects of making different decisions might be. |
| Public Information Systems | Public information systems such as those provided in Tourist Information Offices and Libraries are usually multimedia presentations. The public find it much easier to interact with systems that use graphics and sound rather than just text. Often touch sensitive monitors are used with these systems. Members of the public can choose options to find out about local attractions, public transport etc. |
Computer Games
Computer games have always made use of animation. Many games now include video sequences and advanced sound effects as well.
1.
| Multimedia means that information is conveyed using more than one method, e.g.
text, sound, video and pictures.
|
| 2.
| Multimedia applications place extra demands on computer
hardware. Most multimedia
computers need to have :
|
|
Section 17 : Operating Systems |
The operating system is a very special piece of software. All the other applications software such as databases and spreadsheets communicate with the computer hardware through the operating system. The operating system controls the overall operation of the computer. It is the most important part of the systems software.
An operating system (or OS) is a computer program which controls the entire operation of the computer. Computer software applications communicate with the computer hardware via the operating system.
Example Operating Systems
When you buy a computer it is usually supplied with an operating system already installed. You will not be able to use a computer without an operating system. Different operating systems are available for different types of computer and different purposes. Some popular operating systems are :
| Operating System | Description |
| MS-DOS® | A simple, command-driven operating system used on personal computers. |
| Windows 2000® | A WIMP based operating system used on most PC computers. |
| UNIX | A multi-user, multi-computer operating system which is used on large mainframe computers and networks. |
The choice of operating system will affect how a computer works. It will probably determine the type of user interface (command line, menu driven or graphical) that the computer uses and the types of processing (batch, transaction or real-time) that the computer can carry out.
Because an application such as a spreadsheet works by communicating with the operating system the application will probably only work with one particular operating system. If you buy Microsoft® Works® for Windows® 2000 it will only operate on computers with the Windows 2000 operating system. If you want to use Microsoft Works with the MS-DOS® operating system you will have to buy a different version of the application.
MS-DOS®, Windows® 2000 and Microsoft® Works® are registered trademarks of Microsoft Corporation in the United States and other countries.
There are several tasks which are performed by practically all operating systems, regardless of the complexity of the computer the operating system is being used on. These tasks include :
The range of tasks that an operating system performs increases if the computer using the operating system is on a network or if the operating system is a multi-tasking or multi-user operating system.
Managing Communications Between Computer and Connected Peripherals
Many peripherals can be connected to a computer. It is the job of the operating system to manage the communication between the application programs that are running on the computer and the peripheral devices. For example the operating system will :
There has to be some control over these activities to make sure that problems do not occur. Consider what might happen if a computer program was trying to load a file from a floppy disk and, at the same time, another program was trying to save data. Therefore the operating system manages all of these tasks. If, for example, a program wants to save or print a file it must send a request to the operating system asking it to do so. The operating system will then carry out the task.
Provision of a User Interface
The operating system will provide a user interface that the user uses to interact with the computer. Modern operating systems usually provide a graphical user interface. Alternatives to this are command line and menu driven interfaces.
Allocation of Computer Memory
Computer memory must be allocated to (divided between) the different tasks that the computer is performing. Even if your computer appears to be doing only one task such as word processing there will be several different items to which memory must be allocated. For example memory would have to be allocated to storing the word processor program, storing your word processed document and storing a copy of the image that is being displayed on the monitor. And of course the operating system itself will also use up some memory.
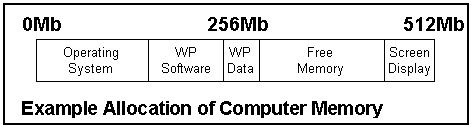
Organising Data on Backing Storage Devices
Work and programs must be saved on a backing storage device so that they can be kept when a computer is turned off. The operating system is responsible for organising data on backing storage devices. Work and programs are saved as files which must be organised so that they can be found and loaded when required. Each file is identified by a filename.
Most operating systems divide a backing storage device up into directories (also known as folders). Files can be stored within each directory. The diagram below shows how data has been organised on a particular hard disk drive.

The user has chosen the names of the directories and files but the operating system has decided where and how to store the files on the disk. The operating system has ensured that no two files are stored in the same place on the disk and that rules such as having a maximum length for filenames have been enforced.
MS-DOS®, Windows® 2000 and Microsoft® Works® are registered trademarks of Microsoft Corporation in the United States and other countries.
The most basic type of operating system can only carry out one task at a time and can only be used by one person at a time. Sometimes a more sophisticated operating system is required. The three most common advanced operating systems are :
| Operating System | Use | |
| Network OS | Network operating systems are used on computers which are connected to a network to manage the security of the network. | |
| Multi-Tasking OS | A multi-tasking operating system can appear to carry out more than one task at the same time. | |
| Multi-User OS | A multi-user operating system is used on a mainframe or minicomputer which may be used by more than one person at a time. | |
These operating systems are more complicated and may require faster hardware and more memory to work than more basic operating systems.
Operating systems that are used on computers connected to networks usually have to carry out some additional tasks. Probably the most important of these is managing system security. Important aspects of systems security that an operating system might manage are :
Making a user log on with a user name and password before a computer can be used.
Allow a user on one computer to access files stored on another computer (e.g. a server).
Controlling who has access to which files.
Keeping a log of all of the files that a user changes.
Automatically backing up important files.
A multi-tasking operating system is capable of appearing to carry out more than one task at a time.
Windows® 2000 and UNIX®; are examples of multi-tasking operating systems. If you have a computer with a multi-tasking OS you could be using a spreadsheet and a word processor at the same time. You could also have the computer testing every five minutes to see if you had any new email and displaying a television programme on screen. Most multi-tasking operating systems have a WIMP user interface with each task being displayed in its own window.
In reality because the computer only has one microprocessor it can only be doing one thing at once. The computer fools you into thinking it is doing more than one task at once by dividing the processor time up between each of the tasks. Each task is given a small amount of processor time in turn. The amount of time allocated to a task is known as a time slice. These time slices are very short, usually less that 1/1000 of a second. Because the slices are so small, the user is fooled into thinking that the computer is doing many things at once.
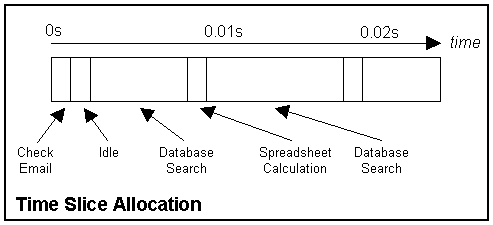
The time can be allocated to the different tasks on an equal basis (each tasks gets the same amount of time) or on a priority basis with more important or more urgent tasks getting most time. Commonly the task that the user is currently working on (such as entering data into a spreadsheet) has the highest priority. It is allowed exclusive use of the processor whenever it wants it and is known as the foreground job. Other less urgent tasks such as sending data to a printer are only permitted to use the processor when the foreground job does not need it. These tasks are known as background jobs.
If an operating system is carrying out more than one task then the job of allocating memory also becomes harder because the computer’s memory must be allocated between the tasks.
Multi-tasking operating systems are also sometimes known as multi-program operating systems.
Windows® 2000 is a registered trademark of Microsoft Corporation in the United States and other countries.
Multi-user operating systems are used on large mainframe computers. A mainframe computer system has one very powerful processing unit which may contain many microprocessors. Many users will all share this processing unit. They use terminals (a keyboard and a monitor) to access the mainframe computer.
A multi-user operating system lets more that one user work on a mainframe computer at the same time.
A multi-user operating system allocates the CPU time of the mainframe computer between the different users. Each user in turn is given a small time slice of the CPU time. Because these time slices are very small the users believe that they are all using the mainframe at the same time.
This diagram shows how a mainframe computer with four terminals connected to it divides its processing time up.
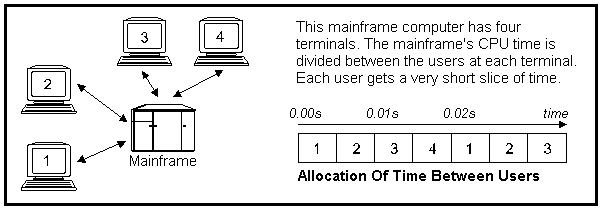
Time can be shared equally between each user or can be allocated to users using a priority system so that some users get more time than others. Multi-user operating systems rely on having very powerful mainframe computers to process data.
Sometimes operating systems are also classified according to the types of processing that can be carried out by software packages running on them. As well as the categories
of network, multi-tasking and multi-user a particular operating system could fall into these four categories :
| OS Type | Description |
| Batch | A batch operating system can perform batch processing of data. Data to be processed is grouped together into batches. No data is processed until a complete batch has been collected, then all of the data in a batch is processed in one go. There may be a long time delay between data being input into the system and the data being processed. Each task that is waiting to be carried out is known as a job. |
| Interactive | An interactive operating system carries out a dialogue with the user. Once the user has entered a command or selected an option the operating system will process the user's input and react with some output before the user can input any more data. Interactive operating systems can carry out transaction processing. |
| On-Line | An on-line operating system allows the user of a computer to interact directly with another central computer. On-line operating systems are commonly used by transaction processing systems that require many users at different computers to interact with a central computer. An on-line operating system could be used in a chain of travel agents where computers located at many branches make bookings on one central computer. |
| Real Time | A real time operating system can perform real time processing of data. This means it can process data extremely quickly to meet a real world deadline. Real time operating systems are usually used in control systems and embedded systems. |
Note that a particular operating system could fall into more than one category. e.g. it could be network, multi-tasking, interactive and on-line.
1.
| The operating system (OS) is a computer
program which
controls the entire operation of the computer. It is the most important piece of systems software.
|
| 2.
| MS-DOS®, Windows 2000® and UNIX are operating systems.
|
| 3.
| The operating system will determine the type of user interface and types of
processing a computer can use.
|
| 4.
| All operating systems perform these tasks :
|
| 5.
| Data saved on a backing storage device is usually
organised hierarchially in a
directory tree.
Files are created within
directories. Directories can also be created
within other directories. A directory inside another directory is a
subdirectory.
|
| 6.
| There are three types of advanced operating system that can perform additional functions. These are : |
| 7.
| Operating systems are also sometimes classified according to the types of processing they can carry out. These additional classifications are : |
| 8.
| A particular operating system might fall into several categories. For example it could be a multi-tasking, network, interactive OS.
| | |||||||||||||||||||||||||||
MS-DOS® and Windows® 2000 are registered trademarks of Microsoft Corporation in the United States and other countries.
Section 18 : Other Software |
Most people use standard generic packages such as a word processor or database for much of their work. Many other generic or application specific packages are available to carry out particular tasks. Here are some examples :
| Games | Games are programs which let people play in situations that they are unlikely to encounter in everyday life. | |
| Teaching | Computer Aided Learning and Home/Distance Learning systems can help people to learn at their own pace. | |
| Geographical Information Systems (GIS) | Geographical Information Systems plot stored data onto maps so that it can be easily analysed and interpreted. | |
| Expert Systems | An expert system is an artificially intelligent computer system that stores and can apply knowledge about a particular area of human expertise. |
The first computer games could only be played in an arcade on specially designed arcade machines, but now games can be played in several different ways :
Games usually include very high quality graphics and animation or video, together with excellent music and sound. Because these things require a lot of storage space most games are supplied on CD-ROM or DVD. To play the latest games on a desktop computer you usually need to have a lot of RAM and a fast processor. Most games are easier to play if you have an input device such as a joystick in addition to your mouse and keyboard.
In many games it is possible to play against the computer as an opponent. The computer may use a form of artificial intelligence to decide how to play. Newer games also let you compete against other people in different locations across the world via the Internet.
Some people believe that spending a lot of time playing computer games is a bad thing. They think that people who spend too long playing games don't do enough physical exercise to keep them healthy and may miss out on the opportunity to socialise with others. There are also concerns that peoples behaviour may be affected by the amount of violence contained in some games. An age rating system, designed to stop young children obtaining very violent games has been introduced.
Computer software can assist people to learn in many different ways. Two of the most significant are by using Computer Aided Learning (CAL) software and through Home/Distance Learning.
Computer Aided Learning (CAL)
A computer aided learning system teaches a user by presenting her with material to learn then assessing how well the material has been understood :
Home/Distance Learning
The widespread availability of computers in the home and fast broadband Internet links means that it is possible for people to study at home, with course material being delivered to them across the Internet.
This type of learning is particular suitable for people who live in remote communities, who find it difficult to travel to a college or who move around frequently.
Advantages of using Computerised Learning Systems
There are several advantages to using a computerised learning system, including :
There is still however some way to go in developing these systems. Some current computer aided learning packages make fairly basic assessments of the student's knowledge. Additionally computer aided learning systems are inflexible and lack the prsonal touch of a teacher or lecturer.
A Geographical Information System (GIS) presents stored data graphically on a map. The most common use of a geographical information system is as part of an in-car satellite navigation (SatNav) system, used to give a driver directions to get to his destination.
Satellite Navigation (SatNav)
A satellite navigation system consists of a receiver, a computer, a CD-ROM or DVD-ROM drive, an LCD monitor and a keyboard or remote control.
The receiver receives signals from a network of satellites called Global Positioning Satellites (GPS). From these the computer system can work out the location of the car. Maps are stored on a CD or DVD and based on the position of the car the computer can load the correct map and display it on the monitor with the car's position indicated.
Before setting out on a journey the driver can enter the name or postcode of the place that he is travelling to. The computer can locate the destination on the map and work out the best route for the driver to take. As the journey progresses the monitor will be used to indicate when the driver should turn onto another road. Directions may also be announced through speakers using speech synthesis so that the driver does not have to take his eyes off the road.
A satellite navigation system may also be linked to a traffic information system which can receive information about traffic jams and roadworks by radio. If a road involved in a journey is busy the computer system will be able to automatically change the recommended route to minimise the delay.
Other Geographical Information Systems
Geographical information systems can also be used to help analyse data by plotting it on a map. For example :
All of these tasks are made easier by seeing the data viewed on a map rather than as a list in a table. Most geographical information systems will be able to display a map at different levels of magnification so that as much or as litte detail as is required can be seen.
An expert system is an artificially intelligent computer system that stores and can apply knowledge about a particular area of human expertise. Expert systems store data collected from human experts in a knowledge base. An inference engine is used to apply this knowledge to solve problems posed by the user. Most expert systems ask the user questions and then suggest a conclusion to the user, based on the answers given to these questions. An expert system may be able to learn from experience, developing new knowledge or modifying existing knowledge based upon how accurate its conclusions have proved to be in the past.
The knowledge base is generally composed of rules that form conclusions based on the inputs made by the user. A simple example rule might be :
IF the person is aged 60 or over AND is female THEN she is entitled to a pension
An expert system will usually require many inputs and apply many rules before offering a possible conclusion to a user. The expert system may change the questions that it asks the user, based on the answers entered to previous questions. Here are some example uses that expert systems can be put to :
| Example | Description |
| Medical Diagnosis | The task of identifying the cause of a patient's symptoms is normally carried out by a doctor. However in some areas and countries there is a shortage of doctors, and although doctors have good general diagnostic skills it is not possible for each doctor to be an expert in every field of medicine. An expert system can be used to help diagnose a patient's illness by asking the patient questions about the symptoms. A knowledge base can then be used to identify likely causes. The expert system can benefit from the knowledge of many doctors. However, unlike a real doctor it can not see the patient's symptoms for itself. Instead it relies on the patient to describe their own symptoms. |
| Customer Technical Support | If you experience a problem with a computer system you will probably need to get support from the company that made it. Usually this is done by telephoning a central call centre. The staff at the call centre will have some technical knowledge but it is unlikley that they will have a detailed knowledge of every computer that the company has ever made. Therefore they will probably use an expert system to help answer enquiries. The expert system will be able to store detailed knowedge about every product and add to its knowledge base by learning what solutions have worked for particular problems in the past. This will enable members of staff who don't know very much about a particular product to help users solve problems with it. The member of staff will ask the customer questions, prompted by the expert system and the system will attempt to diagnose likely causes and appropriate courses of action based on the customer's answers. The expert system will help the company serve its customers better but if a problem occurs which has never been encountered before a human expert may need to investigate the cause. |
Expert systems are useful because
However an expert system is only as good as the knowledge it contains, and expert systems may not recognise unusual situations that a human expert would spot.
1. | Games are programs which let people play in situations that they are unlikely to encounter in everyday life :
|
|
Section 19 : Comms Methods |
Communicating is tranferring information from one person or location to another. There are many different methods that can be used to communicate information. The best method to use on a particular occasion will depend upon factors such as :
Communications systems can be classified as being either private or broadcast. Private systems are used for private communications between a small number of people. Broadcast systems allow one person to send the same information to lots of people at the same time. Some of the most common communication systems are listed below.
| Private Communications Systems | |
| Post | |
| Telephone | |
| Cellular Telephone | |
| Fax | |
| Video Conferencing | |
| Broadcast Communications Systems | |
| Teletext | |
| Digital TV | |
Data can be communicated directly between computers through a computer network or using a modem or ISDN.
The traditional postal system can be used to deliver letters and parcels to almost anywhere in the world. This is because a postal system is simple to operate and requires virtually no modern technology to function.
An address written on a package is used to identify the destination to which it should be delivered. Most countries include a code such as a postcode in the address. This identifies the area that the package is to be delivered to. If a computerised sorting system is available then this will use the code to automatically route a package to its destination. The last stage of delivery is carried out by a postman who takes the package to the house that it is addressed to.
The cost of sending a package is paid for by purchasing stamps which are stuck onto the packet. It is more expensive to send heavier packages. It also costs more to get a package delivered more quickly.
Advantages
Disadvantages
|
|
A telephone network enables instant voice communication between two people. All countries have a telephone network but the proportion of people who have access to a telephone varies from country to country. In the UK over 95% of people have a telephone at home.
People who use a telephone system are known as subscribers. Each telephone connected to a network is identified by a unique number. To start a conversation with another person on the network you must dial the number of the person's telephone. A modern telephone system relies on a lot of highly sophisticated computer equipment to manage and connect calls.
Subscribers have to pay to use the telephone network. This payment consists of a fixed monthly charge for connection to the network and call charges. The cost of a call depends upon the length of the call, the time of day at which it is made and the distance between the people making and receiving the call.
The telephone network can also be used for transmitting data with a modem or for sending faxes. In the UK more than half of the capacity of the telephone network is now used for sending data.
Advantages
Disadvantages
|
|
Cellular telephones perform the same functions as an ordinary telephone. They can be used for instant voice communications with another person. By dialling the number of another cellular telephone you can instantly talk to the person who owns it. Over 30 million cellular telephones have been sold in the UK.
Ordinary telephones are connected to the telephone network by cables which run under and above the ground. Because of this a telephone can not be moved around. It can only be used near the point at which it connects to the network. In contrast a cellular telephone connects to the telephone network using radio waves. A cellular phone can be moved around and used at any point that is covered by the network. Most cellular phones can be used anywhere within the country they are purchased in and can often be used abroad as well.
Data can be transmitted using a modem and a cellular phone but this transmission is much slower than sending data with an ordinary phone. You can send text messages from one cellular phone to another using a system called Simple Messaging System (SMS). WAP phones let you access some Internet sites so that you can get useful text information such as traffic news via your phone. More similar services will be introduced now that faster GPRS phones are available.
There are many different ways that you can pay to use a cellular phone. Whichever way you choose, it is normally more expensive to use a cellular phone than an ordinary phone. There is a continuing debate over the safety of cellular telephones. Some surveys suggest that the radiowaves transmitted and received by these phones might affect brain activity.
Advantages
Disadvantages
|
|
A fax machine can be used to send copies of documents from one location to another. A fax machine consists of a scanner, printer and modem all built into one device. The document that is to be sent is inserted into a fax machine. It scans the pages and sends them via the telephone network to another fax machine. The receiving fax machine then prints a copy of the document.
A fax machine can be connected to the telephone network just like a telephone. A fax machine is identified by a number which you must dial to send a document to it. Few people have fax machines at home but most businesses have a fax machine. Charges for sending faxes are set in the same way as for making telephone calls.
Advantages
Disadvantages
|
|
Electronic Mail (email) is a system which allows users of a computer network to send messages to each other. Users can usually :
Each user has to have his or her own address that other users need to know to send messages to him or her. An example address is :
mark@mwchemicals.co.uk
An email system can transmit other types of information as well as simple text. Pictures, music, videos, in fact almost any sort of information that you can think of can also be sent. This is achieved by attaching files created in another package such as a word processor or drawing program to the end of an email message. These files are known as attachments.
An electronic mail system can be private and only operate within a particular company on the company's own WAN. However most email is now sent via the Internet so that any Internet user can send and receive email. In the year 2000 approximately one quarter of the UK population could send and receive emails. In poorer countries the proportion of people with access to email is much lower.
The cost of sending an email is very low. It is much cheaper to communicate by email than by post, fax or telephone. This is especially true if the person you are communicating with lives a long way away.
Advantages
Disadvantages
|
|
Video conferencing uses the telephone network to transmit video images from one location to another. These video images can be transmitted and received by computers with cameras attached or by specialised video conferencing hardware.
Video images can not be sent down a single telephone line. Usually many lines are required at the same time to send a high quality video picture, so using video conferencing is expensive.
Video conferences can take place between just two people. Frequently however many people, all at different locations, take part in a video conference at the same time. Large companies often use video conferencing systems. It can be much cheaper to hold a video conference than to bring a lot of people together to hold a normal conference. This is especially likely to be true if the people involved in the conference work a long way away from each other.
Video conferencing can be achieved much more cheaply by using web cameras on the Internet, but the picture quality will not be as good. An even cheaper solution to
hold a meeting between people at different locations is to use teleconferencing. In a teleconference only sound is transmitted. A teleconference is effectively a telephone call but
with many people taking part in it
instead of just two.
Advantages
Disadvantages
|
|
The teletext system transmits text and very simple graphical information to televisions. To access teletext you need a television set with a teletext decoder built into it. Each television channel can provide its own teletext service. The channel supplies the information that is included on the service.
Teletext information is sent as pages, each of which is identified by a three-figure number such as 100 or 360. The pages are transmitted in sequence, one after the other. To access a particular page you must enter the page's number into your television using a remote control. You will then have to wait until the page that you want is next transmitted. When this occurs the page will be displayed, but you may have to wait for as long as a minute to view a particular page.
Typical information that is available on a teletext system includes news, weather, television listings, financial news and sports reports. Deaf people can use teletext to put subtitles at the bottom of the television screen so that they can read the words that are being spoken.
Advantages
Disadvantages
|
|
Digital television was introduced in the UK in 1999. Eventually the digital television system will replace the current analogue system. Digital television has a number of advantages over analogue television. In particular :
To receive digital television you must either purchase a special decoder or a new television with a decoder built into it. Digital television can be received by satellite, radio waves or fibre-optic cable. Most digital television decoders also include a modem which can be used to connect the decoder to the telephone network so that data can be sent from the viewer back to the television channel. This enables the provision of interactive television where the user can influence what is transmitted.
The companies that run digital television channels have used the capabilities of digital television to provide a range of new services such as :
| Television Internet Television Internet is a limited
Internet service which can be viewed on a television.
A computer is not required to access television Internet. Some
World Wide Web pages
can be viewed and email can be sent and receieved. The data
is transmitted over a telephone line using the modem in the decoder.
| Pay-per-View
| A pay-per-view system can be used to make viewers pay for particular programmes that
they choose to watch. Pay-per-view is often used for popular events such as
boxing matches or film premieres. To watch a pay-per-view program you must use your
decoder to pay for the programme before it is transmitted. The decoder sends payment
details to the television channel using its modem.
| Pseudo | Video On Demand A video-on-demand service lets the viewer watch a television programme when he wants
to. The user chooses the programme from a menu and it is transmitted to his television
when he wants to see it. Such systems are very expensive to set up and use but a simpler
system called pseudo video-on-demand can be used with digital television.
The viewer can choose the programme he wants to view from a short list of programmes. Each programme
is transmitted every 15 minutes on a different channel. Once a viewer chooses a program he has
to wait no more than 15 minutes before it starts. This system works because a lot of channels
can be broadcast at the same time on a digital system.
| |
Digital televisions integrate a number of different functions from broadcasting and telecommunications into one product. It is likely that further integration of different communications technologies will take place in the future.
1. | Communicating is tranferring
information from one person or location to another.
|
| 2. | There are different
methods of communcation. The best method to use
on a particular occasion will depend upon the type of information being sent, how
quickly it must arrive, what equipment is available and how much you are prepared to
pay to send the information.
|
| 3. | Communication methods can be classified as
being broadcast or private :
|
|
| Private Communications Systems | ||||
| Method | Details | Advantage | Disadvantage | |
| Post | Letters and parcels are delivered by hand using a sorting system. |
| It can take a long time to receive a package sent by post. | |
| Telephone | Used for instant voice communications. Telephones are connected to network by cables. |
|
| |
| Cellular Telephone | Telephone system where phones are connected by radiowaves and can be used anywhere there is a transmitter. |
|
| |
| Fax | Used to send copies of documents from one location to another. |
|
| |
| Allows computer users to send messages and documents electronically. |
|
| ||
| Video Conferencing | Transmits live video pictures between users of the telephone system or over the Internet. |
|
| |
| Teleconferencing | Allows many people to take place in the same telephone call simultaneously to hold a meeting. |
|
| |
| Broadcast Communications Systems | ||||
| Method | Details | Advantage | Disadvantage | |
| Teletext | Sends text and simple graphical information as pages to a television. |
|
| |
| Digital TV | Sends pictures in widescreen format to televisions. |
| Have to purchase a new TV or set top box to use. | |
5. | Increasingly different communication
systems are being integrated together. For example a
digital television may incorporate
a modem so
that you can send email and access the
Internet.
| |
Section 20 : Computer Networks |
A computer network is a group of computers which are connected together to allow communication between them.

Computer networks can be classified in many different ways. Some important comparisons are :
1.
| Over how wide an area the network is spread. Networks in
small areas are known as local area networks (LANs)
and networks which cover larger areas are known as
wide area networks (WANs).
|
| 2.
| Whether network resources such as file storage space and
printers are controlled
centrally by a server or whether control is distributed
between the network stations on a peer-to-peer network.
|
| 3.
| How the communication links between the stations on the network are arranged. This
arrangement is known as the network topology.
| |
The speed at which data can be sent between different computers on a network is vital. The data transmission rate of a network or connection is commonly referred to as its bandwidth. Many home computers and computer networks have now been linked together to form the Internet.
Computer networks are usually put into one of two classes depending on how large an area the network covers. The two types of network are :
| Examples of LANs | Examples of WANs |
| A typical school computer network. | The Internet. |
| A network of computers used to share book information within a library. | A network of bank cash dispensers. |
| A ticket booking system used by a chain of high street travel agents. | |
| Properties of LANs | Properties of WANs |
| Covers a small area, usually just one site. | Covers a large area, often linking together several sites. |
| Computers connected by NIC and cables. | Computers connected by modems and telephone lines, ISDN, broadband or similar. |
| Fast transmission of data. | Slow transmission of data. |
Computers which are connected to a network are called stations. Stations on a LAN are normally connected to the network using a network interface card (NIC) and some cable. The cable might be made of copper or optical fibres (made of glass fibres).
Cables must run all the way around a building that has a LAN installed. Every station on the network must be connected to a cable.
Sometimes a radio transceiver can be used to connect a computer to a LAN instead of a cable. Using a radio means that the computer does not have to be plugged into the network, so it can be moved around more easily.
Connecting computers together at different locations on a WAN is more difficult than connecting computers on a LAN. This is because it is not possible to join two computers which may be thousands of miles away from each other by a simple cable.
Therefore connections to a WAN are usually made over a public network such as the Public Switched Telephone Network (PSTN). The cables that connect the computers are owned by a telephone company. Other companies pay the telephone company money to use its cables to build their WANs.
Telephone companies provide many different alternative methods that can be used to connect computers at different locations together. The three most common systems are :
| Method | Description | Speed
| Modem and Telephone Line
| A modem converts digital computer data into analogue form
so that it can be sent across a standard telephone line to another computer.
| Slow
| Terminal Adaptor and ISDN Channel
| A terminal adaptor sends data in digital form down a
special type of connection called an ISDN channel.
| Faster
| Broadband
| An ADSL or Cable Modem sends data in digital form down a telephone line or cable TV connection.
| Very Fast
| | ||||
Modems are often used to connect individual computers to a WAN. A modem can transmit data over a standard telephone line. You can use a modem wherever you can use a telephone.
Because the telephone network was set up before computers were in widespread use, telephone lines were not designed to carry the digital signals that computers use. They were designed to carry human voices in the form of analogue electrical waveforms.
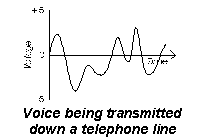
A special device known as a modem must be used to enable a computer to communicate over a telephone line. The modem converts the binary digital data that the computer wants to transmit into an analogue signal for transmission down the telephone line. Another modem must be used at the other end of the telephone line to convert the analogue signal back into a digital one that the receiving computer can understand.
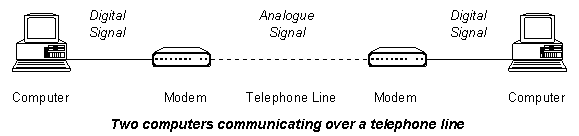
Modulation is the process of converting digital electrical signals generated by a computer into analogue electrical signals which can be transmitted over a telephone line. Demodulation is the process of converting received analogue signals back into digital signals which a computer can understand.
The speed at which data can be transmitted over a telephone line has increased steadily. Most modern modems can receive and transmit data at up to 56.6KBps (kilobits per second). Transmission speeds over a telephone line are very slow compared to other methods. Alternatives such as ISDN and broadband can send data much more quickly.
| Advantages of Modem over ISDN and Broadband |
|
A terminal adaptor can be used to connect computers on a WAN together using an Integrated Services Digital Network (ISDN) channel.
ISDN channels are a more modern form of connection than the public switched telephone network. Data can be transmitted digitally over an ISDN channel, so faster transmission speeds can be achieved than when data is sent using a modem and an analogue telephone line. ISDN channels are not available in all countries.

A single ISDN channel transmits data continuously at 64KBps (kilobits per second). This compares to a maximum speed of 56.6KBps for a modem. More than one ISDN channel can be used at a time to send data between two computers. If two channels were used then a speed of 2*64=128KBps could be achieved. When very fast speeds are required, large numbers of channels (e.g. 32) can be used together or (if available) broadband could be used instead.
| Advantages of ISDN over Modem |
|
The term broadband is commonly used to refer to high speed connections to a WAN such as the Internet. Broadband connections have become available in the UK in the last few years, but whether or not you can use broadband depends upon where you live. A typical broadband system can transmit and receive data at a speed of 560KBps. This means that data can be transmitted ten times more quickly using broadband than using a modem and telephone line. Because broadband connections are fast it is possible to use them for applications which needs to send a lot of data such as video conferencing.
There are two main methods of connecting a computer to a WAN using broadband. They are :
| Method | Description
| ADSL Modem and Telephone Line
| This method is only available at locations that have a telephone line which is connected to an ADSL (Asynchronous Digital Subscribe Line) enabled telephone
exchange. By connecting an ADSL modem to the computer and the telephone line it is possible to access a WAN through the telephone line and use the telephone to make voice calls at the same time.
| Cable Modem and Cable TV
| This method is only available at locations that have a connection to a cable TV network. By plugging a cable modem into the computer and the cable
TV control box it is possible to access a WAN through the cable TV connection.
| |
As well as installing the required hardware it is necessary to contact the company that owns the telephone/cable TV line to get them to enable broadband on a connection before it can be used. A monthly
fee will have to be paid to use the service, but this usually does not depend on how much the connection is used.
| Advantages of Broadband over Modem or ISDN |
|
One of the most important reasons for connecting computers to a network is to let the computers on the network share expensive resources such as file storage space and printers. Access to these resources must be managed in some way. This can be achieved using either a server based network or a peer-to-peer network.
Server Based Networks
The most common type of network used in a business or school environment is a server based network. On a server based network access to shared resources like storage devices and printers is obtained through special server computers. Three different types of computer are usually connected to a server based network :
The file server must ensure that people can only access files that they are permitted to. Most file servers do this by making each user log on with a user name and password before they can access any files. The user name that a user logs on with will determine which files the user can access.
The printer server controls access to shared network printers. Each station on the network can print out on the printer(s) connected to the printer server. If lots of people try to print at the same time then the printer server puts all the documents that are being printed in a queue. The documents are usually printed by the printer server in the order that they were sent by the users.

A large server based network may have more than one file or printer server connected to it.
Peer-to-Peer Networks
Peer-to-peer networks do not have special computers which are used as servers. Instead any computer on the network can load information from the hard disk of any other computer. A computer on the network can use any printer connected to any other computer.
Peer-to-peer networks are cheaper to set up and easier to manage than server based networks. They are however less secure. Because of this peer-to-peer networks are used mainly by small companies who trust their employees and do not have the necessary technical staff to maintain a server based network.

Network topology refers to the layout used to wire the computers together. There are four common topologies. Any topology can be used regardless of whether a network is local or wide area, server based or peer-to-peer.
| Bus (or Line) | Ring |
|
|
|
|
| Star | Hierarchical |
|
|
|
|
Data transmitted through a network or between two hardware devices is carried by a medium. The most common media are described here :
Wired
| Copper Cable
| Copper cable is used to electronically connect together computers on most LANs and in telephone lines. It allows reasonably fast
transmission and extra connections can easily be added to a copper cabled network. Data transmitted along
a copper cable can be corrupted by electrical interference.
| Optical Fibre
| Optical fibre can transmit data much more quickly than copper cables and across longer distances. This is because the data is carried as light rather than electrical signals. Optical fibres are interference
free and transmit data more securely than copper cables. The hardware required to use optical fibres is more complex and expensive than that needed to connect to a network using copper cable.
| Wireless
| Radio
| Radio transmission is sometimes used as a method to directly connect computers (usually laptops) to a LAN. Radio connections are slower than wired connections and more vulnerable
to interference. It is easy to add extra computers to a radio network as no new wiring is required. Computers connected by radio can be moved around whilst remaining connected to the network.
| Microwave
| Microwave transmission is used to connected together two different sites that belong to a WAN. For two sites to be connected by a microwave link there must be a line-of-sight
between them (you must be able to see one site from the other) and they must be within about 30 miles of each other. Operating a microwave link is cheaper than paying to use the telephone network if you have a lot of data
to send but transmissions can be affected by poor weather conditions.
| Satellite
| Satellites provide a versatile but expensive means of transmitting data. Satellites can transmit data very quickly and (subject to a suitably located satellite) to/from anywhere in the world. A suitable satellite
dish and transceiver are required. Data transmitted by satellite is less affected by the weather than data sent by microwave as the signal travels through space rather than through the atmosphere.
| Infra-Red
| Infra-red transmission sends data through the air as invisible light. Infra-red transmission speeds are very slow so this method is not usually used in networks. Instead it is used by hardware devices to
communicate with each other. For example a remote control communicates with a televsion using infra-red and a laptop could print to a printer by infra-red.
| | ||
The most common network topology is the bus (or line) topology. It is cheap and easy to set up a bus network because relatively little cable is required but bus networks are not as reliable as other topologies. If the main cable breaks anywhere along the network the computers connected to it will no longer be able to communicate with each other.
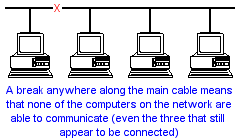
One way to reduce the effect of a cable break is to split the network up into sections using hubs or switches. This diagram shows a bus network that has been split up into three sections :

A sectioned network is more reliable than a standard bus topology. If a cable connecting a computer to a hub breaks then only that one computer will be affected. All of the other computers will continue to be able to use the network (note however that if the main backbone cable fails none of the computers will be able to use the network).
Hubs and switches are also used to connect together the computers at different levels in a hierarchical network.
Sometimes a number of LANs can be connected together to make a WAN. For example a company with LANs in each of its offices might choose to connect all these LANs together to make a WAN. If this is done then the workers at the different offices will be able to share information across the network. To connect two networks together one of two pieces of hardware is required :
| Bridge | If the two networks are of the same type they can be connected together using a bridge. The bridge simply copies data that is being transmitted from one network onto the other. |
| Gateway | If the networks are of different types then the job of passing data between them is more complicated. Data that is sent from one network to the other will need to be converted from the format that is used on the sending network into the format that is used on the receiving network. This job is done by a gateway. |
There is no limit to the number of networks you can connect together in this way. In the example below three networks are connected together. Note that computers on Subnet A can talk to computers on Subnet C by sending messages through Subnet B.
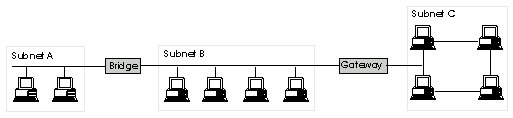
In complex network such as the Internet there are many different routes that data could be sent down to travel from one computer or subnet to another. Devices called routers are used to determine what route to send data along.
Computers connected to a network are more vulnerable to security threats than stand-alone computers. This is because :
For this reason extra security measures are usually applied to computers connected to a network. These may be implemented by a network operating system. Likely network security measures include :
| Network Security Measures | ||
| User Names and Passwords | The use of a user name and password system restricts who can access what data on a networked computer system. Users often have to log on to a file server before they can use a computer connected to a network. | |
| File Access Rights | File access rights specify what actions a user can take on a file or directory. The rights that a user has will depend upon the user name he is logged on with. | |
| Logs | When a user name and password system is in use a log can be kept of who has done what on a computer system. This may deter unwanted activity and will help track down anyone who has made unauthorised used of a computer. | |
| Encryption | Encryption is the coding of data so that it can not be read without being decoded first. Data is often encrypted as it is transmitted around a network so that if it is intercepted it can not be read. | |
| Firewall | A firewall is used to control and monitor data sent between two networks or between a home computer and a network. Firewalls can limit the types of data that are allowed to pass between networks and identify and block both viruses and attempts to hack into a network. | |
Ensuring security is even more essential when a computer is connected to a public network such as the Internet. Standard security measures such as backing up and using a virus checker should also be used on computers connected to a network.
Here are some of the advantages and disadvantages of networking a group of computers togther :
| Advantages |
|
1.
| A computer network is a group of computers
which are connected together to allow communication between them.
|
| 2.
| Computers connected to a network are known as stations.
|
| 3.
| The speed at which a network or connection can transmit data is commonly referred to as its bandwidth.
|
| 4.
| Computer networks are classified as being either Local Area Networks (LANs)
or Wide Area Networks (WANs). Important properties of LANs and WANs are :
|
| 5.
| Computers can be connected to a WAN using a modem and telephone line, a terminal adaptor and ISDN channel or broadband :
| 6.
| Access to shared resources such as printers and file storage space can be controlled using either a central server based system or a decentralised peer-to-peer system.
| 7.
| The network topology describes the physical layout of the computers on a network
and the interconnections between them. The four most common network topologies are
bus,
ring,
star and
hierarchical. |
| 8.
| Data sent around a network goes through a transmission medium. This could be wired or wireless. The most
common media are : |
| 9.
| Hubs and switches can be used to break a network up into sections so that if a cable fails the effects are less widespread than if a cable fails in a network that was not broken up. The main cable
running through the network is known as the backbone.
|
| 10.
| Two networks of the same type can be connected together using a
bridge. Networks
of different types must be connected using a
gateway. In complex networks suchs as the Internet where data can travel from one computer to another down many
different paths a router determines which way to send it.
|
| 11.
| Computers connected to a network are more vulnerable to security threats than stand-alone computers. This is beacuse data on one
computer can
be accessed from another, transmitted data can be intercepted, it is hard to control physical access and viruses can travel through networks.
Extra
security measures are implemented on networked computers, usually by a network operating system. Suitable meaures
include
user names and passwords, file access rights,
logs, encryption
and firewalls.
|
| 12.
| Advantages of networking a group of
computers together include :
|
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Section 21 : The Internet |
The Internet is the largest WAN in the world. It was developed by the United States Defence Advanced Research Projects Agency in the 1970s and was initially known as ARPANET. The Internet was designed to be used by companies and Universities doing military research so that they could share information. Since then the number of people who use the Internet, and the services that are provided on the Internet have grown tremendously. Over half of the population of the United Kingdom can now access the Internet.
Unlike other WANs, such as a lottery ticket machine network, the Internet is not owned or controlled by any one organisation. In fact the Internet is made up of lots of smaller computer networks (LANs) and individual computers connected together by a WAN to enable computer users to exchange information. Each small network that is part of the Internet is known as a subnet.
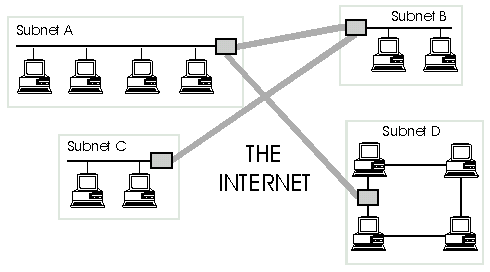
To connect to the Internet you will need some equipment such as a modem and telephone line or a broadband connection. Once connected you will be able to gain access to services such as electronic mail and the World Wide Web.
To connect to the Internet from home you will need several items :
The two most common methods of connecting to the Internet are using a modem and telephone line or a broadband connection. Other methods such as ISDN are also available. This table compares accesing the Internet by modem and broadband. Press on a Go button at the bottom of the table to find out more about how the two methods work.
| Method | Modem | Broadband
| Connection Via
| Telephone Line
| Telephone Line or Cable TV cable
| Hardware
| Modem
| ADSL Modem, Cable Modem or Router
| Speed
| 56.6KBps
| 560 to 2048KBps
| Connection Time
| Must dial up to use. Takes about 1 minute to connect.
| Always connected or almost instant connection.
| Availability
| Anywhere there is a telephone line.
| Available to around 85% of UK population.
| Pricing
| Either a fixed monthly fee of £12 upwards for virtually unlimited use or pay per minute (typically 2p/min).
| Fixed monthly fee for unlimited usage. Fees range from £15 to £75 depending on required speed.
| Suits
| People who can not get broadband, need to use the Internet from various locations (maybe with a laptop) or who use the Internet infrequently.
| People who use the Internet a lot, always from the same location.
| More Info
| |
When you connect to the Internet you can access many different services. Some of the most popular services are listed below.
| Service | Use | |
| Electronic Mail | Using electronic mail (email) you can send messages and computer files to any Internet user around the world. | |
| World Wide Web | The Word Wide Web (WWW) is a vast databank of information on many subjects which anyone can read and add information to. | |
| Usenet Newsgroups | Newsgroups provide a discussion forum on which people can ask questions which other users can respond to. | |
| Internet Relay Chat | Internet Relay Chat (IRC) let users "chat" to each other over the Internet. | |
| File Transfer Protocol | File Transfer Protocol (FTP) is used to retrieve files over the Internet. | |
| Broadcasting | Radio and low quality television programmes can be broadcast over fast broadband Internet connections. | |
The System
Electronic Mail (email) is a system which allows users of a computer network to send messages to each other. Users can usually :
Each user has to have his or her own address that other users need to know to send messages to him or her. An example address is :
mark@mwchemicals.co.uk
An email system can transmit other types of information as well as simple text. Pictures, music, videos, in fact almost any sort of information that you can think of can also be sent. This is achieved by attaching files created in another package such as a word processor or drawing program to the end of an email message. These files are known as attachments.
The Software
To be able to use email you need email software. A typical email package will let you :
Advantages and Problems
This table summarises the advantages and problems of using email :
Advantages
| Speed
| Electronic mail arrives much more quickly than ordinary post. An email can arrive anywhere in the world within a few seconds of it being sent.
| Cost
| The cost of sending an email is very low. It is much cheaper to communicate by email than
by post, fax or telephone.
This is especially true if the person you are communicating with lives a long way away.
| Accessibility
| Email is very accessible as you can read your email on any suitable computer anywhere in the world. You do not have to go home to receive email as you do with post or be able to
deal with the email as it arrives as you do with a telephone call.
| Problems
| Recipients
| Less people have access to email than to other communication methods. This is espcecially true in poorer countries.
| Packages
| It is not possible to send packages by email.
| Viruses
| Recently many viruses have been spread through the Internet as attachments to emails. To prevent this happening files received as attachments should be
virus checked before they are opened.
| SPAM
| Because email is very cheap many companies use it to send out adverts. Often these adverts are sent to people who have not asked for them and do not want them. They are known as
SPAM. If you receive too much SPAM email (as many people do) it can be difficult and time consuming to find the emails that you want to or should read.
| Information Overload
| Many people now receive so many emails that it takes too much time to read through each of them and see which are really relevant to them. Because emailing is cheap and easy people send information by
email that
they would not have bothered to send by other communication methods. Having so much information that you can not effectively deal with it all is known as information overload.
| | ||
The System
The World Wide Web (or simply Web) is the most popular service on the Internet. The development of the web was partly responsible for the rapid increase in the number of people who used the Internet in the late 1990s. The World Wide Web consists of millions of different sites, each of which contains information. Each site is identified by a unique address called a Uniform Resource Locator or URL.
The information at a site is stored in the form of pages which can contain text, pictures, sound and video. Because web pages can contain so many different types of information they can be designed to be attractive, informative and interesting. A page can be linked to other pages using hyperlinks. If you want to find out about a topic then you can be sure that there will be some information about the it on the web.
The Software
To look at information on the web you must use a special program called a web browser. Most web browsers will let you do these things :
When you first load your web browser it will display information from a page that you have chosen. This is known as your home page. Many users choose to have a special type of web site known as a web portal as their home page. A web portal is a page that acts as a starting point to obtain information from the world wide web. Web portals usually incorporate a search engine and hyperlinks to frequently used sites (such as news). Yahoo is an example of a web portal.
Accessing a Site
There are three methods that you can use to go to a particular page of information :
| Search Engine | If you want information on a particular topic and you don’t know where to
find it, you can use a
search engine
such as Alta-Vista to search the entire Internet for relevant pages. To use a
search engine you type in a word or several words which describe the topic that you are
interested in. The search engine will then list pages that it has found on the Internet
which are relevant to the words that you typed in. It will usually try to put the pages into order with the most relevant
near the top of the list.
Unfortunately due to the vast amount of information that is present on the Internet a search may result in tens of thousands of relevant pages being found. It is therefore very important to be as specific as possible when you use a search engine to keep the number of pages that are found to a minimum. |
| Hyperlinks | Each page can contain hyperlinks to other pages containing information about similar topics. If you are looking at a page on the screen then any links it contains will be highlighted (in underlined blue letters). By simply double-clicking on the link you will be taken to the page that it is a link to. Looking at web pages by clicking on links to move from one page to another is known as surfing. |
| Address | Each page has a unique address. If you know a page’s address (e.g. www.cedar.org) then you can type it in and go directly to the page. |
Uses of the World Wide Web
Information on the world wide web can be provided by individuals or by organisations such as governments and broadcasters. Here are just a few examples of how the world wide web can be used :
| Use | Details
| Research
| There is an incredible amount of information on the world wide web. This can be an
excellent source for researching virutally any topic. The information can be up-to-date and present a variety of views. You need to be carfeul however to verify the source and accuracy of information obtained from the web.
| Advertising
| Many companies promote themselves by advertising on popular web sites such as search engines. These adverts often takes the form of small images called banners. Companies can also set up their own
web sites to promote their products.
| Distibuting Software
| Traditionally software has been distributed on CD-ROM or floppy disk. Now it is possible to obtain
software directly from the Internet. This is known as downloading. Usually only software that takes up relatively little storage
space such as utilites and operating system updates are distributed on the web. Files that take up more space would take too long to download. Some
downloaded software
programs are free. Other software can be paid for online. The web is also used by software pirates to illegaly distribute copied software.
| Customer Support
| Companies can use the web to provide useful information to their customers. This can happen in various ways :
|
|
Creating a Web Site
A special computer language known as HTML is used to define the layout of pages. You can use a web design package to create your own web pages.
Advantages and Problems
This table summarises the advantages and problems of using the world wide web :
Advantages
| Availability of Information
| An incredible amount of information is available on the web. This is easy to access (you don't need to go anywhere) and easy to search (search engines do this automatically).
| Up-to-date Information
| Information on the web can be constantly updated. You can get the latest news, share prices, product support information etc.
| Multimedia
| Information on the web is provided as multimedia. This means that it can include text, pictures, sound and video.
| Problems
| Reliability of Information
| Anybody can put information on the world wide web. There is no guarantee that the creator of a web site is really an expert on the topic he has written about or is who he claims to be. You need to treat
information obtained from the web with care. Consider the source of the information and compare it with information from other sources.
| Too Much Information
| If you search for a particular topic using a search engine it will probably find tens of thousands or even millions of relevant pages. Manually looking through all these pages is very time consuming. Good
pages can be missed because they are not near the top of the list of pages that were found.
| Accessibility
| Information on the world wide web is only available to those who can afford to and know how to use the Internet.
| | ||
The System
USENET newsgroups are used by Internet users to discuss topics of interest. There are newsgroups for many different topics. Any user can read the articles that are in a newsgroup or add extra articles themselves. Newsgroups are a good place to ask questions of other Internet users.
For example if you wanted to find out something about the Java programming language you could ask a question in the comp.lang.java newsgroup. Your question would be seen by everyone else who reads this newsgroup. Anyone who knew the answer could send you a reply.

Any message you send to a newsgroup will not be seen immediately by the other newsgroup users. It will only be seen by a user the next time he reads the newsgroup. It may therefore be a number of days before you receive a reply.
Because USENET newsgroups are read by millions of people across the world you can be fairly certain that someone will be able to help you if they choose to.
The Software
To be able to read and create news messages you need a piece of software called a news reader. Sometimes the facilities of both a news reader and an email program are integrated into one package.
Advantages and Problems
The main advantage of USENET over other messaging systems such as email and chat rooms is that you can post just one messsage that will be read by many users. These users will probably be interested in or know about the topic the message relates to as they have chose to look at the newsgroup the message was posted to. USENET therefore provides an excellent way to find out about particular topics and to communicate with people you don't know who are interested in a topic.
There are two problems with the USENET system. The first is spamming. Many companies send advertisement messages to USENET newsgroups. These do not necessarily relate to the group topic and are often sent in large numbers. These messages are referred to as SPAM. Some newsgroups become unusable because they are overrun by SPAM. The second problem is that it can be difficult to determine the source and accuracy of a message posted to a newsgroup, so care needs to be taken when reading messages.
The System
Internet Relay Chat (IRC) is the most common mechanism for "talking" interactively over the Internet. The "talk" takes the form of typed messages rather than spoken words.
To take part in a discussion you must first enter a chat room. There are many different chat rooms available. Each room is dedicated to the discussion of a particular topic such as football, computer games etc.
Depending upon the popularity of the topic there could be either just a few or lots of people in a chat room at once. When you enter a chat room you can see the names (or nicknames) of all of the people in the room. You can also see the messages that these people are sending. If you want to contribute to the conversation you can send a message yourself. This will appear on the screens of all of the other users'.
Some chat systems will let you send private messages to particular users that only they can read.
Advantages and Problems
Unlike electronic mail, chatting using a system such as Internet Relay Chat is interactive. This means that when you type a message it appears on the other users' screens almost immediately. The other users are then able to respond straight away. To be able to chat like this all of the users involved in a conversation must be logged on to the Internet at the same time. It can be difficult to verify the identity of other users of a chat room. Some people disguise their identities and pretend to be someone they are not. It is never a good idea to give out personal information in a chat room as you can not really be sure who is reading it.
File Transfer Protocol (FTP) is used to download files that are stored on other computers on the Internet. Using FTP you can :
To access some files using FTP you will need a user name and password. However most FTP sites will let you logon anonymously by typing in "anonymous" as the user name and your email address as the password. If you set up your own web page then you will probably have to use FTP to put the pages onto your ISP's web server. Transferring information onto the internet like this is known as uploading.
Files can also be downloaded through the world wide web. Most people prefer to download from the web as it provides a simpler user interface.
The Internet was not designed with broadcasting in mind but several companies have developed software that enable radio and television pictures to be broadcast on it.
Good quality radio and low quality television pictures can be transmitted over the Internet. Broadcasting over the Internet is sometimes known as webcasting. To receive webcasts you need to have the appropriate software and a fast Internet connection such as broadband. It is not possible to receive Internet broadcasts using a slow connection like a modem and telephone line.
Advantages and Problems
This table summarises the advantages and problems of using the Internet for broadcasting compared to traditional methods :
Advantages
| Access Anywhere
| You can listen to the radio channel or watch the TV programme that you want wherever you are in the world. You do not need to be in a particular country or town.
| Range of Programmes
| Because Internet broadcasts can be made from anywhere in the world and received anywhere in the world there is a much bigger choice of programmes to listen to/see than on traditional broadcast systems.
| Easy Set Up
| The technology needed to broadcast on the Internet is much cheaper to obtain than traditional broadcasting equipment. Small companies or individuals can start broadcasting without spending a lot of money.
This means that new channels are more likely to set up and programmes can be made for minority interests.
| Problems
| Quality
| The quality of radio brodcast on the Internet is good, but Internet television is not very good. Pictures are often small or jittery, even with a fast broadband connection.
| Skills and Hardware
| The equipment required to receive Internet broadcasts is more expensive and more complex to set up than that needed to receive traditional broadcasts (i.e. a television or radio).
| | ||
There is very little regulation of the information that is available on the Internet. Because the network is spread across the entire world, it is impossible for national governments to control what information is available in their countries. This may be a good thing for freedom of speech but it does mean that unsuitable and potentially dangerous material can be obtained. This includes :
When you use the Internet yourself you have to be careful about what material you access and think carefully about whether information you read is likely to be accurate. In some institutions such as schools and workplaces steps are taken to reduce the likelihood of Internet users accessing inappropriate material. Filtering is the process of checking the content of requested web pages, email and other data to ensure it is appropriate before allowing it be viewed. There are many different ways a filtering system can work :
Advantages and Problems
The main advantage of using a filtering system is that it can prevent Internet users accessing inappropriate material. However no system is perfect and filters can sometimes let inappropriate material through, especially if a knowledgeable user deliberately attempts to access it. Filters can also sometimes cause problems by preventing access to web sites that a user has a genuine reason to want to visit. For example a history student trying to find out about racist attitudes in Nazi Germany might find that access to useful web pages is blocked.
Some companies want to provide facilities similar to those available on the Internet on a private network that is not connected to the Internet. For example a company might want to :
A private network within a company that provides facilities such as web sites and email is known as an Intranet. A company may choose to connect its Intranet to the Internet through a firewall to protect the computers on the Intranet.
There are advantages and disadvantages to each of the individual services such as the world wide web and email that are available on the Internet. Listed below are some general advantages and disadvantages.
Range of Information
There is an incredible amount of information available on the world wide web and through USENET. From home an Internet user can gain access to hundreds of thousands of times more information than could be stored in a large library. This information comes from a wide range of sources and can be of many types such as text, photos, sound and video. Information on the world wide web can be automatically located using a search engine.
In countries where the government usually restricts what the population can do and say the Internet has promoted freedom of information by making it harder for the government to control access to it.
Information Can Be Instantly Updated
Information that is accessed through the Internet can be instantly updated. You can obtain the latest information on many topics straight away using the world wide web.
Speed/Convenience of Access to Information
The Internet is very convenient to use as it can be accessed from home. Information on the world wide web can be located very quickly using a search engine. Email can send information from one user to another almost instantly.
A Smaller World
Through the Internet it is possible to access information from anywhere in the world. Email can be sent to family members or friends wherever they live. This helps to make people aware of other cultures and beliefs. It also encourages people to feel part of a global community instead of just a national one.
Quality of Information
There is very little regulation of the information that is available on the Internet. Because the network is spread across the entire world, it is impossible for national governments to control what information is available in their countries. This may be a good thing for freedom of speech but it does mean that you have to be careful when you assess information that you have obtained from the Internet. In particular you can never really be sure of :
Quality of Service
Most users connect to the Internet from home using a modem. The speed that modems can send and receive data at is quite slow. This means that only some types of information can be transmitted in a reasonable time period. Users are not prepare to wait too long for information to arrive.
Text can be sent quickly, but pictures can take a while to transfer. Audio files take a long time and downloading video sequences is very slow. This places restrictions on how web page designers can set out their pages. As well as considering how a page should look a web page designer must also consider how long a user will be prepared to wait to access the page.
Security
Because anyone with the appropriate equipment can access the Internet, there is some concern about the security of information on the Internet. In particular concerns exist about :
| Security of Payment Details | To purchase items from many e-commerce web sites you must enter your credit card number. If an unauthorised person were to obtain these details he could use this information to purchase goods and services with your credit card. Credit card numbers are encrypted before they are transmitted over the Internet, so they are relatively secure during transmission. Once an e-commerce company has your credit card number it will store it in a database. There have been a number of cases recently when hackers have managed to access these stored details and obtain credit card numbers which belong to other people. |
| Email Privacy | Electronic mail messages are not encrypted before they are sent. An employee of an Internet Service Provider or anyone who could obtain the appropriate level of access could read your emails. |
| Viruses | Viruses can be spread across the Internet. Some viruses such as Melissa have been developed specifically to infect computers via the Internet. Most Internet viruses are hidden in electronic mail messages. When you read an email message with a virus attached to it, the virus will infect your computer. |
Access
Because it is relatively expensive to connect to the Internet, access is restricted to those who can afford it. This means that many people will be unable to receive email or to access the world wide web. As use of the Internet becomes more widespread this could amount to discrimination against the poor and those who are not technically aware.
1.
| The Internet is the largest
WAN in the world. |
| 2.
| The Internet is made up of many individual computers and smaller networks known
as subnets.
|
| 3.
| To connect to the Internet you need :
|
| ||||||||||||||||||||||||||||||||||||||||||||||||||||
Section 22 : E-Commerce |
Electronic commerce, or e-commerce, is the buying and selling of goods and services over the Internet. The large number of Internet users and the ability to present information simply and effectively on the world wide web have made e-commerce a boom industry.
Traditional companies are competing with new companies which only trade on the Internet to sell products. Companies which only trade on the Internet are known as e-businesses. Some e-commerce companies sell goods direct to the public whilst others sell products to other companies.
Selling goods over the Internet has benefits for both sellers and buyers. Sellers can gain cheap access to a worldwide marketplace and buyers can purchase a wide range of goods and services from their homes.
To start trading on the Internet a company will need to :
If the company is a large one then it could take on new staff to run its e-commerce web site. Otherwise it may pay another specialist company to set up and operate the site. It is also likely that the company will need to invest in a lot of new computer hardware to connect its computer systems to the Internet and to operate the web site.
An e-commerce web site may be linked to a company's existing stock control and orders database. This would mean that users of the web site could be given an indication of whether a product they want to buy is in stock or not and how long it will be before a delivery can be made. Customers could also track the progress of their orders.
The initial costs of starting to trade on the Internet can be very high. Most e-businesses do not make a profit at the moment. However companies continue to set up new e-commerce web sites because they believe that in the long term these businesses will be very profitable.
When a customer buys an item from a business he makes a transaction. In a traditional business most stages of a transaction are carried out by a human. E-commerce transactions reduce the need for human intervention to a minimum. This means that an e-commerce purchase can be carried out much more cheaply than a traditional one. As a result goods can be sold more cheaply and companies can make greater profits.
The important steps in an e-commerce transaction are :
1.
| The customer browses the web site to decide what he wants to buy. |
2.
| The customer selects the items that he wants to purchase and identifies how many of each item
he wants. This list of items if often known as a "shopping basket". |
3.
| The customer enters his credit or
debit card details to pay for the goods. |
4.
| The company's computer connects to the computer at the customer's bank to check that
the card number is valid, that the card has not been lost or stolen, and that
the customer has enough money available to pay for the goods. |
5.
| The value of the goods is transferred from the cutomer's bank account to the company's
bank account. |
6.
| The customer enters delivery information such as his address so that the goods can
be despatched to him. |
7.
| All of the information about the purchase is placed in a
database of orders. |
8.
| The items purchased are collected together and packed. |
9.
| The postal service is used to deliver the goods to the customer. |
|
The first seven steps in this transaction process can be carried out without any need to involve an employee of the company.
Sometimes the payment is not taken from the customer's bank account until the goods are despatched. This is particularly likely to be the case if there is a long delay between the order being placed and the goods being despatched.
Often a confirmation email is sent to the customer before goods are depatched. This enables the company to double check that the purchase is a genuine one and provides the customer with a record of the transaction in case the delivered goods differ from those that were ordered.
Most goods and services can be bought and sold over the Internet.. Below is a list of some goods which can already be purchased by e-commerce. Many other type of goods are also available.
Online Banking
Online banks let customers access their account details over the Internet. Customers can view account balances and statements and transfer money between different accounts. This feature can be used to pay bills for items such as electricity.
Banks which only operate on the Internet sometimes offer higher interest rates to customers with savings than traditional banks do. This is because they do not have to pay the high costs of running branches on the high street. Customers can pay in money by post or by transferring it from another bank. Money can be withdrawn from an automatic teller machine (ATM).
Ticket Booking
Tickets for events such as pop concerts, theatre shows or sports matches can be purchased online. Tickets for travel by air or rail and complete package holidays can also be booked. Customers can check ticket availability on different dates and pricing before they make a booking. They can also easily compare different prices offered by different companies.
Often some tickets for an event remain unsold. A few days before the event is due to take place the organisers may choose to reduce the price of these tickets to encourage more sales. These tickets can be sold or auctioned at a lower price by specialist last-minute booking web sites.
Currently tickets are posted to customers after they are paid for. Systems are being developed which will let the customer print the tickets on his own printer as soon as they have been bought.
Auctions
An auction on the Internet can attract a lot more bidders than an auction held in an auction house would. Internet users can put items up for sale on auction web sites and other Internet users can bid for them. The web site owners charge a commission for each sale that takes place. Anyone, anywhere in the world can participate in a web auction.
The list of items that are available for auction can be displayed together with item descriptions and photographs. An item is usually sold on a particular date. Bidders can place bids in the days leading up to the sale. The computer system at the web site will automatically select the winning bid and will manage the transfer of the item from the seller to the buyer.
Car Importing
There is a widely held belief that cars cost a lot more to purchase in the United Kingdom than in other countries in Europe. There is a dispute over why this should be the case. Customers can save money by buying cars abroad and then importing them into the UK themselves. However many customers do not have the time or skills to organise this.
Therefore several companies have set up web sites which allow customers to buy cars from abroad. Once a customer has selected a car from a web site, the company that runs the site will purchase the car for the customer, import it into the country and deliver it to him.
Purchasing a car this way can save a customer a lot of money but there are disadvantages to. It usually takes a lot longer to buy a car from abroad than to buy it from a local car dealer. British car dealers also argue that the level of service obtained is inferior. Customers have to be very careful that they are dealing with a reputable company when buying a car on the Internet. A new car is an expensive purchase and the customer will have to pay a large deposit before he receives his car.
Books and CDs
There are a small number of web sites which offer books and CDs for sale over the Internet. These products are usually priced more cheaply than similar products in a shop, but a delivery charge will have to be paid.
On-line book and music stores can operate from out-of-town warehouses. They can stock a much wider range of items than a traditional store could and so cater to many different tastes and interests. An on-line catalogue can be provided which can include photographs of the items for sale and reviews.
There are a number of security issues which arise when a customer purchases an item over the Internet. Some common problems which customers encounter are :
| Lack of Information Customers often have access to less information about a company that they are dealing
with on the Internet than they would if they visited a high street shop. Just because a
web site claims to be run
by a well known company does not mean that it actually is. Fraudulent web sites
have been set up to gather credit card information so that money can be stolen from
the card owners. It can also be particularly
hard to rectify problems with an order if the company that you are dealing with is located
abroad. |
Transferring | Card Details To pay for a purchase, credit or debit card details must be transferred across a public
WAN. These details could be intercepted and used to make fraudulent purchases. Most
e-commerce web sites use a secure server. This means that they use a system such as
SSL to
encrypt card details when they are transmitted. It would be very
difficult for a hacker to steal card information during transmission. |
Linked | Systems E-commerce web sites are often linked to other
information systems belonging to a
company. There have been a number of cases where companies have accidentally allowed
Internet users to access these linked systems. As a result customers'
credit card details have been made public. This is the result of poor
security, and a breach of
the 1998 Data Protection Act for companies based in the UK.
|
|
Being able to trade goods over the Internet has brought advantages for customers and businesses. For the customer the use of e-commerce means that :
1.
| Customers can buy goods and services without having to leave their homes at whatever
time they want. This makes shopping easier for people who are very busy or who find it
difficult to travel to a shop. |
2.
| Customers can research their purchases on the
word wide web. Product descriptions,
photographs and reviews may be available. A customer can compare prices offered
by many different companies to obtain the best possible price. Some web sites will
carry out comparisons like this automatically. |
3.
| Because the customer can choose to purchase items from a wider range of companies,
these companies are forced to keep their prices low so that they remain competitive.
| 4.
| Customers can purchase a wider variety of goods more easily. They can access web sites
selling specialist products such as bee keeping equipment which would not normally be
readily available in a shop. |
|
E-commerce also brings benefits to businesses because :
1.
| A web site can be accessed from any computer that is
connected to the Internet,
anywhere in the world. This means that a small company based in one country can
sell goods to customers in other countries without having to set up offices abroad
or to pay for expensive advertising. The number of potential customers that a
company can reach will increase considerable if its starts to trade on the Internet. |
2.
| The cost of selling goods electronically can be lower than selling by traditional
methods. E-commerce companies do not need expensive town centre shops to trade from.
They can be based in out-of-town warehouses which are cheaper to build and rent.
Fewer employees are required as most of the process of the customer finding out
about a product and making a purchase is highly automated.
| 3.
| An e-commerce web site can operate for 24 hours a day every day of the year with
minimal human inviolvement.
| |
However e-commerce does not suit every customer, business of type of purchase. For example :
1.
| Some people do not like using computers or do not have the skills required to do so and so
will never purchase goods by e-commerce. Others enjoy taking a trip to the shops and treat
shopping as a leisure activity. They prefer to visit real shops than to buy goods on the
Internet.
| 2.
| Some people are concerned about the security of e-commerce transactions. Customers feel
they are more likely to be conned when they do not know exactly who they are dealing
with. There are also concerns about the security of
credit card details entered as part
of an e-commerce transaction.
| 3.
| Some goods such as clothing are highly personal. People like to see them for real and try
them on before they decide to buy them.
| 4.
| To purchase some items or services you have to visit a real building. For example you
have to go to a hairdressers to get your haircut. These services can not be sold directly on
the Internet.
| |
1.
| Electronic Commerce or e-commerce is the
buying and selling of goods over the Internet.
|
| 2.
| Electronic commerce has become popular due to the growth in the number of Internet
users and the development of the world wide web.
|
| 3.
| Companies which only sell goods on the Internet are known as
e-businesses.
|
| 4.
| A company that is involved in e-commerce must
set up a website and register its
address. Appropriate methods of payment collection, order delivery and advertising
must also be developed.
|
| 5.
| The costs of setting up an e-commerce web site can be high as computer
hardware must
be purchased and a web site must be developed.
|
| 6.
| The act of buying a product is known as a
transaction. E-commerce transactions can
be carried out very cheaply because there is very little human involvement. A transaction
involves the selection of goods, the transfer of payment and the despatch of the goods.
|
| 7.
| Examples of e-commerce businesses include :
|
| 8.
| Security is an important issue when goods are purchased on
the Internet.
|
|
Section 23 : Global ICT Services |
A service is something that you can buy which does not exist as an object. For example haircuts and operations are services. Paying an accountant or solicitor to give you advice or a secratary to type a document for you would also be services. Usually when you buy a service you are paying someone to do something for you. This contrasts with buying a good such as a book where you are paying someone to give you something.
Many services can now be delivered using information systems. These services are mostly concerned with manipulating information. They take some information from you, process it in some way and then return the outputs of this processing to you. Because information can be sent around the world very quickly using methods such as fax, telephone and email these services can be provided from anywhere in the world. It does not matter if the person purchasing the service is in a totally different country to the company or person supplying the service.
A service which processes information using an information system and can be provided from anywhere in the world is known as a Global ICT Service.
Global ICT services take some information from you, process it in some way and then return the outputs of this processing to you. Some example global ICT services are :
| Examples of Global ICT Services | ||
| Secretarial Services | A secretary anywhere in the world can receive rough notes or sound recordings of information by email or FAX and turn this into a professionally presented document which can be returned by email. | |
| Bulk Data Entry | Large volumes of data can be entered into computer databases in foreign countries and then sent to the UK. Workers in some countries will do this in return for lower wages than workers in the UK. | |
| Web Design | A plan describing the structure of a web site together with information to be contained on the web site can be collected in one country and emailed to a web designer in another country who can produce the web site. | |
Services like this which process information can be carried out anywhere in the world because the information can be transferred from the person purchasing the service to the person supplying the service very quickly using electronic methods such as email and FAX.
Global ICT services usually have these four properties :
1.
| The supplier of the service can be located anywhere in the world, regardless of the
location of the service purchaser.
| 2.
| The information that the service must process is sent to the service supplier
using an elctronic method such as email or FAX.
| 3.
| The service supplier processes the information is some way to produce new information.
| 4.
| The information produced when the service is carried out is returned to the service
purchaser using an electronic method.
| |
The next pages contain three detailed examples of how global services can be purchased and provided.
A secretary creates professionally presented documents using a word processor. The information that must be included in the documents is usually provided by someone else. It may be given to the secretary as rough notes or by dictation. Traditionally a secretary would work in the same building as the person or team of people that he or she produced documents for.
If a company makes use of the Internet it is now possible for a secretary to work in a completely different location to the people she works for. The information that must be included in a document could be typed as rough notes or recorded as a sound file on a computer. This could then be emailed to a secretary anywhere in the world. Alternatively, rough handwritten notes could be FAXed to the secretary. The secretary can then prepare a document using the information and email this back to the person who wanted the document.
Because the secretary can be be in a completely different location from the people that she works for a company can purchase secretarial services from secretaries anywhere in the world. This will probably mean that the services can be obtained more cheaply as a company will have more potential secretaries to choose from and people in some areas are prepared to work for lower wages than people in other areas. Additionally a secretary will be able to work for several different people in different locations and will be able to choose where he or she lives without worrying about his or her work.
Some companies which deal with the public receive tens of thousands of completed data collection forms every day. For example a large insurance company could receive fifty thousand applications to start new insurance policies on a typical day. The information written on these applications must be entered into a computerised database so that it can be processed and stored.
The information that must be entered is usually handwritten. It could be inputted automatically using OCR software but this is not very accurate. Therefore workers are employed to read the information on the forms and type it into a computer. These workers are known as data entry clerks.
If there is a lot of information to be entered many data entry clerks must be employed. This can be very expensive for a company, as employees in the UK expect to receive a relatively high rate of pay. However in some other countries people are prepared to work for much lower wages. Therefore a company could save a lot of money if the data could be entered abroad. By making use of the Internet this can be achieved. The process works like this :
Because all of the information is transferred electronically the data entry process is not slowed down significantly. The work can be completed at a much lower cost because the workers are prepared to accept lower wages.
Most companies and many individuals want to create web sites containing information about themseleves, the work they do, or the products that they sell. It is possible to create a simple website yourself using web design software but for larger sites it is usual to employ a professional web design company to build and maintain the site.
Web design services can be provided by companies as a global service. A customer who wants a web site building can plan the structure of the web site and collect information and photographs to be included on the site. This can then be emailed to a web design company anywhere in the world.
The designers will create the site using HTML code and will write any neccessary programs in a language such as Java. They will then upload the site onto the World Wide Web for the company that ordered the site. Any changes that are required to the web site can be agreed between the company and the designers by email.
Because the location of the web designers is unimportant a company wanting a web site can choose from many more web designers than if it could only choose from web designers in the local area. For web designers the main advantage is that they can sell their services to companies anywhere in the world.
1. | A service is something that you can buy which does not exist as an object.
|
| 2. | Haircuts, operations, legal advice and secretarial services are example of services.
|
| 3. | A service which processes
information using an
information system and can be provided from
anywhere in the world is known as a Global ICT Service.
|
| 4. | For global ICT services, the location of the service purchaser and the service supplier is irrelevant. They can be located anywhere in the world.
|
| 5. | A global ICT service takes some
information
from you, processes it in some way and then returns the
outputs of this processing to you.
|
| 6. | The information to be processed by a
global ICT service (inputs) are usually sent to the service supplier electronically (e.g. by
FAX,
email) by the service
purchaser. It is then processed by the service supplier. The results of processing (outputs) are
are returned electronically to the service purchaser.
|
| 7. | This table lists some example global ICT services :
|
Section 24 : Data Logging |
Computers are often used by companies and scientists to automatically measure and record changes in conditions such as :
When a computer is used to automatically collect and record data as it is produced we say that the computer is being used for data logging.
A data logging system consists of sensors connected via an interface to a computer and some data logging software.
A typical computer system which is used for data logging will need to include :
| A computer. | |
| Some sensors to measure the physical quantities (e.g. temperature) of interest. | |
| An interface to connect the sensors to the computer. | |
| Some software to store and display the information on the computer. |
The sensors will measure the physical quantities of interest and pass this data on to the computer via the interface. At regular intervals the computer software will record this data. The software can then be used to display the data as a graph or a table.
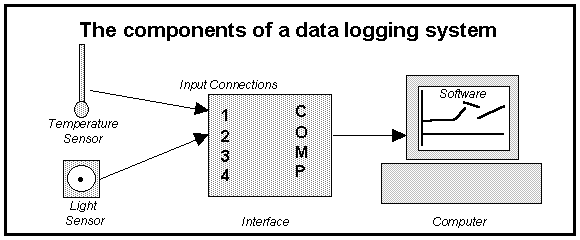
Data that is to be recorded by a data logging system is gathered using sensors. A sensor is a device which measures a physical quantity such as the temperature and then sends a voltage to the computer representing the quantity. Sensors can be either analogue or digital :
Digital : Sensors are either on or off. For example a switch of pressure pad.
Analogue : Sensors can measure a range of values. The size of the voltage the sensor produces is determined by the size of the quantity that the sensor has measured. For example if a cold temperature is measured a small voltage will be sent, whilst if a hot temperature is measured a larger voltage will be sent.
There are lots of different sensors available, each of which is designed to measure a specific quantity. Examples of sensors include :
| Sensor | Type | Quantity Measured | Application |
| Temperature sensor | Analogue | How hot/cold it is. | Monitoring the temperature of a science experiment. |
| Light sensor | Analogue | How light/dark it is. | Turning street lights on when it is dark. |
| Pressure Pad | Digital | If a pad is being pressed. | Detecting cars arriving at a car park barrier. |
| pH sensor | Analogue | The acidity of a liquid. | Monitoring river pollution. |
| Button | Digitial | If the button is being pressed. | Obtaining a ticket at a car park entry barrier. |
| Light Gate | Digital | Detects an object passing through the gate. | Measuring the speed or acceleration of objects. |
| Passive Infra Red (PIR) | Digital | Detects when an object moves into an area. | Activating a burglar alarm if someone enters a room. |
If you are designing a data logging system you will need to decide which sensors to use and where to put them. Many data logging systems will use lots of sensors at the same time.
If you need to use analogue sensors then as well as choosing the type of sensor(s) you want to use you must also make sure the sensor(s) take measurements over ranges that are suitable for the system you are creating. For example you may want to use a temperature sensor and have to make a choice between sensor A that measures temperature in the range -10ºC to 40ºC and sensor B that measures temperature in the range 0ºC to 120ºC. Sensor A would be best for measuring the temperature at which water melts and sensor B would be best for measuring the temperature at which water boils.
The sensors that are used in a data logging system are not plugged directly into the computer. This is because :
An interface is put between the sensors and the computer. You can typically connect up to eight sensors to an interface made for a home computer. The interface converts the voltages that the sensors produce into digital signals that the computer can process and protects the computer from dangerous voltages.
The conversion is carried out by a special device inside the interface which is known as an analogue-to-digital convertor or ADC.

When an analogue sensor is first connected to an interface it may need to be calibrated. Calibration matches sensor voltages with units that humans can understand. During calibration two readings should be taken and matched to known values. For example a reading could be taken from a temperature sensor when it was in a bucket of ice and matched to 0ºC. Then another reading could be taken when the sensor was in boiling water and matched to 100ºC. Once this has been done the computer will be able to work out the temperature in degrees for all other sensor voltage readings.
Calibration Example
During calibration a particular temperature sensor produces a voltage of 1V at 0ºC and 5V at 100ºC. The difference in voltages between the two temperatures is 4V. Therefore the computer can calculate that a change in the voltage produced by the sensor of 1V is equivalent to a change in temperatue of 25ºC.
Most data logging software will perform two main functions :
Recording Data
Because the data logging system has a limited amount of RAM it
can only store a limited number of readings from the sensors. When you design a system you
will need to decide :
To decide these things you must use your common sense and think about what you are monitoring.
The more frequently you take readings (or the more readings you take), the more computer RAM will be required to store them so it is important not to take readings too often.
Displaying and Analysing Data
The software will be able to display the data that has been recorded on the monitor or on a printer in a number of different formats such as :The graphs can be of different types. e.g.
Some organisations will perform much more sophisticated analysis of data collected by data logging than the software that will run on a home PC can. For example the Met. Office uses a very sophisticated computer model to analyse data collected using data logging equipment to produce a weather forecast.
Sometimes it is not possible to put the computer (or people) in the location that you need data logging sensors to be. Here are some examples of data logging applications where the computer and user are located some distance away from the sensors :
Information collected by the sensors must be sent back to the computer to be analysed. There are two different ways in which this can be done :
| Transmission | The data that is collected by the sensors can be transmitted electronically to the computer. Methods of communication such as telephone lines, radio links or satellites are used to transmit the data. |
| Storage and Collection | The data that is collected by the sensors can be stored in a small amount of RAM contained in a device called a data logger. The data logger is located near the sensors. When the data needs to be analysed a person must go and collect the data logger and take it to where the computer is. The data can then be transferred into the computers memory using a simple cable. |
The transmission method is usually best because the data is available straight away to be analysed by the computer. A person does not need to go and collect it. On the other hand the storage and collection method is usually much cheaper. Sometimes only the transmission method can be used. Nobody could go to the space probe to collect the data it had stored in its data logger!
Collecting data using sensors and sending it over a long distance to a computer to be recorded and analysed is called remote data logging.
Using computers to record data has a number of advantages over recording data manually :
The main disadvantage of using a data logging system is the initial cost of purchasing the equipment. Whilst a thermometer can be purchased for less than one pound, the price of the components of a data logging system to record the temperature will be considerable.
When designing a data logging system you will need to consider :
1. | What you want to measure.
| 2. | What type
of sensors you will use for your measuring.
| 3. | What
range you will need your sensors to take measurements over.
| 4. | Where
you will position the sensors.
| 5. | Whether you will be able
to put the computer and sensors in the same place or will have to put them in separate
places and use remote data logging instead.
| 6. | The
amount of time that should pass between each
measurement (the time-interval).
| 7. | What
graphs / tables you will use
the software to produce and what you will do with them.
| |
Often the measurements that a data logging system takes are used to activate devices such as motors, lights, heaters etc. to control a process. For example measurements taken of the temperature in a house can be used to turn on the heater in a central heating system when it becomes cold.
When input measurements are used to control outputs like this the computer system which controls the process is known as a control system. There is a separate article on control systems.
1.
| Data logging is the automatic collection and recording of data as it is produced.
|
| 2.
| A data logging system consists of some sensors,
an interface, a computer and
software to record data.
|
| 3.
| A sensor is a device which measures a physical quantity such as the temperature
and then sends a voltage to the computer representing the quantity measured.
|
| 4.
| Sensors can be either digital or analogue :
|
| 5.
| Example sensors are heat sensors, light sensors, pressure pads and buttons.
|
| 6.
| An interface is positioned between the sensors and the computer. It performs two
tasks :
|
| 7.
| When an analogue sensor is first connected to an interface it may need to be
calibrated. Calibration matches sensor voltages with units that humans can
understand.
During calibration two sensor voltages are matched to known units. Using this
information any voltage produced by the sensor can be converted into units that
a human can understand.
|
| 8.
| Data logging software will take readings from the sensors at fixed intervals
over a specified time period. Later the software will analyse the data which
may be output as a table or a graph.
|
| 9.
| If the sensors can not be located by the computer that will analyse the data
then a remote data logging system can be used. There are two different types
of remote data logging systems :
|
| 10.
| Advantages of data logging systems over manual data collection methods :
|
| 11.
| The main disadvantage of a data logging system is the initial purchase cost.
|
| 12.
| Often the readings taken by a data logging system are used to turn
devices
such as heaters and lamps on and off. Such systems are known as
control systems.
| |
Section 25 : Control |
A computer control system is a computerised system designed to control a process.
Control systems use sensors such as temperature sensors and pressure pads to monitor physical quantities. Using software the control system will carry out actions based on the quantities it has measured. These actions might include turning on devices such as a light or pump or sounding a buzzer.
Control systems can often be found built into other machines. These are known as embedded systems. They are also used by companies to manufacture products using Computer Assisted Manufacturing (CAM) and robots.
Here are some example control systems :
| Example Control Systems | ||
| Traffic Lights | The computer controls the sequences of lights displayed at a cross-roads to ensure that cars do not crash. Additionally the computer operates a pedestrian crossing to let pedestrians cross the road when a button is pressed. | |
| Simple Greenhouse | The computer controls the temperature in a greenhouse to maintain the conditions required for the plants in it to grow. If the temperature gets too cold then the computer turns on a heater to keep the plants warm. | |
| Robot Arm | The computer controls the movement of a robot arm which sprays parts of a car body. The arm must only spray when the body part is present and must then follow a programmed spraying path. The arm must stop if any foreign object, such as a human being, gets in its way. | |
A typical computer system which is used for control will need to include :
| A computer (or microprocessor). | |
| Some sensors to enable the computer to detect quantities such as temperature or pressure. | |
| Some devices for the computer to turn on and off. | |
| An interface to connect the sensors and devices to the computer. | |
| Some software to read data from the sensors and decide when to turn the devices on and off. |
The sensors will be used to measure the physical quantities of interest. This data will be transmitted via the interface to the computer. The software that is running on the computer will use the data to decide which devices to turn on or off. The devices will then be turned on or off through the interface.
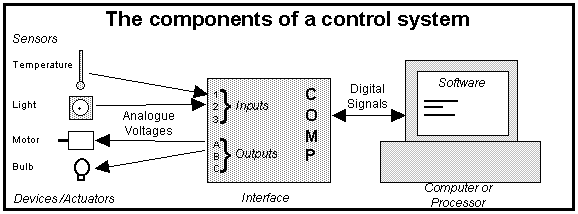
Sometimes the computer, software and interfaces can be combined together onto a single circuit board to be used inside a machine such as a washing machine (to control the wash cycle). This type of control system is called an embedded control system. A new car contains many embedded control systems.
Control systems use sensors to gather information about the world. A sensor is a device which measures a physical quantity such as the temperature and then sends a voltage to the computer representing the quantity. Sensors can be either analogue or digital :
Digital : Sensors are either on or off. For example a switch of pressure pad.
Analogue : Sensors can measure a range of values. The size of the voltage the sensor produces is determined by the size of the quantity that the sensor has measured. For example if a cold temperature is measured a small voltage will be sent, whilst if a hot temperature is measured a larger voltage will be sent.
There are lots of different sensors available, each of which is designed to measure a specific quantity. Examples of sensors include :
| Sensor | Type | Quantity Measured | Application |
| Temperature sensor | Analogue | How hot/cold it is. | Monitoring the temperature of a science experiment. |
| Light sensor | Analogue | How light/dark it is. | Turning street lights on when it is dark. |
| Pressure sensor | Digital | If a pad is being pressed. | Detecting cars arriving at a car park barrier. |
| pH sensor | Analogue | The acidity of a liquid. | Monitoring river pollution. |
| Button | Digitial | If the button is being pressed. | Obtaining a ticket at a car park entry barrier. |
| Light Gate | Digital | Detects an object passing through the gate. | Measuring the speed or acceleration of objects. |
| Passive Infra Red (PIR) | Digital | Detects when an object moves into an area. | Activating a burglar alarm if someone enters a room. |
If you are designing a control system you will need to decide which sensors to use and where to put them. Control systems will use lots of sensors at the same time.
The data gathered by the sensors is used to decide when to turn the devices connected to the control system on and off.
Devices are used by a control system to make changes to the real world environment that the system controls. Devices are also known as actuators. The devices are activated by electrical signals sent to them by a computer.
There are lots of different devices available. Examples of common devices include :
| Device | Action Produced | Application |
| Bulb | Lights up an area. | Lighting up a garden when a person walks into the area. |
| Motor | Rotation of a shaft. | Moving a buggy. |
| Buzzer | Makes a short beep noise. | Warning a pilot of a dangerous situation. |
| Pump | Moves gasses or liquids from one place to another. | Keeping a fish tank supplied with oxygen. |
| Heater | Produces heat. | Keeping a house warm in a central heating system. |
| LCD Display | Displays short sequences of numbers or letters. | Information readout on a till. |
The action of many devices will depend upon how high or low the analogue voltage that is sent to the device is. For example :
The computer will use software to decide when to turn the devices on or off and to determine how high a voltage to send to a device. This decision will be based on the information that the system has gathered using its sensors.
An interface is put between the sensors and the computer. You can typically connect up to eight sensors and four devices to an interface made for a home computer. The interface contains two important components :

The software used in a control system will regularly take readings from the sensors. Using this information the software must decide which devices to turn on or off.
When the control system is designed the user must input into the system the information it needs to take these decisions. This information will be in the form of an algorithm which describes when to take readings and under what conditions the different devices should be turned on and off.
The user would normally plan the algorithm using a flowchart, then input it into the computer using a programming language such as Logo.
This example shows the algorithm used to operate a very simple control system for a doorbell. When the button is pressed the bell sounds until the button is released.
The algorithm would be converted into a program and entered into the computer that will run the control system.
You can view the algorithm used to control three other systems later in the notes.
| Example Control Systems | |
| Traffic Lights | |
| Simple Greenhouse | |
| Advanced Greenhouse | |
Most useful control systems use feedback. Feedback occurs when the previous outputs from a control system change the inputs, usually to keep the system in a stable state.

Consider a refrigeration system which is used to keep food frozen at below -20°C. A temperature sensor is used to measure the temperature inside the freezer. The system contains a refrigeration unit to cool the freezer. If the temperature is below -20°C then the refrigeration unit is turned off to save energy. If the temperature rises above -20°C then the refrigeration unit is turned on to cool the food down.
The cooling system inside the freezer will repeatedly follow this sequence of actions :
In this system the inputs first affect the outputs (temperature sensor causes refrigeration unit to turn on). Then the outputs affect the inputs (refrigeration unit changes temperature reading). Because the previous outputs affect the inputs we can say that the system involves feedback. The feedback keeps the system in a stable (cold) state.
When data is collected from sensors it is converted into digital data by an interface. This digital data is transmitted to a computer as a binary number.
Simple devices such as bells or bulbs can be activated by an interface sending an electrical voltage to them. The computer tells the interface whether to activate a device or not by sending it a bit. A 0 tells the interface to turn the device off and a 1 tells the interface to turn the device on.
Many control systems only use digital sensors and simple devices. In these systems all of the data that is passed between the computer and the interface can be represented as a group of bits in a byte, with each bit indicating the status of a sensor or controlling the status of a device.
This diagram shows data that is being used by a control system for a burglar alarm :
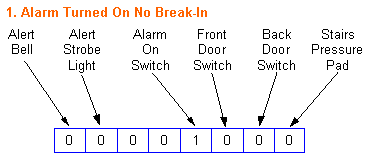
The current status of the alarm can be determined by interpreting the pattern of bits in the byte of data. Each bit represents the status of one sensor or device. Note that :
The alarm is currently switched on. This can be seen because the bit that relates to the Alarm On Switch is set to 1. The alarm has not detected a break-in. If a break-in is detected one of the sensors used to identify this (the door switches or pressure pad on the stairs) will set its bit to 1.
This diagram shows the change that occurs when a break-in happens :

The intruder has opened the front door. This has triggered the Front Door Switch so the bit associated with this sensor has been set to a 1. The computer responds by activating the Alert Bell and Alert Strobe Light devices. It does this by setting the corresponding bits to 1 :

This type of system, with the values of bits in a byte representing the status of sensors and devices is used by many control systems.
Using a computer to control a process has a number of important advantages over controlling the same process manually.
There are however some disadvantages of using a computerised system :
You will need to make several decisions when you design a control system. Exactly which items you need to specify will depend upon the particular system. Possibilities include :
1. | What
sensors and devices the system will
use.
| 2. | Where the sensors and
devices will be located and how they will be connected to the
computer.
| 3. | What
algorithm will be used to operate the system. This involves
describing how the computer will decide when the devices should be turned on and off
based on the inputs from the sensors. This algorithm could be described using a
flowchart.
| |
If you are asked to design a control system for a project you must also justify why you have designed the system the way you have.
This control system is used to operate a simple pedestrian road crossing involving just one set of traffic lights. When a pedestrian wants to cross the road she presses the button located near the crossing. After a short pause the traffic lights will turn to red so that the pedestrian can cross. Red and green men lights and a buzzer are used to indicate when it is safe to cross.
The important components of this system are :
Input and Output Devices
The control system has these input and output devices :
| Input Devices | Output Devices |
| Button | Red Light Amber Light Green Light Red Man Green Man Wait Sign Buzzer |
Flowchart
The operation of the control system can be described by this flowchart :

Note that there is no stop box because the crossing once started never stops operating unless something goes wrong.
This control system is used to keep a greenhouse warm in the Winter. It keeps the temperature of the greenhouse above 20°C. If the temperature drops below 20°C then a heater is turned on to warm the greenhouse up.
The important components of this system are :
Input and Output Devices
The control system has these input and output devices :
| Input Devices | Output Devices |
| Temperature Sensor | Heater |
Flowchart
The operation of the system is described by this flowchart :
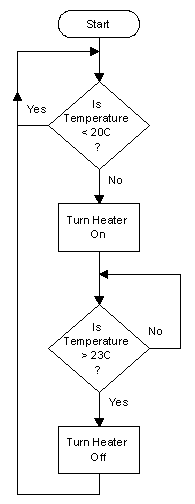
This control system is more advanced than the simple greenhouse control system described previously. As well as keeping the greenhouse warm in the winter it also prevents the greenhouse overheating in hot weather.
The system keeps the temperature of the greenhouse between 20°C and 26°C. If the temperature drops below 20°C then a heater is turned on to warm the greenhouse up. If the temperature rises above 26°C then a fan is turned on to cool the greenhouse down by blowing cold air from outside into the greenhouse.
The important components of this system are :
Input and Output Devices
The control system has these input and output devices :
| Input Devices | Output Devices |
| Temperature Sensor | Heater Fan |
Flowchart
The operation of the system is described by this flowchart :

Many computerised control systems are built into other devices that we use on a daily basis in the home and whilst travelling. A computer that is built into another machine is known as an embedded control system. Embedded systems have replaced mechanical or manual control of devices and enabled new sophisticated machines to be produced.
Here are some example of machines that commonly contain embedded systems :
| Machine | Use of Embedded System |
| Burglar Alarms | Burglar alarms usually incorporate an embedded system that uses sensors to detect the presence of an intruder. The system will be able to activate devices such as an alarm bell and telephone dialler if a break-in occurs. It may also be able to keep a log of events and communciate with a remote central monitoring station. |
| Environmental Control | Heating and air conditioning systems in homes, offices, cars and greenhouses use temperature sensors to measure the temperature of the area they control. They can turn on devices including heaters and air conditioning units and open vents to keep the temperature within a specified range. |
| VCR | Video cassette recorders (VCRs) are controlled by embedded systems. The embedded system in a VCR will allow it to be programmed to turn on and off at specified times to record programs when the owner is absent. |
| Refrigerator | The embedded system in a refrigerator will use a temperature sensor to measure the temperature inside the fridge and turn on a cooling unit if the temperature becomes too warm to keep food safely, |
| Car | A modern car will incorporate many embedded systems to control various aspects of of its use. Some tasks that a car will use an embedded system for are :
|
Using embedded systems instead of manual or mechanical control mechanisms is generally preferred because :
Computer Assisted Manufacturing (CAM) is the use of computers to manufacture products. Computers are able to make products like bolts, panels and cogs by directly controlling machinery such as :
Computers pass instructions to the machines that they are controlling using a standard system called Computer Numerical Control, or CNC for short. The designs of the products made by a CAM system are often developed using a Computer Aided Design (CAD) package. These designs can then be transferred electronically to the CAM system. A system in which the design of an item is produced in a CAD package and then the item is automatically made by CAM machinery is known as CAD/CAM.
Computers can also be used in a more sophisticated way to control an entire manufacturing process such as making a car. In addition to making the component parts a computerised system can assemble, move, paint and test them. Robots are often used to do this.
When most people think of a robot they imagine something that looks like a human, can perform a wide variety of tasks and thinks for itself. This is a long way from reality. The majority of robots are used in industry. They are designed to carry out one specific task over and over again. A robot will carry out its task very accurately but it is difficult to adapt a robot to carry out a task that is significantly different from the one it was designed for.
Robots are controlled by computer programs that respond to the inputs they receive from sensors. Robots use standard sensors such as buttons together with visual recognition systems that can be programmed to identify objects like screws or machine parts by processing images from a camera. Most robots use electrical motors or hydraulic systems to produce movement.
Here are some examples of uses that robots are put to :
| Task Type | Suitability | Example |
| Repetitive Tasks | Many jobs in the manufacturing industry are very repetitive. Humans are not very good at these. They got bored and tired and make mistakes. Humans do not get much satisfaction from carrying out repetitive tasks. | Over 50% of robots are used to manufacture cars. Robots can move car parts, screw or weld them together and paint complete cars. Each robot on a car production line will perform one specific job. It will be able to carry out its job highly accurately 24-hours a day. |
| Dangerous Situations | Because robots are not affected by certain factors such as radiation and because human life is valued so highly robots are often used in situations that would be dangerous to humans. | A robot buggy can be used to defuse a bomb. The buggy is equipped with cameras so that a controller can see where it is, a robot arm that the controller can use to lift a possible bomb and move it to a safer location and a high pressure water jet or gun that can be used to disarm a bomb. |
| Highly Accurate | Robots can move and positions items much more accurately than a human can. | Electronic components can be placed onto a circuit board and soldered together far more precisely using robots than by a human hand. They are also being used to assist surgeons in micro-surgical operations as unlike a surgeon's hand, a robot arm does not shake. |
| At Home | Robots have not yet become popular in peoples homes as they are expensive and currently unsuitable for many domestic tasks. | Robotic vacuum cleaners and lawnmowers are available but they are currently very expensive. |
The main advantages of using robots instead of humans are :
There are also some disadvantages to using robots :
You have already read about how a pedestrian road crossing can be operated by a computerised control system. Control systems can also be used in more sophisticated ways to manage the movement of traffic :
| Use | Description |
| Traffic Lights | At road junctions such as crossroads and roundabouts traffic lights are commonly used to indicate which direction traffic can travel in at any one time. This reduces the likelihood of accidents and ensures that cars moving in each direction have the opportunity to pass through the junction. The task of changing the colour shown at each set of lights to ensure that cars can only travel in one direction at a time is carried out by a computerised control system. The control system will let traffic move in each direction in turn. There may be sensors in the road or on the lights that detect how many cars are passing in each direction. The amount of time that each light is on red or green for could be adjusted so that if more cars are travelling in one direction than another they get more time to go through the junction. At quiet times of day the lights at a junction may be set to stay on green in one direction all of the time. Sensors will detect if any vehicles arrive at the lights from the other directions. If this happens the lights will change to let them pass. |
| Co-ordinating Traffic Flow | In most urban areas you will find many sets of traffic lights. As you drive through a town you may pass through several sets of lights on just one road. If you have to stop at too many of these
it can be frustrating and increase your journey time.
The operation of the traffic lights at different junctions can be co-ordinated to ensure that cars do not get stopped too many times. Here is an example of two sets of traffic lights at crossroads on one road :
Most traffic travels along this road in the direction indicated by the red arrow. If cars travel at around the speed limit then the operation of the two set of traffic lights will be co-ordinated so that when cars that passed through set A on green arrive at set B, the lights at this junction will also be on green to let them through. In a real system the operation of many sets of traffic lights can be co-ordinated. By co-ordinating the operation of traffic lights throughout a town it is possible to reduce journey times for drivers. The traffic lights are able to communicate with each other using wireless (radio) network connections. Information collected by sensors at the traffic lights may also be sent to a central monitoring station so that the people in charge of managing the traffic can spot busy routes and traffic jams. A central computer system may be able to adjust the timing of the various sets of lights so that if a traffic jam is building up the traffic in the busy area is given priority at the lights. |
| Congestion Charging | In some cities and on major motorways there is so much traffic that journey times can be very long. One way to reduce the number of vehicles that are on the road and so speed up the flow of traffic
is to charge drivers for the journeys that they make. This is known as congestion charging.
When a car enters an area covered by congestion charging a digital camera photographs it and sophisticated software reads the car registration from the number plate. This is looked up in a database so that the owner of the car can be identified. Other cameras will monitor the route that the car follows so that its entire journey is known. The car owner will then be charged for the journey. It may be possible to pay for the journey over the Internet by using online banking. The cost of a journey will depend upon the route followed and the time of day. By charging more at busy times it is possible to persuade some drivers to travel at other times or use public transport instead. |
| Car Parking | A computerised control system can be used to control access to car parks and charge the drivers that use them.
Magnetic sensors in the road detect when a car approaches an entry barrier. If there are spaces in the car park then a ticket will be printed for the driver to take and the barrier will be lifted. The ticket will have the time of arrival printed on it in human readable form and possibly also in machine readable form such as a barcode. When a driver leaves the car park a charge is made based on how long her car has been parked. This money may be collected by a person or by a machine that reads the barcode from the ticket and uses the data stored in the barcode to calculate how long the car has been parked for. Sensors on the exit roads will count how many cars leave the car park. By counting the number of cars arriving and leaving a computer can calculate how many spaces are free. If the car park is full then a warning sign near the entrance will indicate this and cars that arrive at the car park will not be allowed to enter. If there are several car parks in a town then signs can be placed on roads going into the town to indicate how many spaces are available in each car park. This will avoid the problem of people going to full car parks as they will be able to see a car park is full and choose an alternative less busy one to go to. At the end of each day the computerised system will be able to calculate the total amount of money that has been taken at a car park. |
| Satellite Navigation (SatNav) | Finding your way to a destination can be difficult, especially if you are going to a place for the first time. A computerised satellite navigation (or satnav) system can help to make this task easier.
Most satellite navigation systems are fitted into vehicles. They consist of a receiver, a computer, a CD-ROM or DVD-ROM drive, an
LCD monitor and a keyboard or remote control.
The receiver receives signals from a network of satellites called Global Positioning Satellites (GPS). From these the computer system can work out the location of the car. Maps are stored on a CD or DVD and based on the position of the car the computer can load the correct map and display it on the monitor with the car's position indicated. Before setting out on a journey the driver can enter the name or postcode of the place that he is travelling to. The computer can locate the destination on the map and work out the best route for the driver to take. As the journey progresses the monitor will be used to indicate when the driver should turn onto another road. Directions may also be announced through speakers using speech synthesis so that the driver does not have to take his eyes off the road. A satellite navigation system may also be linked to a traffic information system which can receive information about traffic jams and roadworks by radio. If a road involved in a journey is busy the computer system will be able to automatically change the recommended route to minimise the delay. |
1.
| A computer control system is a computerised system designed to control a process.
|
| 2.
| A control system consists of some
sensors,
devices, an
interface, a computer and
software to control the system.
|
| 3.
| A control system gathers data using sensors. Using an
algorithm the system will
decide when to turn devices on and off based upon the information provided by the
sensors.
|
| 4.
| A sensor measures a physical quantity such as the temperature
and then sends a voltage to the computer representing the quantity measured.
|
| 5.
| Example sensors are heat sensors, light sensors, pressure pads and buttons.
|
| 6.
| A device can be used to make changes to the real world environment that a control
system operates in. Devices are also known as actuators.
|
| 7.
| Example devices are buzzers, motors, pumps, lamps and liquid crystal displays.
|
| 8.
| An interface is positioned between the sensors and the computer. The interface
contains two important components :
|
| 9.
| The control software uses
an algorithm to decide when to turn the devices on
and off based upon the inputs from the sensors. The algorithm is usually planned
as a flowchart and then entered into the computer using a
programming language.
|
| 10.
| Feedback occurs when the preious outputs from a control system change the inputs, usually to keep the system in a stable state.
|
| 11.
| Information about the current status of the sensors in a control system is often presented to a computer by the interface as a
byte of data. Each bit in the byte represents the current state of one digital sensor, with a 0 indicating the
sensor is off and a 1 indicating the sensor is on. Devices can be
activated/deactivated by the computer setting bits associated with the devices to 0 (off) or 1 (on).
|
| 12.
| Advantages of computer control systems over manual systems :
|
| 13.
| The main disadvantages of computerised control systems are :
|
| 14.
| A computerised control system that is built into another machine is known as an embedded control system. Embedded control systems can be found in burglar alarms, environmental control systems,
VCRs, refrigerators and cars amongst many other machines.
|
| 15.
| Computer Assisted Manufacturing (CAM) is the use of computers to manufacture products. CAM systems control CNC devices such as lathes and milling machines to
make items. Often the design of the item to be made is produced in a CAD package and transferred electronically to a CAM system to be made. This is known as CAD/CAM.
|
| 16.
| Robots are computer-controlled devices that are capable of motion and can perform a variety of tasks. Robots can be used in situations that are dangerous to humans. They can perform
repetitive tasks highly accurately. Robots allow products to be made cheaply but have caused some people to lose their jobs.
|
| 17.
| The flow of traffic around a town can be monitored and controlled by a computerised system :
| |
Section 26 : Control Programs |
In the control topic you will have found out how computer programs can be written to operate control systems. Programs can also be written to control the movement of robots and vehicles.
Robots can be used for many different tasks such as :
Robots must be programmed with instructions to either tell them where to go or to enable them to decide where to go for themselves. Robots which may come into contact with humans must also be programmed to act in such a way that they do not cause injury or damage. For example if a robot in a warehouse finds an object in its path it must either stop or steer its way around the object.
A common type of robot that is often found in schools is known as a turtle.
A turtle is a small robot that can move around the floor. The turtle can move forwards and backwards and rotate left and right. Attached to the turtle is a pen. If the pen is lowered then the turtle will draw on a piece of paper placed underneath it as it moves. If the pen is raised then the turtle will not draw as it moves.
To carry out a task the turtle must be given a sequence of instructions to follow. The sequence of instructions is known as a program. A special programming language is used to give these instructions. Each individual instruction is called a command . Most turtles can be programmed using a language called Logo. The most basic turtle control language will support these six commands :
| Logo Control Commands | |
| Command | Purpose |
| PENDOWN | Lower the turtle's pen to start drawing. |
| PENUP | Raise the turtle's pen to stop drawing. |
| FORWARD 50 | Go forward 50 steps. |
| BACK 100 | Go back 100 steps. |
| LEFT 90 | Turn left 90 degrees. |
| RIGHT 45 | Turn right 45 degrees. |
The number after a forward or backward command is how many steps the turtle should move. The number after a left or right command tells the turtle how many degrees to turn through.
If a robot turtle is not available then the operation of the robot can be simulated by using a picture of a turtle on the screen.
Here are some example programs which use the turtle to draw shapes.
This program could be used to draw a number one :
PENDOWN FORWARD 60 LEFT 135 FORWARD 10 PENUP
The turtle moves forward 60 steps to draw the stick part of the one. It then turns left 135 degrees before moving forward 10 steps to draw the line at the top of the one.
The number one looks like this :
![]()
The large triangle shows the position of the turtle and the direction it is facing.
A square can be drawn by following this algorithm :
put the pen down
draw a side
turn right 90 degrees
draw a side
turn right 90 degrees
draw a side
turn right 90 degrees
draw a side
lift the pen up
This can be easily converted into the following program :
PENDOWN FORWARD 100 RIGHT 90 FORWARD 100 RIGHT 90 FORWARD 100 RIGHT 90 FORWARD 100 PENUP
An examination of the program shows that it actually repeats a pair of commands four times. These commands are FORWARD 100 RIGHT 90.
Most programming languages include a REPEAT command which will repeat a group of instructions a number of times. The square program can be written much more concisely using the repeat command :
PENDOWN REPEAT 4 [ FORWARD 100 RIGHT 90 ] PENUP
The commands in the square brackets after the REPEAT statement are repeated four times.
An equilateral triangle is a triangle in which each of the three sides has the same length. The angles inside each corner of the triangle are all sixty degrees. The angles outside each corner are all 120 degrees.
An equilateral triangle can be drawn by following these steps :

This algorithm can be written as a program like this :
PENDOWN FORWARD 100 LEFT 120 FORWARD 100 LEFT 120 FORWARD 100 PENUP
Using the repeat command the program can be written more concisely as :
PENDOWN REPEAT 3 [ FORWARD 100 LEFT 120 ] PENUP
1.
| Robots can be used to carry out many tasks such as welding, exploring and operating in dangerous environments.
|
| 2.
| Robots must be programmed to carry out a particular task.
|
| 3.
| A common type of robot which is found in schools is the turtle.
|
| 4.
| A turtle is usually programmed in a
high level language called Logo.
|
| 5.
| Most turtles will understand these commands :
|
| 6.
| The REPEAT command can be user to write programs more efficiently.
| |
Section 27 : Data Protection |
The use of computers for storing and processing information has brought many advantages for organisations who work with data :
Privacy
Whilst these may be "advantages" for the organisations concerned, they are not always "advantages" for the people about whom information is stored. Your privacy might be affected by the use of a computer to store information about you in a number of ways :
Data Misuse
It is much easier for people to misuse data stored using a computer system than using a manual system because :
To ensure that their privacy is protected people expect certain rights. The Data Protection Act of 1984 was introduced to give basic rights to people about whom information is stored on a computer. In 1998 this Act was replaced by the Data Protection Act 1998.
The first Data Protection Act was introduced in 1984. This was replaced in 1998 by a new Data Protection Act which changed the law to meet the requirements of the European Union.
The Data Protection Act gives rights to individuals about whom information is stored. Individuals may find out information about themselves, challenge it and claim compensation in certain circumstances. The Act places legal requirements on those who store and use personal data. They must let everyone know about their use of data and follow the data protection principles.The 1984 Act only covered data that was stored on a computer. The 1998 Act covers data that is stored either :
The Data Protection Act applies only to information which relates to living individuals.
The following definitions are used by the act :
| Definitions | |
| Personal Data | Information about a living individual who can be identified. |
| Data Subject | An individual about whom data is stored. |
| Data Controller | A person who holds personal data for processing. |
The Act created an Information Commissioner (previously known as the Data Protection Commissioner) who is responsible for enforcing the Data Protection Act and spreading information about it. The Commissioner maintains a Data Contoller Register (the Register) which is a list of all of the people who hold personal data and the purposes that they will use the data for.
With only a few exceptions any data controller who holds personal data on computer must register with the Information Commissioner. When a data controller registers an entry is made in the Data Controller Register detailing the data that will be stored. Each entry contains the following information :
A data controller who only stores records on paper does not have to notify the Commissioner. The controller will not therefore be entered in the register, but he will have to follow the rules set out by the Act.
The data protection principles are requirements that data controllers must meet to comply with the Data Protection Act. These eight principles state that any personal data stored by a data controller shall :
1.
| be processed fairly and lawfully
| 2.
| be processed only for limited purposes
| 3.
| be adequate, relevant and not excessive in relation to the purpose for which they are held
| 4.
| be accurate and up to date
| 5.
| be held no longer than is necessary
| 6.
| be processed in line with a data subject's rights
| 7.
| be kept securely
| 8.
| not be transferred to countries that don't have similar data protection laws to the UK.
| |
The Act gives legal rights to individuals (data subjects) concerning personal data held about them. These rights are intended to ensure that data subjects should not suffer from companies misusing data they hold about them. The seven main rights that an individual has are :
| Rights of the Individual | |
| Subject Access | An individual is entitled to be supplied by any data controller with a copy of any personal data held about him or her. The data controller may charge a small administration fee for this service. |
| Correction or Deletion | If data is inaccurate then a data subject may complain to the courts and have the data blocked, deleted or corrected. |
| Damage Protection | A data subject may prevent any processing which is likely to cause damage or distress. |
| Direct Marketing | A data subject may prevent processing of data for the purposes of direct marketing. |
| Decision Taking | A data subject may demand that a data controller does not take any decision which will significantly affect him solely on the basis of automatic processing. |
| Complaint to the Commissioner | A data subject who considers there has been a breach of one of the Principles of the Act by a data controller is entitled to complain to the Information Commissioner who must consider the complaint and can prosecute the data controller. |
| Compensation | A data subject can seek compensation through the courts if damage has been caused by the loss, unauthorised disclosure, unauthorised destruction or use of inaccurate data. |
The "Direct Marketing" right is designed to help individuals avoid receiving unwanted mailshots and telesales calls. The "Decision Taking" right is intended to protect individuals from unfair treatment as a result of computerised procedures such as "credit scoring" which is used to decide whether or not to let a person borrow money.
Sometimes data is exempt from the Act. This means that some of the parts of the Act do not apply to the data. It is useful to distinguish between two different types of exemptions :
Complete Exemptions
Some types of personal data can be stored without the Data Controller having to register with the Information Commissioner. These types of data are said to have complete exemption from the Act. Some examples of this are :
Partial Exemptions
Some types of personal data have partial exemption from the Act. Some but not all of the terms of the Act apply to this data. This table contains some examples of when a partial exemption might apply.
| Disclosure Exemptions | Stored information can sometimes be disclosed to people even though these people are not listed in the
disclosures section of the Data Controllers Register. Some example
disclosure exemptions are :
|
| Access Exemptions | The data subject has no right of access to information stored about him if one of the following access
exemptions applies :
|
| Storage Time Exemptions | A data controller can keep data for any length of time if it is being used for statistical, historical or research purposes. |
Whilst the Data Protection Act has given individuals extra rights to control what data contollers do with information about them it does have some limitations :
The Data Protection Act does not stop companies collecting and sharing information about you, so long as they have told the Information Commissioner that they intend to do this.
This table summarises the most important changes that have been made to data protection law with the introduction of the 1998 Act. Some of the changes do not come into force completely until 2001.
| Definitions | The Data Protection Registrar has beed renamed the Information Commissioner. |
| People who use data are now known as Data Controllers instead of Data Users. | |
| Manual Data | Data stored in a structured manual filing system is now covered by the Act. Most users with manual systems will not have to register with the Data Protection Commissioner, but will have to obey the rules set out in the Act. The 1984 Act only covered data stored electronically. |
| Principles | Some principles are changed slightly. An eigth principle which restricts which countries data can be sent to has been added. |
| Rights | A new right has been added which lets a person prevent processing for direct marketing purposes. An individual can also demand that any decisions which will signicifcantly affect him should not be made by automated methods only. |
| Exemptions | The list of exemptions has been considerably revised. Most of the old exemptions remain but many specific new ones have been added. |
A code of practice is a set of guidelines that a person employed in a particular job is expected to follow. A code of practice can :
A code of practice may be produced by :
| 1. Organisations can store and process data more easily and quickly using computerised information systems.
| 2. | Because it is easy to process and
share information using computers the privacy
of the individual might be affected.
|
| 3. | The Data
Protection Act 1998 places obligations
on organisations that store data and gives some basic
rights to individuals about whom data is stored. It
replaced the Data Protection Act 1984.
|
| 4. | The
Information Commissioner is
responsible for enforcing the Act.
|
| 5. | The Act uses these definitions :
|
| |
|
| 6. | An organisation that wants to
store personal data on computer must notify the Information Commissioner who will create
an entry in the Data Controller Register.
|
| 7. | Organisations
storing personal data in structured manual systems do not have to notify the Commissioner but
must obey the rules set out by the Act.
|
| 8. | It is a criminal offence punishable
by an unlimited fine to store personal data on computer without registering, unless an
exemption applies.
|
| 9. | Organisations storing personal data
must obey these eight principles. Personal data shall :
|
| ||||||||||||||||||||||||||||||||||||||||||||||||||||
Section 28 : Copyright |
The Copyright Designs and Patents Act (1988) states that it is illegal to copy software without the permission of the person or company that owns the copyright for the software. This means that it is illegal to make copies of floppy disks or CD-ROMs containing computer software or to install the same software onto more than one computer unless you have a special licence agreement.
The illegal copying of software is known as piracy and a person who does this is a pirate. Most pirates copy software for their own use but some pirates copy software to sell to other people. In some European countries it is estimated that each software package that is sold is copied seven times. In other parts of the world this figure is much higher. The growth of the Internet has increased the amount of software that is copied as many people choose to download illegally pirated software from the World Wide Web.
Illegal copying of software reduces the income of software companies. Having invested money in designing and producing software these companies need to earn income from software sales to recover these costs and make a profit. Without this income software companies will go out of business and the range of new software that is developed will be reduced.
The terms of the Copyright Designs and Patents Act make both the copying and the sale of copies of software packages illegal.
Despite the fact that copying software is illegal many people still do it. Therefore some software companies use copy protection methods to make it harder to copy software. They also use licence agreements to restrict the use that customers can make of the software that they purchase.
Specific offences which are outlawed by the Copyright Designs and Patents Act (1988) are :
There are some very serious sanctions which a court can impose on anyone breaking the law. These are :
If the crime is committed by a company rather than an individual then the directors or other responsible members of the company can be held legally responsible.
Despite the fact that the terms of the Copyright, Designs and Patents Act make it illegal to copy software, many people continue to do so.
Therefore the companies that develop and sell computer software take other measures to make it more difficult to copy software. These are known as copy protection measures. Copy protection can be achieved in many ways such as using unique codes and dongles.
| Method | Details |
| Unique Code | When you install some software packages you must enter a unique code into the package before it will work. Anyone who illegally copies the software will not be able to use the copy unless they know the appropriate code. Users who purchase the software legally usually have to register their names and the code for their copy of the package before they can obtain support from the company that made it. Because each legally sold copy of the software has a different code it is much easier to find out where an illegal copy of the software came from. |
| Dongle | A dongle is a small hardware device which plugs into a computer. To use some software packages you must plug a dongle, which is provided with the software, into the computer. Without the dongle the software will not work. If the software is copied or installed onto more than one computer it will not work as there is only one dongle. |
When you buy a software package you will enter into a licence agreement with the company that made it. A licence agreement is a legal contract agreed between the person who buys a software package and the company that developed and sells it. It states what the person who has purchased the software may do with it. Having a licence agreement does not make it harder to illegally copy software but does make it easier for a software company to successfully take legal action against a person who has pirated software.
There are several different types of licence agreement :
| Licence Type | Details |
| Single-User | Most home users who buy computer software get a single-user licence. A single-user licence allows you to install and use the program on one computer. If you want to install the package on another computer you must first remove it from the one it is already on. |
| Multi-User | If a software package is purchased by a company then the licence agreement may give the company permission to install the software onto more than one computer. This is known as a network, site or multi-user licence. This type of licence is very convenient for companies that have many computers connected to a network. The company will have to pay more for this type of licence than for a standard licence to install the software onto just one computer. But the cost will be lower than it would be to purchase individual copies of the program for each computer. |
| Freeware | Software that is described as "freeware" can be copied and used free of charge. It may not be altered or sold for profit. Many small utilities and games are freeware. |
| Shareware | Software that is described as "shareware" can be copied and used free of charge for a fixed time period. After this if the user decides that he wants to continue using the software a licence fee must be paid to the author. In return for the licence fee the user will be able to use the program forever and may recieve support and access to extra features within the package. |
1. | The
Copyright, Designs and Patents Act 1988 governs the illegal duplication of
computer software.
|
| 2. | Copying computer software without the
permission of the author is illegal. A person who does this is commiting
piracy and is known as a
pirate.
|
| 3. | In some European countries it is estimated that
each legally sold software package is copied illegally an average of seven times.
|
| 4. | Computer software companies
rely on the income from the sale of software packages. Illegal copying of software
reduces this income and may result in fewer new packages being developed.
|
| 5. | There are three different
offences created by the act :
|
| |
|
| 6. | Despite the fact that copying
software is illegal many people choose to break the law. Therefore software houses
use other methods as well to try and prevent piracy :
|
|
Section 29 : Hacking |
The Computer Misuse Act (1990) makes the misuse of a computer a criminal offence. The law was introduced in 1990. Throughout the previous decade the growth in the use of computers had made new crimes possible which existing laws did not deal with.
The Act is essentially an anti-hacking law. Hacking is attempting to gain unauthorised access to a computer system and a hacker is a person who does this. The Act applies to employees of a company who commit these offences from within the company as well as hackers who access computer systems remotely.
Many hackers attempt to gain unauthorised access to a computer system simply to demonstrate that they are clever enough to do this. Others may have more sinister intentions such as :
Making hacking illegal will not stop people from doing it. Therefore sensible companies do not rely on this Act to stop people misusing their computer systems. They incorporate appropriate security measures into their computer systems and keep regular backups. Most companies will also include a clause relating to the unauthorised use of computer systems in an employee's contract of employment. Any unauthorised use of a computer by an employee would probably lead to dismissal.
The terms of the Act make it illegal to gain or to attempt to gain unauthorised access to a computer system.
The Computer Misuse Act (1990) created three specific offences :
1. | The
Computer Misuse Act 1990 governs the unauthorised use of computer systems.
|
| 2. | Gaining unauthorised access to a computer
system is known as hacking and a person who does this
is a hacker.
|
| 3. | In many cases a person who
tries to gain unauthorised access to a computer belonging to an organisation actually
works for the organisation.
|
| 4. | After gaining unauthorised access to
a computer system a hacker may attempt to steal, change or destroy stored data.
|
| 5. | The Act created three specific
offences :
|
| |
|
| 6. | Sensible organisations do not rely on
the law to protect them from hackers. They take appropriate measures to reduce the
likelihood of a hacker accessing or damaging data :
|
| |
Section 30 : Health & Safety |
Many modern jobs involve using a computer system for long periods of time. For example :
| Computer Programmers | Computer programmers spend most of their time using a computer to write the code that is used in new software packages. |
| Call Center Workers | Employees in call centers answer telephone calls from members of the public who want information about services such as insurance or to buy products. When an employee answers a call he will record information about the call in a computerised database. He may also use another database system to locate the information that the caller wants. |
| Office Workers | Many office workers use computers to help them complete their work. Documents can be prepared using a word processor, information can be stored in a database and email can be used for communication. An office worker may spend most of his day using a computer. |
Using a computer for a long time can affect a person's health. Incorrect use of computer equipment can also pose a threat to safety. A lot of research has been carried out into the most serious risks to health posed by computer use. Measures which can reduce these risks have been identified. The government has introduced various regulations to try to reduce the likelihood of injury.
Working with a computer system and monitor is not believed to be particularly dangerous. However research has revealed that some types of problem are more common in workers who use computers for long periods than in other workers. The problems that computer users have the highest risk of encountering are identified below.
| Problem | Explanation |
| Eye Strain | Research suggests that using a computer monitor does not have any negative effects on eyesight in the long term. However there is evidence that computer monitors can cause temporary eye strain. Eye strain can be caused by poor positioning of a monitor, particularly if it is too close to the user, by poor lighting in an office or reflections from a screen. The most common symptom of eye strain is a headache. |
| Wrist Problems | Typing for prolonged periods without a break can result in a Repetitive Strain Injury (RSI) such as tendonitis. RSI occurs when a person is constantly using the same group of muscles. This occurs in the fingers, hands and wrists when a worker types at a keyboard for a long time. |
| Back and Neck Problems | Back and neck problems occur in computer operators because they remain seated in the same position for a substantial part of the working day. Poor location of the keyboard and monitor relative to the worker's chair can increase the risk of back and neck problems. |
| Stress | Stress is a feeling of mental or physical strain or tension. It is a person's natural reaction to being placed under too much pressure at work. Stress can be caused by prolonged periods of concentration which often occur when people use computers. Other factors such as the poor design of a user interface to a computer system or the repetitive nature of some computing tasks can also lead to stress. Workers who view themselves as "slaves" to the computer systems that they use are very likely to encounter stress. |
| Electrical Safety | Computer systems include many electrical devices and a lot of extrernal wiring to connect the different components of the system together. Poorly maintained hardware or wiring could result in an electric shock or fire. |
Many measures can be taken to reduce the risk of these problems occuring.
By taking appropriate measures the risk of many computer related health and safety problems can be reduced. Sensible measures for reducing these risks are listed below. Some of them are required by law.
| Problem | Measures to Reduce Risk |
| Eye Strain |
|
| Wrist Problems |
|
| Back and Neck Problems |
|
| Stress |
|
| Electrical Safety |
|
Many of the suggested measures, such as taking regular breaks away from the computer can help to reduce the risks of several problems at the same time.
The safe use of computers in the workplace is governed in the UK by :
These regulations apply to any employee who regularly uses a computer for a significant part of his job. It is the responsibility of both the employer and the employee to ensure that the regulations are obeyed. The most important rules set out by these regulations are that an employer must :
1.
| Inform employees about their rights under the regulations. |
2.
| Assess each computer workstation to identify any potential risks to health or safety and
inform employees about these risks. |
3.
| Ensure that each workstation meets minimum ergonomic (positioning) requirements. |
4.
| Provide appropriate training in the safe use of computer equipment. |
5.
| Plan work to provide regular breaks or changes in activity. |
6.
| Offer free sight tests to computer users at regular intervals and provide special
corrective spectacles if they are required for computer work. The employer does not have to
provide spectacles for everyday use. |
|
Parts of other laws also apply to computer equipment and its use in the workplace. For example, the 1989 Consumer Protection Act demands that electrical equipment must be adequately earthed and insulated and that proper instructions are provided for the use of the equipment.
1.
| Many jobs involve using a computer for a long time :
|
|
Section 31 : Security |
Data security is the application of safeguards to protect data from accidental or deliberate change, deletion or disclosure.
There are four main threats to the safety of data. These are :
Sensible organisations take appropriate measures to ensure that the data they store remains secure. Common security measures include password systems, logs and regular backups. The most appropriate measures to use in a particular situation will depend on :
If the stored data relates to identfiable individuals then a company must keep data secure to comply with the Data Protection Act.
There are four main threats to the security of data :
| Accidental Damage | Data stored on magnetic media such as disks or tapes can easily be damaged by poor storage, dirt, heat or magnetic fields generated by televisions or loudspeakers. Computer equipment can be damaged by acts of nature such as fire or floods. People using a computer system can easily delete the wrong file from a disk or the wrong record from a database by selecting the wrong option in a software package. |
| Data Theft | Important data such as a list of a company’s customers or information about how products are produced could be stolen and sold. Often such data is stolen by employees of the company who have legitimate access to the data. Disgruntled employees can also sometimes destroy or change important data. |
| Hacking | Sometimes if computers are connected to a network "hackers" deliberately gain unauthorised entry to computer systems. They can delete files or change the data stored in them. Hacking is an offence under the Computer Misuse Act 1990. |
| Computer Viruses | Computer viruses can deliberately delete or damage data stored on a computer. |
The threats to security become greater if computers are connected to a network. Organisations use many different measures to help enhance the security of the data that they store.
Many measures are available which can help improve the security of data. Which measures are appropriate will depend upon the situation.
| Computer Security Measures | ||
| Safe Storage of Data | Using high quality media and storing data in appropriate conditions will reduce the risk of data being accidentally damaged. | |
| Limiting Physical Access | It is possible to limit access to some computer systems physically using locks, swipe cards etc. This can reduce the risk of unauthorised personnel accessing or damaging data. | |
| User Names and Passwords | The use of a user name and password system can restrict who can access what data on a computer system. | |
| Biometric Measures | Biometric systems can identify people by recognising one of their unique physical characteristics. | |
| File Access Rights | File access rights specify what actions a user can take on a file or directory. Example access rights are read only, change and append. | |
| Logs | When a user name and password system is in use a log can be kept of who has done what on a computer system. This may deter unwanted activity and will help track down anyone who has made unauthorised used of a computer. | |
| Encryption | Encryption is converting data into an apparently meaningless form so that it can not be read by unauthorised users. | |
| Backups | A backup is an extra copy of data. If the original data is damaged then the backup can be used to recover the correct data. | |
| Virus Checks | Using a virus checker to identify viruses before they infect a computer can reduce the risks of a virus destroying data. | |
| Firewalls | A firewall is device or program that monitors and restricts the data that flows between a home computer or private network and a public network such as the Internet. | |
| Digital Signature | A digital signature is a binary code that uniquely identifies a person. Digital signatures are used to identify who sent an email and check the email has not been altered. | |
Important data should be stored safely. Some data may be kept for many years so it is important that :
Access to a computer system and data can be limited by keeping the system in a locked room. Locks and keys, security guards and video cameras can be used to ensure that unauthorised people can not gain access to the area in which the computer system is situated.
This would not however stop an employee who had the authority to access the computer room from causing deliberate or accidental damage or stealing important data.
A further limitation of this solution is that it is not always possible to limit access to a computer system physically. Some systems, such as the Automatic Teller Machines (ATMs) used by banks to dispense money have to be available for the public to use. Also, many computers are connected to networks and can be accessed from other computers on the network which are located elsewhere.
If a password system is in use then before you can access a computer system you must enter a valid user name and password . The process of entering this information and being granted (or refused) access to a computer is known as logging on.
Passwords can be guessed or "cracked" and so the success of these systems depends upon users choosing passwords wisely and keeping them secret. Following a simple set of guidelines like these will help make a passworded system more secure :
Attempting to guess a password to gain unauthorised entrance to a computer system is an offence under the Computer Misuse Act 1990.
Password systems are often used on computers connected to a network. The user name that you log on to a computer system with will determine which files you can access. A user should only be given access to files that he or she needs to use. Limiting the files that a user can access will limit the amount of damage that he or she might do either deliberately or accidentally.
As with limiting physical access to a computer system, the use of a password system will not prevent authorised users such as employees from damaging or stealing data. A more secure alternative to a username and password is a biometric system.
Biometric systems can be used as an alternative to passwords to identify the users of a computer system. Biometric systems identify people by recognising one of their unique physical characteristics.
The most common characteristic that is used is the fingerprint. To start with a person's fingerprint is scanned into a computerised database. When a person needs to be identified, his fingerprint is rescanned. The rescanned fingerprint is looked up in the database and matched to the stored fingerprint of the person it belongs to.

Biometric systems have a number of advantages over password systems :
Biometric systems can not be used in all situations as they require specialised hardware. For example you would have to use a username and password to log on to an Internet web site from home as you are unlikely to have a fingerprint scanner connected to your home computer.
An alternative biometric system recognises the pattern of blood vessels at the back of the iris. This is more sophisticated than a fingerprint system and more expensive to implement. Scientists are also working on a system that can identify people from the dimensions of their faces. This would enable people to be identified from further away than a fingerprint or iris scan. It is possible that people could be automatically identified using CCTV cameras.
File storage space on a computer network is usually shared by many different users. Some users will want to store confidential files which must not be accessible to other users. For example :
It is also sometimes the case that some users should be able to change a file whilst other users should be able to read the information in the file but not change it. For example :
File Access Rights are used to determine what actions a user can take with a file. File access rights can be applied to individual files or all of the files in a directory. Example file access rights are :
| Right | Explanation | Right | Explanation |
| Read Only | A user can read the data in a file but can not change it. | Change | A user can read the data in a file and change it but can not delete the file. |
| Append | A user can add data to the end of a file but can not change the data that is already in it. | Full Control | A user can do anything with a file. |
The access rights for a particular file or directory can be set differently for different network users. To enable this a username and password system must be in use so that the computer can determine who is trying to access a file.
One effective way of deterring authorised users from damaging or stealing data from a computer system is to get the system to keep logs of all of the actions that each user carries out. A log must be used together with a user name and password system.
All of the actions that a user carries out are stored together with the user's name in a log. If data is deleted, copied or changed the computer system manager can identify the person responsible by examining the logs. Here is part of a log :
| System Log 1/1/1997 | ||
| User | Time | Action |
| jbloggs | 12:00 1/1/1997 | log on |
| jsmith | 12:02 1/1/1997 | delete file "january accounts" |
| jsmith | 12:05 1/1/1997 | copy file "employee addresses" |
| jbloggs | 12:10 1/1/1997 | check email |
If users know that their actions are being monitored then they are less likely to deliberately damage or steal data. Logs can also be used to help trace any accidental damage to data.
A log can not stop a person from damaging or stealing data but it can help identify the culprits. Most hackers will try to turn off any log keeping software when they break into a computer.
Encryption is converting data into an apparently meaningless form so that it can not be read by unauthorised users. If some data has been encrypted then unless you know what the code used to encrypt the data was you will not be able to read it. Changing encrypted data back into its original form is known as decryption.
Files containing important or confidential data are often encrypted before they are saved onto a storage device. Encrypting a file will not prevent the deletion or corruption of the file. However if the file is stolen then it will be very difficult for anyone to read the information that it contains.
Data can also be encrypted before it is transmitted across a network. This usually happens when confidential data such as a credit card number is transmitted across the Internet.
Whatever measures are implemented to try and avoid data being deleted or changed, it is impossible to guarantee that this will not happen. Therefore it is vital that extra copies are made of important data. These extra copies are known as backups. For important data a regular backup procedure should be implemented.
Backups should be kept away from the computer room so that they will not be damaged by fires / floods etc. There is no point in keeping a backup if it is likely to get damaged when the original data gets damaged.
The type of backups that are kept usually depend on the type of processing being carried out :
There is a separate article which covers backing up in much more detail.
Viruses can get onto a computer from infected floppy disks, over a network or over the Internet. Virus checking software can be installed on a computer to examine all of the files that are accessed, checking them for viruses. If a virus is found the virus checker will attempt to remove it. The virus checker may not however be able to recover any data that has already been damaged by the virus.
Although the destructive actions of a virus are deliberately planned by the person who wrote the virus program, the introduction of a virus onto a computer system is usually accidental.
There is a separate article which covers viruses in much more detail.
Many businesses want to connect their private computer networks to a public network such as the Internet. They are however concerned that users of the public network may be able to access confidential data stored on their private network. Similarly home computer users are worried that Internet users may be able to access data stored on their computers. Many of the security problems associated with connecting computers to a public network can be overcome by using a firewall.
A firewall is device or program that monitors and restricts the data that flows between a home computer or private network and a public network such as the Internet.
Typically a firewall will let you :
A digital signature is a binary code that uniquely identifies a person. Digital signatures are used to improve the security of sending messages by email. Two particular problems with using email are :
You can get a digital signature from an issuing authority such as VeriSign or you can make your own up (but this is less secure). If you have a digital signature then when you send an email you can add it to the end of the email.
When the email is received the recipient will be able to verify that the message came from the person that supposedly sent it by checking the message's digital signature. Digital signatures also allow the recipient to check if the message has been altered at all since it was sent.
There is no such thing as a security system which can not be broken. Therefore any sensible computing department will have a disaster recovery plan. This will detail the procedures that should be followed to minimise any further damage once a disaster has occurred.
It will also include the procedure which will be used to attempt to repair or restore as much of the system as is possible.
1. | Data
security is the application of safeguards to protect data from accidental or
malicious modification, destruction or disclosure.
|
| 2. | There are four main threats to the safety of data. These are :
| 3. | Organisations which store important data take appropriate security measures to reduce the risk of data loss or theft. Possible measures include :
| 4. | Which security measures to use for
a particular computer system will depend upon :
|
| 5. | If the stored data relates to
identfiable individuals then a company must keep data
secure to comply with the Data Protection Act.
| | |||||||||||||||||||||||||||||||||||||||||||||||||||||
Section 32 : Backups |
No-one likes losing data that they have entered into a computer. Lost data represents a waste of time and effort. For companies the loss of data can be especially serious. Many companies store essential information such as customer accounts or stock databases on computer. Loss or corruption of this information could cost a company a lot of money.
If data is very important then appropriate security measures should be put in place to try and avoid any data loss or corruption. However problems can still occur :
Therefore extra copies of important data should be made on a regular basis. These copies are known as backups. If the original files become corrupt then the data can be restored from a backup copy. A company should have a backup strategy which sets out how backups will be made.
Often the method used to make backups will depend upon the type of processing that is being carried out :
| Backups by Type of Processing | |||
| Batch Processing | Backups are kept using the Ancestral or Grandfather-Father-Son system. | ||
| Transaction Processing | Periodically a copy of the master file called a file dump is made. Recent transactions are stored in a transaction log file. | ||
| Real-time Processing | A lot of backup hardware is employed to reduce the risk of failure. | ||
A backup is not the same thing as an archive. An archive is a file containing old data which is no longer used but which must be kept. Archive files are often kept under the same conditions as backups.
.
A backup strategy is a plan which details how backups will be made and how data will be restored in the event of a system failure. There are many important factors that should be considered in a backup strategy. These include :
How often should data be backup up ?
If a file is corrupted and you restore the file from a backup copy then some data may still be lost. This is the data that was added to the file since the backup was made. If backups are made once a week then a whole week's work could be lost. On the other hand if backups are made once a day then only a day's work would be lost. Backups should therefore be made as regularly as possible.
Unfortunately backups cost money to produce. Storage media must be purchased and staff time is taken up. Therefore a balance has to be struck between making backups very frequently and keeping backup costs down.
As a general rule files which change frequently should be backed up often whereas files which do not change very much can be backed up less frequently.
When should data be backed up ?
Backing up data can tie up a computer so that it can not be used whilst the backup is in progress. Therefore backups are usually made overnight or at weekends when a computer system is less likely to be in use.
What storage medium should the backups be stored on ?
There are a variety of different storage media that backups can be stored on. These include magnetic and optical disks and magnetic tapes. The best medium to use in a particular situation will probably depend upon the volume of data to be backed up and the speed at which the backup must be performed.
Where should backups be stored ?
There is no point in making a backup copy if the backup may be damaged. These guidelines should be followed to ensure that backups are stored safely :
Should backed up data be compressed ?
Data that is backed up can be compressed to reduce the amount of storage space that it will require. Compressed backed up data must be decompressed before it can be restored. Therefore backups are usually only compressed if they are unlikely to be accessed regularly.
Who will carry out the backup procedure ?
In a small company each employee may make his or her own backups. In a larger organisation however the task of producing backups will usually be performed by one selected individual. This individual can be properly trained in using the backup procedure and can keep accurate records of the backups that have been made.
What will happen if data is lost ?
If data is lost then it will have to be restored from the backup. A disaster recovery plan should be in place which describes how the data will be restored.
How many copies to keep ?
It is a good idea to make more than one backup copy. This gives you the extra assurance that if a file is corrupt and the backup is also corrupt then you have another backup which may still be operational.
In a batch processing system the File Generation, Ancestral or Grandfather-Father-Son backup method is used. Remember that in a batch processing system all transactions are entered into a transaction file. This file is then used to update the current master file to produce a new updated master file.
| When processing takes place the master file is known as the
father file. Processing the father file with the transaction file
produces the new master file which is known as the son file. The father file and transaction file are stored securely. If the son file becomes corrupt the father file can be processed with the transaction file again to reproduce the son file. In this way the father file and its associated transaction file act as a backup of the son file. An older copy of the master file called the grandfather file is also kept. If the son file and the father file are both corrupted then :
Every time processing occurs the tapes are moved back one generation. So the father file becomes the grandfather file and the son file becomes the father file. The old grandfather file is erased to be reused. |
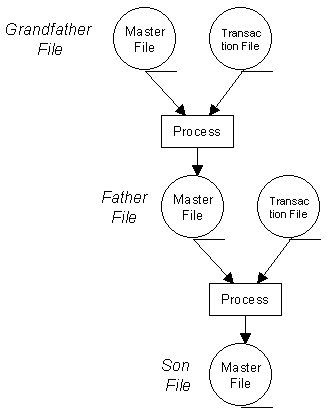 |
Backups for a transaction processing system are produced in a different way to those for a batch processing system. At the end of each time period a backup copy of the master file is made. The time period between each backup could be a day or a week. Making a complete copy of the master file like this is known as file dumping. The copy of the master file is known as a file dump.
Every time an alteration is made to the master file, since the last backup was made, details of the alteration are stored in a transaction log file.
If the system breaks down then two things happen :
By following this process no data should be lost. If there was no transaction log file then all of the transactions since the last file dump would be lost.
The consequences of failure in many real-time systems (e.g. flying a missile/passenger plane, running a nuclear power station) are immense. There is not a lot of point in keeping backup copies of data in a real-time system as there is unlikely to be time to restore backups if anything goes wrong. When a real-time system is developed the emphasis is placed on ensuring that the system will not go wrong rather than on designing a backup method to restore the system if it does go wrong.
Therefore most real-time systems incorporate a lot of spare hardware. Having much more hardware than you need to do a job means that if some hardware fails you can carry on doing the job. For example three identical computers may be used to decide which direction a missile should fly in. The computers each have a "vote" on which direction the missile should fly in. Because the computers are identical all three will normally agree on which direction to take. If one computer goes wrong then it will be outvoted by the two working computers so the missile will still function properly despite the failure. If two computers go wrong you are in trouble.
Sometimes backing up data to disk can be useful in real-time systems. Although this data could not be used to put the system back into its proper state, it could be used later to analyse why a system failed. The "black box" that records flight data in an aircraft is an example of this type of system.
1. | Organisations employee many
security measures to guard against loss or corruption of
data but this can never be completely prevented so backups are kept.
|
| 2. | A backup is
an extra copy of data which is stored in case the original copy is damaged. If the
original copy is damaged then the data can be restored from the backup.
|
| 3. | Organisations should have a backup strategy which details how data will be backed up. The strategy should include :
| 4. | How backups are produced often depends upon the type of processing that is in use :
| 5. |
An archive is a file containing old data which is no longer
used but which must be kept. Archive files are often kept under the same conditions as backups.
| | ||||||||||||||||||
Section 33 : Viruses |
A virus is a special kind of computer program which (usually) has these four features :
A new class of virus called worms have started to spread across the Internet. A worm has all of the properties of a virus but is able to spread without the user doing anything. If your computer is turned on and connected to the Internet it could get a worm without you doing anything.
There is nothing mysterious about a virus. A virus is simply a program that someone has written.
A computer "catches" a virus when a floppy disk or CD-ROM containing a virus is used on the computer. The virus may be hidden at the start of the disk or CD-ROM (in the "Boot Sector") or may be hidden inside another file.
When you access the disk or CD-ROM the virus will copy itself onto your hard disk. It will do this by looking for another program on your hard disk and attaching itself to this program. The virus may make lots of copies of itself, adding itself on to the end of other files on your hard disk to hide itself. The more copies of the virus that are made the harder it will be to get rid of.
Viruses can also be caught from files loaded across a network such as a school network or the Internet. In particular a number of recent viruses have been transmitted as files attached to emails. Viruses which attach themselves to emails can spread much more quickly that viruses which spread by other methods.
A virus only spreads when the user of a computer does something such as opening a file or reading an email. Worms spread across a network without the user doing anything. They simply look for computers connected to the network and copy themselves onto these.
There are several thousand viruses. They all do slightly different things. Here are some examples of the ways in which a virus might affect a computer :
Some viruses start operating as soon as they are copied onto your hard disk. Others are only triggered by certain events. For example a virus may do nothing until a particular date is reached.
Viruses can not damage the computer’s hardware; they can not stop your monitor or printer working or break your hard disk; though they could corrupt information stored on the hard disk.
The actions that a virus will carry out are deliberately programmed by the person who created the virus. However most viruses are copied onto a computer accidentally by someone who does not realise what they are doing.
There are several steps that you can take to reduce the risk of a virus getting on to your computer. These include :
Deliberately introducing a virus onto a computer system is an offence under the Computer Misuse Act 1990 which is punishable by a prison sentence of up to five years.
You could also install a special virus checking program on your computer. A virus checker will examine any files that you use. If a file has a virus then the program will detect it and may be able to remove it. Removing the virus could damage the file that has the virus but it will stop the virus spreading. Of course new viruses are produced all of the time so you must keep you virus checker program up to date with details of all the latest viruses.
If you are worried about a virus or worm getting onto your computer over the Internet you can use a firewall to stop other computers accessing data on your computer.
Regularly backing up important data will ensure that it can be recovered if it is attacked by a virus.
1. | A virus
is a program which :
|
| 2. | A worm is a special type of virus that can spread through a network like the
Internet without a user doing anything.
|
| 3. | A computer
"catches" a virus when a program to which the virus has
attached itself is used. The virus will copy itself onto the computer's
hard disk.
|
| 4. | Likely sources of viruses include
floppy disks, CD-ROMs and the
Internet. Viruses which spread on the Internet by attaching
themselves to emails can spread very quickly.
|
| 5. | Viruses are usually introduced onto
a computer system accidentally by a user who does not realise what he is doing. Deliberately
introducing a virus onto a computer system is an offence under the
Computer Misuse Act 1990.
|
| 6. | There are many thousands of viruses
each of which do slightly different things. Possible actions
include wasting hard disk space, deleting files and displaying annoying messages.
|
| 7. | Viruses can not damage computer
hardware. They can however affect the
software that is needed to use the hardware.
|
| 8. | Several
measures can be taken to avoid, detect and remove viruses from
a computer system :
| |
Section 34 : Validate & Verify |
A common problem with computer systems is that it is very easy to put incorrect data into them. For example :
If you put incorrect data into a computer system then you will get incorrect results out of it. Processing incorrect inputs will produce incorrect outputs. This leads to the acronym :
GIGO : Garbage In Garbage Out
Sometimes incorrect data can actually cause a computer system to stop working temporarily. This is a particular problem in batch processing systems when data may be processed overnight. If incorrect data stops a batch processing system from working then a whole night's processing time may be lost.
People who develop computer systems go to a lot of trouble to make it difficult for incorrect data to be entered. The two main techniques used for this purpose are :
| Validation | A validation check is an automatic check made by a computer to ensure that any data entered into the computer is sensible. | |
| Verification | A verification check ensures that data is correctly transferred into a computer from the medium that it was originally stored on. |
A validation check is an automatic check made by computer software to ensure that any data entered into the computer is sensible. There are many different methods of validation. The most appropriate method(s) to use will depend upon what data is being entered. The most common methods are listed here.
| Validation Checks | ||
| Presence Check | Checks that data has been entered into a field and that it has not been left blank. e.g. check that a surname is always entered into each record in a database of addresses. | |
| Type Check | Checks that an entered value is of a particular type. e.g. check that age is numeric. | |
| Length Check | Checks than an entered value e.g. surname is no longer than a set number of characters. | |
| Range Check | Checks that an entered value falls within a particular range. For example the age of a person should be in the range 0 to 130 years. | |
| Format Check | Checks that an entered value has a particular format or pattern. e.g. a new-style car registration number should consist of a letter followed by 1 to 3 numbers followed by 3 letters. | |
| Table Lookup Check | Checks that an entered value is one of a pre-defined list of valid entries which should be allowed. | |
| Check Digit | A check digit is a digit attached to the end of a string of digits. It is calculated from the other digits and used to help ensure that the whole string is inputted correctly. | |
| Parity Check | Used in data communications to ensure that data is not corrupted when it is sent down a transmission medium such as a telephone line. | |
| Batch/Hash Totals | Batch or hash totals are used when data is entered into the computer in batches to ensure that the data is entered accurately and no data is missed out. | |
Validation checks can be performed by any piece of software. However you are most likely to encounter them when creating a new database. Sophisticated database packages will let you implement validation checks using validation rules. You can provide different validation rules for each different field in the database.
A presence check is the simplest method of validation. A presence check can be used on any field in a database and simply checks that some data has been entered into the field, i.e. that the field has not been left blank
Presence checks are used on important fields which must have data entered into them. For example every student in a school must be a member of a form. Therefore a presence check could be carried out on the form field in each student's record to ensure that each student is placed in a form. The check would not ensure that each student was in the correct form.
A type check is a validation check which most databases perform automatically on all entered data. When a database is created each field in the database is given a type. Whenever data is entered into a field the database will check that it is of the correct type, e.g. alphabetic or numeric. If it is not then an error message will be displayed and the data will have to be re-entered. Here are some example field names and appropriate types.
| Field Name | Type | Valid Data | Invalid Data |
| Date of Birth | Date | 11/03/96 | 30/02/76, fred |
| Sex | Alphabetic | Male, Female, Albert | 123, WA2 |
| Shoe Size | Numeric | 12, 2.3, 12323 | 6G, house |
| Postcode | Alphanumeric | W12 6BD |
Notice that a type check is not a very good validation check. Many of the entries in the Valid Data column in the table pass the type check but are clearly incorrect.
As with type checks, most databases will automatically perform length checks on any entered data. The length check is a validation check which ensures that the data entered is no longer than a specified maximum number of characters. This is particularly important if a fixed length field is being used to store the data. If this is the case then any extra characters typed that made the data longer than the space available to store it would be lost. Here are some example field names and appropriate maximum lengths :
| Field Name | Maximum Length | Valid Data | Invalid Data |
| Title | 6 | mr, Mrs, George | The Duke Of, Sixteen |
| Surname | 15 | Smith, Jones | Smethurst-Whately |
| County | 15 | England, Car | The Former Yugoslav Republic of Macedonia |
Length checks are usually only performed on alphabetic or alphanumeric data.
Range checks are validation checks which are used on data made up of numbers or dates which must fall into a particular range. A lower and upper boundary for sensible values is specified. Any values which fall outside of this range will be rejected. Most sophisticated databases will let you set valid ranges for each field.
| Field Name | Lower Boundary | Upper Boundary |
| Age | 0 | 130 |
| Car Engine Size (L) | 0.5 | 8.0 |
| Month | 1 | 12 |
| Temperature in UK (C) | -20 | 40 |
Sometimes there is only one boundary required for a particular field. For example the minimum volume of a cube would be zero cubic centimetres, but there is no maximum volume. When there is only one boundary to check the type of check used is known as a limit check rather than a range check.
A format check is a validation check which ensures that entered data is in a particular format or pattern. The format that data must be in is specified using an input mask. The input mask is made up of special characters which indicate what characters may be typed where.
In a particular database the following special characters can be used to define an input mask :
Here are some input masks that could be used to validate three letter codes, car registration numbers and postcodes.
| Input Mask | Purpose | Valid Data | Invalid Data |
| LLL | Three Letter Code | ABC AND OLD | AB B2H ABCD |
| LL00LLL | Car Registration Number | AB01CDE DH53MAN | AB1CDE HELLO A823HFA |
| Ll90 0LL | Postcode | WA14 9JD M90 4SJ BL9 0HN | WAM4 9PM WA6 13H M12 9Q |
Sometimes when you enter a data item into an information system the item should only be one of a list of possible items. For example :
| Gender | When entering the gender of a person into a database the only two valid entries could be Male and Female. |
| Membership Number | When entering a membership number into a database the membership number must be a number that actually exists and belongs to a member. |
When this is the case a table lookup check can be used. A table lookup check takes the entered data item and compares it to a list of valid entries that are stored in a database table. If the entry is in the list of valid entries then it is allowed. Otherwise it is rejected.
Table lookup checks are also known as membership list checks or file lookup checks.
The check digit is a particularly important method of validation. It is used to ensure that code numbers that are originally produced by a computer are re-entered into another computer correctly. The check digit is a single digit added onto the end of a code number by the computer. The check digit is calculated from the other digits in the number. Check digits are included in bar code numbers.

Producing a Check Digit
This procedure is used to generate a check digit to add to the end of a number. It uses the Modulo-11 weighted check digit calculation. This calculation is used for ISBN numbers on books.
| 1) | Start with the original product number e.g. 185813415. | |||||||||||||||||||||||||||||||||
| 2) | Weight each digit by its position in the string and add up the results. Note that the
lowest weight used is 2 :
|
|||||||||||||||||||||||||||||||||
| 3) | Divide the total by 11 and then subtract the remainder from 11. The check digit is
the result of this operation :
|
|||||||||||||||||||||||||||||||||
| 4) | Add the check digit to the end of the original number to get the complete product number : 1858134143 |
Validating a Number Including a Check Digit
The procedure to check if a number with a check digit in it has been inputted correctly is similar to that used to generated the check digit :
| 1) | Input the number including the check digit. e.g. 1858134153. | ||||||||||||||||||||||||||||||||||||
| 2) | Weight each digit by its position in the string and add up the results :
|
||||||||||||||||||||||||||||||||||||
| If the last digit in the number is an X then it is treated as the number 10. | |||||||||||||||||||||||||||||||||||||
| 3) | Divide the total by 11.
| ||||||||||||||||||||||||||||||||||||
| 4) | If the reminder is 0 then the number has passed the validation check and so it is likely that it has been inputted correctly. |
It is important that each digit is weighted before the numbers are added up. If this was not done then a check digit would not detect transposition errors (where two digits are swapped around). This is a particularly common form of error when numbers are typed.
Parity checks are used during transmission of data to detect errors that have been caused by interference or noise. All data is transmitted as a sequence of 1s and 0s. A common type of error that occurs during data transmission is that a bit is swapped from a 0 to a 1 or a 1 to a 0 by electrical interference. Parity checks detect this type of error. A parity check works like this :
Transmission
| 1) | When data is transmitted each character is encoded as a 7-bit binary number. e.g. the letter ‘B’ has the code 1000011. |
| 2) | An eighth bit is added to make a byte. This bit is called a parity bit. |
| 3) | A system can use either even or odd parity -
For example in an even parity system a parity bit of 1 would be added to the code for B and it would be transmitted as 11000011. |
Reception
| 1) | When a character is received the number of 1s and 0s in the byte are counted :
|
| 2) | If this is not the case then an error must have occurred. A request will be sent to the transmitter to ask it to send the byte again. |
Parity checks are not very good at detecting burst errors where more than one bit in a byte is changed.
Note : Some examination boards treat a parity check as a verfication check rather than a validation check as the parity check ensures that data is correctly transferred from one location to another.
Some information systems process data that is entered into them in batches from documents. These systems typically use batch processing. Standard validation checks such as range and format checks are used to identify typing errors during data entry, but when data is entered in batches there are two extra types of error that may occur :
Batch and hash totals are two special validation checks that are used when data is entered in batches to identify if one of these types of error occurs.
Batch Total
Before the information on the documents is entered the user counts how many documents there are. This is the batch total.
As the data is entered the computer counts how many documents the data is typed from. After the data has been entered the total that was manually calculated is compared to the computer generated total. If the two differ then a document has been missed or some data has been entered twice.
Hash Total
Hash totals are more sophisticated than batch totals. They can be used to spot missed out or doubly entered documents and can also spot more complex errors such as one document being entered twice at the same time as another is missed out. A particular item on the batch of documents that must be entered is chosen. e.g. Hours Worked. The values of this item for each document that is to be input will be added up manually by the user. The total that is calculated is known as the hash total.
The data on the documents will then be entered. The computer will perform the same totalisation automatically on the chosen item. If the computer calculated total and the manually calculated total differ then a mistake has occurred during data entry.
If a batch or hash total identifies an error then the user will have to go back through all of the documents, checking which have been entered and which have not.
Example
These three documents recording the number of hours worked by the employees at a firm are to be entered in a batch (note that in a real system the number of documents would be larger than this) :

The chosen totals would be calculated manually by the user before the data was entered. Probably only one total would be used. Now suppose that the data was entered but by mistake the user missed out the middle document.
All of the different methods would spot the mistake as the user calculated and computer calculated totals differ. Suppose instead that the user missed out the middle document but entered the last document twice. The computer calculated totals would then be :
The batch total would not spot the mistake as the number of documents entered is correct (3). The hash totals would however spot it as they differ from the user calculated ones.
A verification check ensures that data is correctly transferred into a computer from the medium that it was originally stored on.
Verification checks are usually used to check that information written on a data collection form has been correctly typed into a computer by a data entry worker. Verification checks do not ensure that the entered data is correct. If the original form was completed incorrectly then the entered data will pass a verification check despite being incorrect.
The two most common methods of verification are :
| Verification Checks | ||
| On Screen | Entered data is displayed and the user is prompted to confirm that it matches the data on the input form. | |
| Dual Input | Data is entered twice and the two data sets compared. If there are any differences then the data is checked by the user and corrected. | |
One verification method is to use on screen prompts. After a user has entered some data it is redisplayed on the screen. The user is prompted to read the data and confirm that it has been entered correctly. If the user has entered any data incorrectly she should respond that the data is inaccurate and retype the incorrect parts.
This method of verification is not very reliable. Many users will not read the information that is redisplayed or check it carefully against the source document. However the method is relatively cheap to use.
The dual input method of verification is used when data is entered at the keyboard. The data to be entered is typed in twice by two different operators. The two copies of the data are then compared. Any differences are detected. The operators will be prompted to retype the sections that differ until both copies agree. When the two copies agree it is assumed by the computer that the data has been entered correctly.
This method of verification is very reliable. It is highly unlikely that any data can be incorrectly transferred into a computer system when the dual input system is used. Unfortunately it is very expensive to use. If data has to be entered twice then it will take twice as long to enter the data or twice as many people will have to be employed.
1. | It is very easy to accidentally enter
incorrect data into a computer system.
|
| 2. | Processing incorrect inputs will produce
incorrect outputs. This results in the acronym GIGO which stands
for Garbage In Garbage Out.
|
| 3. | Validation and
verification checks can be used to reduce the likelihood of incorrect data being
stored by a computer system.
|
| 4. | A validation
check is an automatic check made by a computer to ensure that any data entered into
the computer is sensible.
|
| 5. | Common validation checks are :
| 6. | If data is entered into an information system in batches from documents then two additional validation checks can be used. These
attempt to identify if any document is missed out or entered twice. They are :
|
The totals are calculated by the user before data is entered and by the computer after it is entered. If the user and computer calculated totals differ then an error is identified.
| 7. | A verification
check ensures that data is correctly transferred into a computer from the medium that
it was originally stored on.
|
| 8. | Common verification checks are :
| 9. | Neither validation checks nor verification checks
can test whether or not the data entered into a computer is correct.
| | ||||||||||||||||||||||||||||||||||||||
Section 35 : Data Collection |
Many information systems process data that is collected from members of the public who do not know anything about the computer system that is being used. When data must be collected in this way a data collection form (also known as a data capture form) is often used. Data collection forms are designed so that :
Data can often be entered into a computer system quicker and more accurately if a direct data entry (DDE) device is used to transfer the data from the data collection form directly into the computer. This avoids the possibility of a typist making an error when copying data from a form into an information system. However DDE devices are not suitable for inputting some types of data, especically handwritten information.
Here is an example data collection form that could be used to collect information about new members for a youth club :

This form has been designed very poorly. It is not clear what it is a membership form for. The purpose of the "No. of GCSEs you expect to get" question is not clear. The person who completes the form does not know whether to write the date as 12/03/87 or 12th of March 1987. And there is no way the person completing the form can write in their membership number - they haven't joined yet!
By following an appropriate set of guidelines it is easy to design data collection forms that are much more suitable than this example.
If you follow these guidelines then you should be able to design much better data capture forms :
Titles and clipart should be used to make it obvious what the purpose of the form is.
Language should be kept simple to avoid the possibility of confusion.
Clear instructions about what data is required and how it should be written down should be provided.
An appropriate amount of space should be left for the person completing the form to write the required details in.
Instructions should tell the person completing the form what to do with the form when it is completed.
Input boxes should be drawn on the form. The peson completing the form will be forced to write one letter in each box. This should make the form easier to read and ensure that the person completing the form does not write down more data than can be stored on the computer.
All questions should be relevant.
Tick boxes should be used where possible. These speed up input and ensure that the person completing the form can only choose a valid option.
A section should be added to the form so that the organisation that is collecting the form can keep track of what has been done with the information on it.
If appropriate, questions should be designed in such a way as to enable input into an information system to be carried out using a direct data entry device.
The bad youth club data collection form has been redesigned using the guidelines :

There are clear instructions about what to do with the form, and how to fill in the individual items. Input boxes have been drawn so that the person completing the form has to write one letter in each box, making the writing clearer to read. Where possible the user has been given boxes to tick to choose an options from a list of valid options. Information has also been added to the bottom of the form so that the youth club can keep track of what has been done with it, when it is returned.
Because the form is to be completed by a member of the public and because of the type of data that is being collected (e.g. address), it is not really possible to design the form in such a way that a direct data entry device could be used to automatically transfer the information from the form into the computer. Instead, a typist would have to enter the data using a keyboard. To reduce the likelihood of incorrect data being entered into the computer, the data would probably be validated as it is typed.
Data collection can be speeded up if a direct data entry device is used to transfer the data from the data collection form into the computer. Appropriate methods for doing this are :
If one of these methods is used then the data collection form must be designed specially for the method. The type of question that can be asked may also be restricted. For example if O.M.R. is used then questions can only be answered by making a mark in a box. Questions such as "What is your name ?" can not be asked easily.
Using a direct data entry device to input the data will eliminate the possibility of the data being incorrectly typed into the computer by the user.
Sometimes the data collection form has some information preprinted onto it by the computer. After the form has been completed the extra data added by a human is entered into the computer. This type of data collection form is known as a turnaround document.
Optical mark recognition and optical character recognition are often used together in a turnaround document. A turnaround document is a document which :
Here is a turnaround document that a gas company could use to record meter readings.

The document is printed by a computer. The name, address and customer number of the person that the meter reader should visit is printed on the form. The customer's last meter reading is also included.
The meter reader takes the document and visits the customer's house. He then marks the current meter reading onto the OMR grid on the form. In the example the meter reader has marked the reading as 4605. The form is then returned to the gas company.
At the gas company the form is fed into a special reader. Optical character recognition is used to read the customer's number from the form. Optical mark recognition is used to read the meter reading that has been added. All of the information can be read into the computer automatically. A bill can be produced and posted to the customer without any need for human intervention. Turnaround documents allow cheap, fast input of information into a computer system. There is no possibility of errors occurring because a typist has not transferred the data correctly from the form into the computer.
The customer number could have been printed on the form using a barcode. The disadvantage of this would be that the meter reader could not read the number from the barcode.
The turnaround document does not contain any instructions because the meter reader who fills it in will complete hundreds of similar forms every day. He will have been trained to use the forms so printing instructions on them would simply waste space.
Alternatives to Turnaround Documents
In some industries turnaround documents are being replaced by small handheld computers. For example many gas companies now issue their meter readers with handheld computers. At the start of the day the names and addresses of the customers that the meter reader must visit are downloaded into the computer. As the meter reader visits customers' homes, he types the meter readings into the computer. At the end of the day the readings can be transferred automatically onto the main computer to issue bills. Handheld computers used to enter data into a computer system are known as Portable Data Entry Terminals (PDET).
Questionnaires are used to collect information from the public. They are particularly useful when a lot of information has to be gathered from a large number of people. Companies and organisations use questionnaires to collect information for marketing purposes.
Whenever possible questionnaires are designed so that most of the information recorded on the questionnaire can be automatically entered into a computerised information system using a direct data entry device. The most frequently used type of question on a questionnaire is a multiple choice question like this one :

The person completing the questionnaire does so by ticking the box that most accurately describes his opinion. The responses to multiple choice questions like this can be automatically read, quickly and accurately, into a computer system using optical mark recognition.
Using multiple choice questions like this restricts the range of answers that a person can give. For example, a person who purchased a magazine twice a month would probably find it difficult to select which box to tick to answer the example question above.
Responses to multiple choice questions can be automatically entered into a computer and processed to produce statistical information about the responses. This can be clearly presented in the form of a chart or table.
Some questions can not be asked in multiple choice form. For example you can not record your name and address as an answer to a multiple choice question, and most questionnaires require this information. In these circumstances the data must be written in handwriting. If the handwriting was very clear this could be automatically input into a computer system using optical character recognition. However untidy handwriting would have to be typed in by an operator using a keyboard.
1. | A data
collection form (or data capture form) is used to gather information that will be entered
into an information system.
|
| 2. | Data collection forms should be designed so that :
| 3. | Following these guidelines will help to ensure that data collection forms are well designed : |
Section 36 : Simulation & Models |
A computer simulation is a computer program which attempts to duplicate or predict the behaviour of a real life system.
Commercial airline pilots learn how to fly by using a flight simulator rather than flying real aircraft. The flight simulator puts a pilot in copies of real-life flight situations and reacts to a pilot's actions in the same way as a real aircraft would. It is much safer and cheaper for airlines to teach pilots to fly this way. There are three main reasons for using a simulation rather than actually doing something. They are :
Cost : Using a simulation can be much cheaper than actually doing something. Crashing cars to see how the passengers (replaced by dummies) are affected by an impact would be very expensive. Many cars would be destroyed. Simulating this on a computer is far cheaper.
Safety : Some things are very dangerous. Finding out what would happen if a cooling system failed in a nuclear reactor by actually turning the system off would be highly dangerous. Using physical laws the effect could be predicted by a computer simulation.
Feasibility : There are some things that humans simply can not do. It would be interesting to be able to travel through a human body to see how the organs in the body worked. Unfortunately a human simply can't do this. But a human can use a simulation which shows what it would be like to travel around a body.
Simulations use rules and variables to model a real life situation.
Simulations are models of reality. A simulation should copy the behaviour of the real life system that it simulates. The designer of the simulation will incorporate as much of his knowledge about how the real system works as possible into the simulation software. Any simulation will have two important components :
Variables : Variables are things in a simulation that can change.
Rules : Rules determine how the variables in the model are changed and how they affect each other.
In a car driving simulation the variables might include :
A simulation will incorporate many hundreds of variables. Some variables such as the position of the accelerator pedal can be changed directly by the user. Other variables such as the car's speed are changed by the rules of the simulation. Two simple rules that you might want to incorporate into a car simulator are :
These two rules would have to be refined considerably before they could be used in a real simulation.
The rules and variables that make a simulation work are often implemented as mathematical calculations. The mathematical calculations that make a simulation work are known as a model.
Some simulators such as car or flight simulators need to use specialised input and output devices to make the user believe he is interacting with a real car or aircraft. A car simulator would use copies of a steering wheel, gear stick etc. as input devices. Large monitors positioned around the user would act as the main output device.
For other simulations such as a spreadsheet model of how ice cream sales change in hot weather, the methods of input and output are not important. A standard keyboard and monitor could be used.
Spreadsheet software can be used to create simulations of real world situations that use calculations to function :
The numbers typed into the spreadsheet are the variables in the simulation.
The formulae which perform the calculations are the rules of the simulation.
The calculations which are used to make a simulation in a spreadsheet are known as a model. Spreadsheets can be used to model simple or complicated financial situations :
A company could use a spreadsheet to try and predict the effect of changing the price of one of the products it sells.
Organisations like the treasury model mathematically the effect that changes in economic variables such as the rate of interest will have on the economy. A simple model of these effects could be produced using a spreadsheet.
Flight simulators are computerised models which simulate what it is like for a pilot to fly an aircraft. They are used to train pilots to fly real aircraft. Pilots train in simulators rather than in real aircraft because :
| Safety | It is safer to use a smiluator than to fly a real aircraft. Any errors will only result in simulated accidents, not real ones. This is particularly important when training new pilots as they are more likely to make mistakes. |
| Cost | It is cheaper to use a simulator than to fly a real aircraft. Fuel does not have to be paid for and if an accident occurs no real damage has to be repaired. |
| Situations | Different situations can be easily tried out in a simulator. For example a pilot can train to fly in different types of weather or to land at different airports by simply changing the setup of the simulator. |
A flight simulator is designed to train a pilot to fly a particular aircraft as although the principles of flying are the same for all aircraft, the layout of the instruments in the cockpit and the detailed method of controlling an aircraft will vary from one plane to another.
Input and Output Devices
Specialised input and output devices are used in a flight simulator. The flight simulator will be built within a module that is the same size as a real aircraft cockpit. The cockpit controls and displays will exactly duplicate those in the real aircraft. Very large VDUs are used to simulate the view that the pilot would see from the cockpit and hydraulic pistons are used to move the simulator module so that the pilot will feel motion similar to that in a real aircraft.
Rules and Variables
As with any other simulation, a flight simulator will be controlled by rules and variables. A real flight simulator will make use of tens of thousands of rules and variables. Some examples of these are :
| Example Variables | Example Rules |
|
|
After The Simulator
After a commercial airline pilot has been trained in a simulator he will be expected to make many flights without passengers before he is allowed to fly an aircraft with passengers onboard. This is because :
A virtual reality (VR) system places the user of a computerised simulation in an artifically created environment. By using sophisticated computer graphics, three dimensional VR headsets and a data glove the user can almost come to believe that the artificially created environment is real.
Hardware Used In A Virtual Reality System
Because virtual reality systems must produce very high quality graphics they usually require a very fast microprocessor, a lot of RAM and a large backing storage device to work effectively. Two other specialised devices are also used by most VR systems :
| VR Headset | The user of a VR system wears a headset which incorporates two small VDUs which cover each eye, earphones which produce sounds and a motion sensor. Because there is one VDU for each eye the user can view three dimensional images generated by the computer. The motion sensor detects movement of the user's head so that as the user moves the image that is displayed can change to take account of the direction that he is looking in. The combination of these devices can create a very realistic virtual environment for the user. |
| Data Glove | The data glove is worn on a hand of the user of a VR system. The glove contains sensors which detect the movement of the hand. By moving his hand the user can point at items in the virtual environment, pick them up and manipulate them. |
Applications of Virtual Reality
Most current virtual reality systems are quite basic. Much research and development is being carried out in this area. The eventual applications of this technology are uncertain, but some possible uses are listed here.
| The Virtual Office | Most graphical user interfaces liken the experience of using a computer to working in an office. Files can be placed on a desktop, work is stored in folders etc. A virtual reality system can extend this metaphor. The user could operate the computer by interacting with an artifically created office. Files could be accessed by lifting them out of the filing cabinet. The telephone could be answered by lifting a virtual 'phone handset. |
| Training | It is dangerous or difficult for some workers to train to carry out their jobs. For example soldiers can be injured in war exercises and astronauts can not easily practise the skills that they need to use in space on earth. By creating virtual reality copies of the real world environments that they have to work in these people can train to carry out their jobs by using computer simulators. |
| Recreation | Many people enjoy playing computer games. These are becoming increasingly sophisticated and the graphics that they use are becoming more and more realistic. By using virtual reality hardware these games can be improved further still. Game players can be fooled into believing that they are actually within the environment of the game that they are playing. |
Simulations can be used for many purposes. Here are some more examples :
| Example | Description | ||||
| Games | Many computer games attempt to mimic aspects of real life on a computer. For example :
| ||||
| Science Experiments | Some science experiments are too dangerous or expensive to conduct. The way in which different chemicals or physical effects interact with each other can be modelled by a computer so that the results of an experiment can be seen without having to carry it out. | ||||
| Weather Forecasting | The weather that we experience is determined by many factors such as atmospheric pressure, temperature, wind direction, time of day and the relief of the land. Computers are used to produce weather forecasts by simulating how these factors interact with each other and change over time. Powerful mainframe computers are required to carry out the complex calculations involved in forecasting. Weather forecasts are not perfect because the model used to produce a forecast does not incorporate all of the factors that determine what will happen. | ||||
| Economic Modelling | Organisations like the Treasury use mathematical models to simulate the effect that changes in economic variables such as the rate of interest, tax rates or exchange rates will have on the economy. |
No simulation will copy every feature of a real life system. The rules that the simulation's designer incorporates into the simulation will not perfectly copy every aspect of the real system. This is because :
Incorporating all the factors that affect a simulation would make it very difficult and expensive to produce the simulation. The number of variables and rules involved would be massive.
Some situations that could occur in real life are so unlikely to happen that the designer of a simulation would probably not think of including the situations in the simulation.
Mistakes can be made. Relationships in real life systems can be inaccurately observed or incorrectly programmed into a simulated model.
This limits the usefulness of the results produced by a simulation. A simulation is only as reliable as the rules that it is based on. Sometimes a simulation is used initially but the results of the simulation are then tested by using the real system.
1. | A computer
simulation is a computer
program which attempts to duplicate
or forecast the behaviour of a real life system.
|
| 2. | A simulation is a simplified model of
the real life system.
|
| 3. | Simulations are used for three reasons :
| 4. | Simulations function using variables and rules : |
Section 37 : User Interfaces |
A user interface is the method by which a human and a computer system exchange information and instructions.
You may like some programs and dislike others. When you decide whether or not a program is useful you will probably be considering :
It is the job of a user interface to make a program easy to use. Today the user interface is regarded as being so important that up to 90% of a computer program may be devoted to managing it. Software designers use many tools and techniques to help make an interface easy to use. These include :
User interfaces are usually classified as being one of three different types : Command Line, Menu Driven or Graphical User Interface (GUI).
There are three different types of user interface that are in common use. They are :
| Types of User Interface | ||
| Command Line | The user interacts with the computer by typing commands. | |
| Menu Driven | The user interacts with the computer by selecting options from a menu. | |
| Graphical User Interface (GUI) | The user interacts with the computer by using a pointing device such as a mouse or trackball. | |
Each type of interface has its own advantages and disadvantages. Often the type of user interface that is used on a computer system is determined by the operating system. For example most programs that run on computers using a Microsoft Windows® XP operating system have a graphical user interface. Another type of user interface that is less commonly used is speech driven.
Windows® XP is a registered trademark of Microsoft Corporation in the United States and other countries.
With a command line interface the user interacts with the computer by typing commands .
An interaction with a computer using a command line interface usually follows these two steps :
Here is an example conversation in MS-DOS®. The user first asks the computer to go to the directory "c:\apps\dtp". He then instructs it to start the program "word".
![]()
Examples of systems which use a command line interface are :
| Advantages | Disadvantages |
|
|
Very few new computer programs are developed to use a command line interface.
MS-DOS® is a registered trademark of Microsoft Corporation in the United States and other countries.
With a menu driven interface the user interacts with the computer by selecting options from a menu.
A typical program will have many menus which the user can access. Here is an example of one menu from a word processing package :

Menus can be either full screen or pull-down. Pull-down menus are accessed by selecting the menu from a menu bar. Pop-up menus are activated by pressing a button on the mouse.
Examples of systems which use a menu driven interface are :
A bank automatic teller (cash) machine.
A handheld electronic organiser.
| Advantages | Disadvantages |
|
|
With a Graphical User Interface (GUI) the user interacts with the computer by using a pointing device such as a mouse or trackball.
The most popular form of GUI is a Windows, Icon, Menu and Pointer (WIMP) system. The important features of a WIMP system are :
| 1. | Window : An area of the screen which is used to display a particular program or piece of work. Many windows can be displayed on the screen at the same time. e.g.
|
| 2. | Icon : An informative picture / symbol displayed on the screen which the user chooses to select an action. Icons can usually be used to represent software packages, documents and hardware devices. e.g.
|
| 3. | Menu : A list of options which the user can pick from. Menus can be pull-down (selected from a menu bar at the top of the screen) or pop-up (selected by pressing a mouse button). e.g.
|
| 4. | Pointer : A symbol such as an arrow which is moved by a pointing device and can be used to select objects. |
WIMP user interfaces are now very popular and are used on most computers. Examples of operating systems and programs that have a WIMP Interface are :
When you use a program such as a word processor that has a WIMP interface it is often the case that the document you are creating looks exactly the same on the screen as it will when it is printed out. If this is the case then the program is described as being WYSIWYG. This stands for What You See Is What You Get.
| Advantages | Disadvantages |
|
|
MS-DOS® and Windows® XP are registered trademarks of Microsoft Corporation in the United States and other countries.
A speech driven user interface is controlled by a user speaking commands. Speech driven interfaces are not very common at the moment but may become more popular in the future. Commands can be input using a microphone and are interpreted by voice recognition software. Output can be provided either on a monitor or by speech synthesis.
Speech driven user interfaces have a number of advantages over more traditional methods such as command line or graphical user interfaces :
A speech driven interface may need to be trained to recognise the voice of the user. This is particularly likely with systems that understand a wide range of commands. It may be difficult to use a speech driven interface if there is a lot of background noise or if you have a cold that makes your speech unclear.
Speech driven interfaces are often used by in-car mobile telephones. So that a driver does not need to take his eyes off the road or his hands off the steering wheel he is able to control the telephone by speaking commands such as "Dial Emma" or "Hang Up". In the future it is likely that they will be used in devices such as televisions as an alternative to a remote control.
When you are designing an information system you will need to design the user interface. As you will probably be customising a generic package you will have to design your interface to fit in with the facilities the package offers you.
You should try sketching the layout of the screens that you will include in your system before you set the system up. These guidelines will help you develop an appropriate user interface :
| Positioning | Position items in a logical order on the screen. Usually the user will read the screen from the top down and from left to right, so information should be positioned in this order. Related pieces of information (e.g. surname, forenames) should be grouped together. |
| Consistency | Make each screen that the system displays similar to the others. e.g. always use the same colour background, the same style of writing for prompts, always put the titles and any icons in the same place on the screens. |
| Cluttering | Do not clutter the screen by putting too much information on it. |
| Colour | Use colour to highlight - red is often used for warnings. Flashing symbols can attract a user's attention. |
| Sound | Sound can be used to alert users to urgent events such as an error occurring. |
| Help | Include appropriate help information with the system so that the user can discover how to use the system and overcome any problems he encounters. |
| Language | Use simple language. This is particularly important if the system is aimed at young people. |
| Input Devices | Choose appropriate input devices. e.g. mouse, keyboard, bar code scanner. |
If you are asked to evaluate or select a software package then you will need to look at what functions the package can carry out and the quality of the user interface.
Here is a list of some points you could consider when evaluating a user interface :
For some applications a special purpose user interface is required. These are applications for which a standard user interface on an ordinary computer is not suitable. Here are two applications for which this is the case :
| Flying an Aircraft | Pilots use computers to fly aeroplanes. But a pilot does not fly an aeroplane using a mouse and a monitor. The pilot would not be able to control the plane quickly enough to prevent a crash with a mouse and there is not enough space on a monitor to give the pilot all the information he needs. Instead specialised input devices such as a yolk, pedals and many banks of switches and levers are input devices. Output devices such as computer monitors, dials and warning buzzers are used to pass information to the pilot. |
| Automatic Teller Machine (ATM) | People who use a cash machine (ATM) do not want to have to learn how to use a computer to get money. So a very simple menu driven interface which uses a small keypad and card slot as input devices is employed. Output is provided by a monitor, a small printer and the hole that the money comes out of. |
A special purpose user interface consists of not only software but also all of the input devices and output devices used to enable communication between the user and the computer.
1. | A user
interface is the method by which a human and a computer system exchange
information and instructions.
|
| 2. | When you select a software
package to use you will base you decision on what the
software can do and the quality of the user interface. These points will help you
assess the quality of the interface :
|
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Section 38 : Algorithms & Charts |
An algorithm is a description of how to carry out a process. An algorithm lists the steps that must be followed to complete the process. Algorithms can be described using a language such as English. Here is an algorithm which describes how to make a telephone call :
Descriptions like this are often ambiguous and open to misunderstanding. Therefore various formal methods of describing algorithms have been developed. The simplest methods are the flowchart and the system flowchart.
A flowchart consists of a sequence of instructions linked together by arrows to show the order in which the instructions must be carried out. Each instruction is put into a box. The boxes are different shapes depending upon what the instruction is. The main four types of box are :

Flowcharts are often used to describe in detail algorithms that will be carried out by a computer. When a computer carries out an algorithm the computer is said to execute the algorithm. Execution is also sometimes referred to as running.
Here are some example situations in which flowcharts are often used :
| Control Systems | The operation of a control system can be described using a flowhcart. | |
| Macros | The actions that a macro should execute can be planned using a flowchart. | |
| Computer Programs | Computer programs can be designed by drawing flowcharts to show what instructions the program should execute. |
Sometimes a more general view of how an information system will operate is required. A flowchart for a complete information system would cover many pages of paper and would be very difficult to produce and understand. A more general description of how an information system operates can be given by using a system flowchart.
Flowchart Example One : Simple Greenhouse Temperature Control System
This control system is used to keep a greenhouse warm in the Winter. It keeps the temperature of the greenhouse above 20°C. If the temperature drops below 20°C then a heater is turned on to warm the greenhouse up.
The important components of this system are :
The control system has these input and output devices :
| Input Devices | Output Devices |
| Temperature Sensor | Heater |
The operation of the system is described by this flowchart :

Flowchart Example Two : Macro To Sort A Football League Table
A spreadsheet has been created which shows the league positions of some football teams in a league. Whenever a team plays a match the team's points score and position in the league may change. After each match the league table must be sorted to put the teams in the correct order. The actions required to complete this task in the spreadsheet are :
A macro has been created to automate this process. The macro is described by this flowchart :

Flowcharts describe in detail how a process will be carried out. Sometimes during the development of an information system it is useful to be able to produce a more general description of how a system will work.
A system flowchart shows in general terms the operations that will be performed on information in an information system. The arrows on a system flowchart show the direction that data will flow in around the system rather than the order in which the operations will be carried out.
Many more symbols are used on a system flowchart than on a normal flowchart. These are the symbols that may be used :

A car repair garage uses an information system to produce invoices and keep track of the parts it has in stock. The system uses two files :
When a repair is completed the mechanic records the parts that were used on a form. These parts are then entered into the computer by an operator. The list of parts that is entered is checked against the stock list to reduce the likelihood of the operator making a mistake. If the operator enters the name of a part that does not exist then an error report is displayed. When the parts list has been entered the cost of the parts is looked up in the stock file and an invoice (bill) is printed for the customer.
Every night the computer system checks the stock file. A report is printed to indicate which parts need to be ordered from the garage's suppliers. Details of any orders are placed in the orders file.
When a delivery of new parts is made to the garage the person making the delivery gives the garage a delivery note. The delivery note contains a list of the parts that have been delivered. The list of new parts is entered into the computer by an operator. If any parts have been delivered that were not ordered then an error report is printed. When an order is delivered the information about the order is removed from the orders file and the stock file is updated.
The structure of this system can be shown using the following system flowchart :
1. | An algorithm
is a description of how to carry out a process. An algorithm lists the steps that must be
followed to complete the process.
|
| 2. | When a computer carries out an
algorithm the computer is said to execute or run the algorithm. Algorithms are entered
into a computer using a programming language.
|
| 3. | A flowchart
consists of a sequence of instructions linked together by arrows to show the order in
which the instructions must be carried out.
|
| 4. | These symbols are used to produce flowcharts :
| 5. | A system
flowchart shows in general terms the operations that will be performed on
information in an information system. The arrows on a system flowchart show the
direction that data will flow in around the system.
|
| 6. | These symbols are used to produce system flowcharts :
| |
Section 39 : Programming |
For computer hardware to perform a useful task it must be given a set of instructions to tell it what to do. A program is a sequence of instructions which tells the hardware how to carry out a particular job.
New programs are usually only created if there is no existing software package that will perform the same job. Writing a program involves a lot of work so if you can carry out a task with an off-the-shelf package such as a database you will probably find it much easier and cheaper to use the existing package. Developing a sophisticated computer program may take many thousands or even tens of thousands of man hours.
Because developing a program is a complicated task it is important that the program is planned properly before it is written. Programmers usually follow the systems life cycle when developing a program. Tools such as flowcharts are used to plan how a program will operate. The programs that you use such as computer games, utilities and desktop publishers were all created with a programming language.
There are different levels of programming language. Most computer programs are written in a high level language but for some tasks a low level language must be used.
A computer can only process (execute) instructions that are written in machine code. A machine code instruction is a sequence of 1s and 0s. An example instruction which tests if a bit in memory is set to 1 is 0010100101110100110110. The machine code program below will convert an upper case letter stored in a particular memory location to lower case :
| Machine Code Program | Explanation |
| 000011010100101010000000 | Load the contents of memory location E00 into the accumulator. |
| 01101001 | Clear the carry flag. |
| 0010101001000000 | Add 32 to the content of the accumulator. |
| 000001010100101010000000 | Store the result back in memory location E00. |
As you can see the program is quite difficult to understand! An assembly language is a set of simpler instructions (or mnemonics) which correspond to the machine code instructions that a computer understands. The assembly language equivalent of the program above is :
| Assembly Program | Explanation |
| LDA &E00 | Load the contents of memory location E00 into the accumulator. |
| CLC | Clear the carry flag. |
| ADC #32 | Add 32 to the content of the accumulator. |
| STA &E00 | Store the result back in memory location E00. |
The program is still quite difficult to understand, but the instructions used in the program are much easier to remember than the binary codes in the machine code program.
A program called an assembler must be used to translate a program which has been written in an assembly language into machine code so it can be executed. Software such as operating systems and embedded control systems which must run in computers with only a small amount of memory are usually written in assembly language. For example a program to operate a washing machine would probably be written in assembly language.
Advantages and disadvantages of using assembly languages to produce programs are :
| Advantages | Disadvantages |
| It is much easier to learn assembly language instructions than
machine code instructions. But it is still fairly hard to
remember the instructions. Programs written in assembly language can run faster and use up less memory than programs to do the same job written in a high level language. | Programs written in assembly language on one computer
will not work on a different type of computer. A programmer needs to know an awful lot about the computer hardware he is using to write a program in an assembly language. |
High level languages were developed to simplify programming further. Most high level languages were first created in the 1960s and 1970s when computer hardware became much more powerful and hence speed of execution was less important. High level languages use instructions which are much more like written English. Each high level instruction can do the job of many low level instructions.
Many different high level languages are available. Here are some examples :
| C++ | A general purpose language which can be used for most tasks. C++ programs usually execute faster than programs written in other high level languages. |
| COBOL | Used for business applications such as customer databases. |
| BASIC | A general purpose programming language originally designed for use on home computers. |
| Logo | Developed for use in education, used to draw pictures and control devices such as a robot turtle. |
Each programming language has its own commands and structures that can be used. The allowed commands and structures are known as the syntax of the language.
Because a computer can only execute instructions that are written in machine code, a high level language program must be translated into machine code before it can be used. This task can be carried out automatically by computer software.
Advantages and disadvantages of writing a program in a high-level language are :
| Advantages | Disadvantages |
| Instructions are much easier to remember and use than assembly
language instructions. High-level programs are much easier to understand than assembly language ones. Fewer instructions are required to write a program than when using assembly language. A program can usually be developed much more quickly using a high level language than an assembly language. A program written in a high level language on one type of computer can usually be converted to operate on another type of computer quite easily. Because of this high level language programs are described as being portable. | High-level language programs normally take up more space and execute more slowly than equivalent assembly language programs. |
High level language programs must be translated into machine code before they can be executed. This can be done automatically using either an interpreter or a compiler.
Programs are often developed using an interpreter because an interpreter can execute working parts of a program even if some parts do not yet work. When the program works properly it is then compiled so it will run faster and use up less memory. Most sophisticated, large computer programs are written using high-level languages.
Some languages such as BASIC usually use an interpreter. Other languages such as Pascal normally use a compiler.
1. | A program is
a sequence of instructions which tells the computer hardware
how to carry out a particular job.
|
| 2. | A computer programmer will follow the
systems life cycle when writing a program and will make use of tools such as
flowcharts to design the program. |
| 3. | Programs can be written using either
a low level language or a
high level language.
|
| 4. | There are two low level languages. They are machine code and assembly language.
| 5. | A computer can only execute (carry out) a program which is written in machine code.
| 6. | An assembly language is a set of simpler instructions (or mnemonics) which correspond to the machine code instructions that a computer understands.
| 7. | High level
languages use instructions which are much more like written English than assembly language
or machine code instructions. Each high level instruction can do the job of many low level instructions.
|
| 8. | There are many different high level
languages such as C++, COBOL,
Logo and BASIC.
Different languages were developed for the production of different types of program and
for different users.
|
| 9. | High level language programs must be translated into machine code before they can be used. This is done automatically by a piece of software known as a compiler or by an interpreter.
| 10. | This table lists some of the advantages of using low level languages and high level languages to produce programs :
|
Section 40 : Data Transfer |
When producing work computer users often need to put together information from a variety of different software packages. For example a user might want to include a table of data from a database in a word processed document. There are two ways in which data can be transferred between applications like this.
Method 1 : Copy and Paste
Some packages will let you copy data from one application and paste it into another using the standard copy and paste facilities provided by the operating system. Copied data is placed temporarily onto a clipboard. The data can then be pasted from the clipboard into another application. This is especially likely to work if the two applications have been produced by the same company.
Method 2 : Importing and Exporting Using Files
A file saved from one package can sometimes be loaded into another package. Again this is more likely to work if the two packages were produced by the same company. Unfortunately every computer package stores files in a different way so this method will not usually work. There are however a variety of standard file formats which most packages can use to save and load data. Work saved in one of these standard formats can usually be loaded into another package.
| Exporting | The process of saving a file from a package in a standard file format is known as exporting. |
| Importing | The process of loading a file stored in a standard file format into a package is known as importing. |
Different standard file formats exist for different types of information such as text, data, graphics, sound and video. The importance of storing information in a standard format has grown as more people use the Internet. People use standard formats such as MP3 and MPEG to exchange music and video on the World Wide Web.
There are two common file formats for storing text files such as those produced by a word processor. They are :
Text File (TXT) : A text file is the simplest type of file which can contain text. The file stores only the characters that have been typed. No information about how the text should be presented is included in the file.
Rich Text File (RTF) : A rich text file contains text and some limited information about the text layout. Layout information such as font size and style can be stored. More complicated layout features such as page margins and tables can not be used.
The individual characters in a text or RTF file will be stored using a standard code such as ASCII. If possible the rich text file format should be used to transfer text as it will preserve most of the formatting of the text that has been done.
Files containing data are used to store data that is being transferred in to or out of a database. There are two common formats for these files. The two formats are very similar.
Comma Separated Value Files (CSV) : Each record in the database is represented by a line of text. The fields in each record are separated by commas. Sometimes the field names are included in the first line of the file. Here is an example CSV file containing the names of two people.
Surname, Forename, Title Smith, John, Mr Bloggs, Joe, Mr
Tab Separated Value Files : Tab separated value files are identical to comma separated value files except for one minor difference. This is that a <Tab> character is inserted between each field instead of a comma.
CSV and Tab Separated Value files can only store the data that exists in a database. They can not store other information such as any queries or reports that have been defined.
There are three standards formats used for storing graphics files. They are :
Bitmap File : Bitmap files store images by remembering the colour of each dot (known as a pixel) used to make up the image. Bitmap files usually take up a lot of storage space. They are a standard in the sense that most graphics packages can save data as a bitmap file. However computers using different operating systems have different formats for bitmap files.
GIF File : A GIF file is a compressed graphics file. Instead of storing information about individual pixels in an image a GIF file stores information about sequences of pixels. GIF files take up less space than bitmap files to store but usually take up more space than JPEG files. An image saved as a GIF file will look exactly the same as the original image.
JPEG File : JPEG files are highly compressed graphics files. JPEG files can store an image in a very small space. However some detail can be lost from an image when it is stored as a JPEG file.
The GIF and JPEG standards are particularly important. Any image that is to be displayed on the Internet must be stored in one of these two formats.
There are two related standards for storing and transferring video and music files. They are :
As MPEG and MP3 files are relatively small they can be transmitted quickly across the Internet. This has resulted in many people exchanging videos and music online. These are usually copyright, and downloading copyright material is illegal. The record producing industry in particular has suffered with record sales falling considerably as people illegally copy music for free.
Another standard for storing music files is MIDI :
1. | It is useful to be able to transfer
data between two different packages. If this is possible then the user can create
documents containing a variety of different types of data. e.g. graph, text, picture.
|
| 2. | Data can be transferred between
packages using either copy and paste or
standard file formats.
|
| 3. | The process of saving a file from a
package in a standard file format is known as
exporting.
|
| 4. | The process of loading a file stored
in a standard file format into a package is known as
importing.
|
| 5. | The importance of storing information in a standard format has grown as more people use the Internet. People view images and exchange music
and video using standard formats such as JPEG, MP3 and MPEG. If there were no
standards this would not be possible.
|
| 6. | The two standard file formats for files
containing writing are
text files and
Rich Text Files (RTF). Rich Text Files preserve more
information about the layout of a document than text files can.
|
| 7. | The two standard file formats for
data files are
Comma Separated Value (CSV) and
Tab Separated Value. These two formats can store
the records that are held in a
database but can not store other information such as any
queries that have been defined.
|
| 8. | The three most common standard file
formats for graphics files are
bitmap, GIF and
JPEG. Bitmap files are usually large and
the bitmap format used differs between computers with different
operating systems. GIF files take up less space. JPEG files are
the most compact format but some detail can be lost from
images saved as JPEG files. GIF and JPEG formats are used to store images on the
Internet.
|
| 9. | There are three standard file formats for storing and transferring sound and video files. These are :
|
Music and videos are often exchanged over the Internet as MP3 and MPEG files. It is illegal to exchange copyright material in this way. |
Section 41 : Social Issues |
The widespread use of computers together with changes in communications technologies have significantly changed many peoples lives. Indeed, the impact of the computer on society is so great that the current increasing use of computers is often referred to as the "Information Revolution". It is likened in the scope of its impact to the industrial revolution of the 18th and 19th centuries which completely changed the structure of industry and society. Here just a few of the most significant issues are discussed.
| Impact on Lifestyles | |
| Impact on Employment | |
| Impact on the Environment |
Use of Leisure Time
Cheap personal computers are now owned by many households. People, especially children, spend a lot of time using their computers. The more time children spend playing on their computers the less time they have for more social activities and the less exercise they get. There is some concern about how this affects their ability to interact with other people. However it is also argued that computers can help children with less well developed socialising skills to learn to interact better with other people. Such children often find it easier to communicate with other people via a computer than in person. Communication via computers acts as a stepping stone towards normal communication.
Some groups are also concerned that violent computer games can affect the behaviour of some children.
Increasing automation of industrial production systems, together with the availability of many services such as shopping and banking via the Internet are partly responsible for the fact that in most Western countries people have more leisure time than in the past.
Personal Information and Privacy
The availability of cheap information processing and storage systems enables companies to store large quantities of personal information about you. Many companies and organisations such as clubs or the government keep information about you. This information is usually made available (for a price) to other companies who might be interested in selling products to you. Some people are worried about how "Big Brother" could put together all this information to build up a dossier on you. The prospect of a National Identity Card which everyone would have to carry and could electronically store information about you increases these concerns. Biometric data that would uniquely identify a persom could be stored on such a card or on a database linked to the card. On the other hand a national identity card may be a good thing as it would make it easier to trace people. This could help catch criminals and terrorists.
People are concerned that companies which store information about them may not respect their privacy and may misuse the data. The Data Protection Act regulates what companies may do with information they hold about individuals within the UK, but many countries do not have laws that are similar to this. Some people do not think that the Data Protection Act goes far enough to protect peoples privacy.
Communications and Availability of Information
Improvements in communication technologies have reduced the cost of sending information around the world :
These factors have resulted in the use of the phrase "Global Village" which describes the situation in which people around the world can all share the same information as if they lived together in a small village.
The growth of the Internet has provided a new interactive channel through which information can enter and leave peoples homes. The World Wide Web enables a rich variety of information including text, sound and video to be viewed. Using a credit card it is possible to shop and buy services with your computer. This is known as e-commerce.
Because no one has control over the information placed on the Internet it has become effectively impossible for governments to censor the information that is available. There is no way in which the UK government can control the content of web servers in other countries, especially less developed countries. This places an extra burden on the users of such services. Parents have a responsibility to ensure that their children only access suitable material and all users have to view information obtained from the Internet with caution. Filtering systems can be used to make it less likely that people will access inappropriate material, but these systems are not perfect.
The lack of any control over the information that can be put onto the Internet may have positive effects in some countries which are less democratic than the United Kingdom. The Internet makes it increasingly difficult for authoritarian regimes to control the flow of information to citizens and promotes freedom of information. Student uprisings against the government in Indonesia were organised by electronic mail. Some governments, concerned about the free flow of information make it either very difficult or illegal for private individuals to own or use modems.
The fact that people can communicate with others from different countries allows them to find out about other cultures and ways of life. However the domination of the English language on the Internet and the fact that many web sites are based in America may lead to cultural homogenisation, where the differences between cultures and lifestyles are reduced as more people are exposed to the same information and influences.
Electronic mail has also enabled some people to work from home as tele-workers.
Because it is relatively expensive to connect to the Internet, access is restricted to those who can afford it. This means that many people will be unable to receive email or to access the world wide web. As use of the Internet becomes more widespread this could amount to discrimination against the poor and those who are not technically aware.
Small Communities
People who live in small communities and in remote areas of the world have traditionally found it hard to communicate with other people, to earn a living, and to get access to services such as education. Young people have often moved away from their place of birth to look for a better job or to meet more people. Computers can help to make life in a small community more sustainable in many ways :
People with Special Needs
Some people face physical or mental difficulties that makes it harder for them to carry out certain tasks. Blindness, poor eyesight, poor hearing and physical limitations can make it hard to carry out everyday tasks. Computer systems can be used to help people to overcome these problems. For example :
Control Systems in the Home
Many devices in the home now incorporate computerised control systems. These devices such as washing machines, burglar alarms and video recorders make life easier and give people more choice about how they spend their leisure time. Unfortunately some people feel pressurised into buying the latest DVD player, mobile telephone etc. This can cause people to get themselves into debt as they buy products that they can not afford.
Education
The use of computers has started to change the way that people learn, and is likely to continue to do so :
Dependency
Computer systems are now involved in many of our everyday activities. For example :
Some people are worried that we are too dependent on computers. What would happen if some of the computers stopped working ? How would we manage if we couldn't take money out of banks or if traffic lights stopped working ? Of course the companies who produce these systems take measures to make this very unlikely, but there is always a possibility that things can go wrong.
Unemployment
The introduction of information technology into many workplaces has caused unemployment. The area most affected has been manufacturing industry (e.g. car production) where human production lines have been replaced by robots and control technology. To a lesser extent office workers have been affected by the introduction of information processing systems.
However it can be argued that many of the manufacturing jobs that have been lost as a result of the introduction of computer technology would have been lost anyway. Most of the lost jobs were low-skilled jobs which would otherwise have been transferred to poorer countries where less well educated workers would perform the work for less money.
Training
The impact of information technology is now also being felt in the retail sector as many services are being offered for sale over the Internet. Banks and financial institutions are closing branches throughout the country and providing on-line and telephone banking systems instead. Many other products which are suitable for posting can be purchased over the Internet by e-commerce and supermarkets have introduced home shopping and delivery services.
This has resulted in a change in the type of work that people employed by many companies have to do, and a need for workers to retrain to use modern technology. This has been particularly difficult for older workers who have had little previous experience of computer equipment. The systems used in many industries now change so frequently that people need to be retrained every few years.
Home Working
Cheap communications, the availability of broadband technology and applications such as electronic mail and video conferencing have made it possible for some people to work from home. This can be very helpful for some employees. For example :
The downside of teleworking is that many "teleworkers" find that they actually work longer hours now that they work from home, as there is no clear dividing line between work and leisure time.
New Jobs
The computer industry has also created jobs. Some careers, such as programming and systems analysis have been created directly. Further employment has been created indirectly. Technology based jobs tend to be well paid, and well paid workers have more money to spend in their leisure time, creating employment in the leisure industry.
Globalisation
Globalisation is the increasing integration of industry and economies around the world. The world wide web gives companies the ability to advertise their products worldwide and by using e-commerce to let customers buy their products from anywhere. This increases the amount of goods that are bought and sold between countries and so contributes to globalisation.
The widespread use of computers has produced a rise in the amount of electricity being used. This will increase the amount of damage done to the environment through power generation at conventional or nuclear power stations.
The computer has, however, had a positive impact on some aspects on the environment. If people are able to tele-work form home then less people will need to travel to work so there will be less environmental damage caused by transportation.
The Internet and improved telecommunications may also have positive environmental effects. People are able to obtain information without having to travel from their homes, and the use of electronic mail and the World Wide Web to distribute information could reduce the amount of paper used, hence saving trees.
Advanced data logging systems operated from satellites and other locations enable the collection of important environmental data which can be used to assess the state of the environment. Advanced computerised control systems can often carry out tasks in a way that causes less damage to the environment that older mechanical methods. For example cars with computerised engine management systems produce less exhaust gasses.
1. | The impact on society of the
use of computerised information systems is known as the
Information Revolution.
|
| 2. | This table summarises some of the most significant changes that have occurred as a result of the use of information technology.
|
Section 42 : Banking |
Most people keep their money in bank accounts. It is safer and more convenient to store money in a bank than in cash, especially if a large amount of money is involved. If you keep money in a bank you can also earn extra money, called interest, for doing so.
This table lists some of the common tasks that people carry out using their bank accounts :
| Task | Details |
| Withdraw and Deposit Money | People need to be able to take cash out of their bank accounts to pay for goods that they purchase. They also need to pay in money that they have received such as wages or presents. Cash can be withdrawn and deposited at a counter within a bank. It can also be withdrawn from Automatic Teller Machines (ATMs) outside banks. |
| Pay for Purchases and Services | It is inconvenient and potentially unsafe for a person to carry enough cash to pay for very expensive items. Therefore banks offer alternative payments methods which do not involve the use of cash. Purchases can be paid for using a Debit or Credit Card or by Cheque. |
| Make Regular Payments | Most people have to make some payments on a regular basis. For example a mortgage might have to be paid every month and an electricity bill might need to be paid every three months. Bank customers can have these bills paid automatically using a direct debit or standing order. |
| Accept Payments | People usually receive regular payments of some kind. Most employees receive wages on a regular basis and these are usually paid directly into the employee's bank account by the company he works for. Payments like this can be carried out using the Bankers Automated Credit Systems (BACS). |
| Check Account | A customer will often want to check the balance of his bank account to see how much money is available to spend. He may also want to see what payments and receipts have occurred recently. This can be checked immediately on an ATM. Additionally a customer will recieve a regular printed list of transactions on his account as a statement. |
A large bank may have several million customers, each of whom could have two or three accounts. A bank will therefore have a lot of information to process and so all banks use computerised information systems to manage customer accounts.
A large bank could have several million customers and around 20 million accounts to manage. Every day there could be many transactions (payments and receipts) on each account. Information about each of these transactions must be stored so that the bank has an accurate record of what has happened to the money in each account.
Because of the massive quantity of information that must be dealt with, all banks use computerised information systems to manage customer accounts. A computerised system will provide many advantages over a manual system :
| Advantage | Details |
| Storage Space | A computerised
infomation system can store a massive quantity of information electronically in a small amount of space
using a hard disk or other storage device.
|
| Availability of Information | Information about every account held at a bank has to be available to all of the banks' employees and customers around the world. A Wide Area Network can be used so that information stored on a central accounts database can be viewed anywhere. |
| Fast Information Retrieval | If account information is stored in a computerised information system then it can be retrieved very quickly if a transaction processing system is used. The details of a particular customer's accounts can be looked up in a few seconds. |
| Automation | When a customer pays for an item using a debit or credit card, money must be transferred from his bank account to the account of the company that he has purchased the item from. A computerised information system can carry out this transfer automatically without the need for human involvement. With hundreds of millions of transfers taking place every day a manual system could not cope. |
| Security | It is important that information about a person's bank account remains confidential and that unauthorised people can not change this information. Computerised security features such as username and password logins and encryption can ensure that the information remains secure. |
Customers who have a current account at a bank are issued with a debit card. This can be used to pay for goods by EFTPOS in shops and over the telephone and Internet. It can also be used to guarantee cheques and to withdraw money from an ATM.
A debit card looks like this :

Information is printed on the front of the card in human readable form. The card number, card issue date, card expiry date, name of the account holder, account sort code and account number are all printed.
Information is stored on the back of the card in machine readable form on a magnetic stripe. The card number and expiry date are stored here. This information can be read into a computer automatically using a card reader.
Newer debit cards also contain a small microchip on the front of the card. This can be identified by the metallic terminals which are used to connect the card to a computer. Cards like this are smart cards. The microchip can store much more information than the magnetic stripe can.
A credit card looks like a debit card and can be used in exactly the same way. When you pay for an item with a debit card the cost of the item is immediately taken out of your bank account. Therefore you can only purchase items that you have enough money to pay for.
When you pay for an item with a credit card you do not have to pay for it immediately. Instead the bank that issued the credit card pays for the item. Every month you receive a bill listing the items that you have purchased that month using your card. You do not have to pay for the items until you receive the bill. This means that it is possible to purchase items before you have enough money to pay for them.
When you receive a credit card bill you can pay it straight away and just pay the cost of the items that you have purchased. Alternatively, you can choose to pay a smaller amount and pay the rest later. If you choose to do this then you will have to pay extra money called Interest to the bank as well as the cost of the items.
A customer can withdraw money from his bank account by using his debit card in an Automatic Teller Machine (ATM). ATMs are located outside banks and in other public areas.

To withdraw money the customer inserts his debit card into the appropriate slot on the ATM. The customer's card number is read automatically from the magnetic stripe on the card. The user must then type a four digit numeric password into the machine using a numeric keypad. This password is known as a Personal Identification Number or PIN.
The ATM sends the Card Number and PIN to the bank's central database using a modem and telephone line. This information is encrypted before it is sent to make it more difficult for hackers to steal it.
If the card number is valid (card not expired or stolen) and the PIN is correct then the customer will be given access to his account. If the PIN is incorrect then the customer is given two more attempts to enter it correctly. After three failed attempts the machine will confiscate the card.
An ATM has a menu driven user interface which can be used by customers with little or no experience of computers. By pressing buttons next to menu options displayed on the monitor a customer can access a number of services :
| 1. | Cash can be widthdrawn from a bank account. |
| 2. | The current balance of a bank account can be checked. |
| 3. | A list of the recent transactions on a bank account can be viewed. |
Some banks offer extra services at ATMs such as the ability to transfer money from one bank account to another.
EFTPOS is an abbreviation for Electronic Funds Transfer at Point Of Sale. It is the most convenient method of paying for most purchases. Items can be paid for by EFTPOS using a debit or credit card.
This is the procedure that is followed to make an EFTPOS purchase from a company :
1.
| The cost of all of the items to be purchased is added up, usually on a computerised till.
| 2.
| The customer presents his debit or credit card to the shop assistant.
| 3.
| The card is swiped through a magnetic stripe reader to input the card number and expiry date into a computer.
| 4.
| The card number, payment amount and identity of the company that has sold the goods is sent to the bank's computer using a
modem and telephone line.
| 
5.
| The bank's computer will look up the customer's account details in an accounts
database.
| 6.
| If the card is valid and the customer has enough money in his account then the payment is approved.
| 7.
| A voucher is printed with the card number and purchase details on it.
| 8.
| The customer must sign the voucher to authorise a payment.
| 9.
| The sales assistant will verify that the signature matches that on the back of the debit card.
| 10.
| The money is transferred electronically from the customer's bank account to the company's bank account.
| | ||||
Sometimes the card number can not be read automatically from the card by the magnetic stripe reader. If the magentic stripe has been damaged then the sales assistant can enter the card number using a small keyboard.
If the card is not valid or the customer does not have enough money to pay for the goods then an error message is printed onto the voucher to indicate that the purchase has not been approved.
Hardware Requirements
To process EFTPOS purchases a company must have a small computer called an EFTPOS terminal. An EFTPOS terminal includes these hardware devices :

In large stores such as supermarkets the EFTPOS Terminal is usually built into the till. This means that the sales assistant does not have to type the payment amount into the terminal and the same printer can be used to print till receipts and EFTPOS vouchers.
Advantages and Disadvantages of Paying be EFTPOS
| For Customer Making Purchase | For Company Selling Goods | ||||
| Advantages |
|
Before the invention of debit and credit cards anyone who wished to pay for an item without using cash had to use a cheque. Cheques can still be used to pay for goods and are often used when payment must be made by post.
The Information on a Cheque
A bank customer is issued with a cheque book which typically contains 25 cheques. Each cheque looks like this :
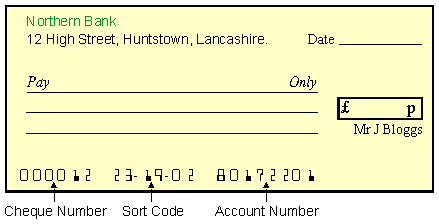
Some information is printed on the bottom of each cheque using a special magnetic ink. This can be read by a human and also by a computer using Magnetic Ink Character Recognition. The printed information is :
1.
| A cheque number which uniquely identifies the cheque.
| 2.
| A sort code which identifies which bank and which branch the cheque comes from.
| 3.
| An account number to identify which bank account money should be taken out of when the
cheque is used.
| |
Using a Cheque
To pay for an item by cheque a bank customer must fill in the blank spaces on the cheque and sign it. This cheque has been completed :
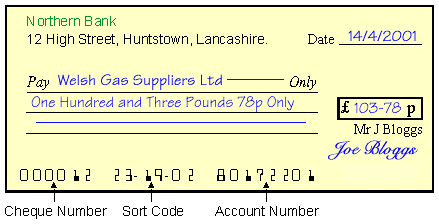
The customer has written this information onto the cheque using a pen :
1.
| The name of the company that the payment is to.
| 2.
| The date that the payment is being made on.
| 3.
| The amount of money to be paid, which is written in both words and figures.
| |
Writing the amount out twice reduces the likelihood that the customer will accidentally write the wrong amount. It also makes it harder for someone else to change the amount later on. The bank will use the signature to verify that the cheque has been filled in by the authorised customer and is not a forgery.
When the cheque is completed the customer will hand it or post it to the person that he has purchased items from. This person will then send the cheque to the bank so that payment can be made. The payment will not be made until the bank has received and cleared the cheque.
The Clearing Process
Clearing is the process used by a bank to verify that cheques are genuine and to transfer the money from the bank account of the person who wrote the cheque out to the bank account of the person that the cheque is made payable to. This is how the clearing process works :
1.
| The person who has received payment by cheque takes the cheque to his bank and tells
the bank the account number of the account that the money should be paid into.
| 2.
| The signature on the cheque is compared to the signature that the bank has on record for
the customer to verify that the cheque is genuine.
| 3.
| The amount of the cheque is read by a human operator and typed onto the cheque in magentic
characters so that the rest of the clearing process can be completely automated.
| 4.
| Batches of cheques are then fed into an automated
MICR reader which can process around 3000 cheques per
minute.
| 5.
| The computer checks that the person who made the cheque out has enough money in his bank account
to pay the amount written on the cheque. If he does not have enough money then the
cheque is rejected.
| 6.
| The amount written on the cheque is transferred from the account of the person who
wrote the cheque to the account of the person who received the cheque.
| 7.
| Finally the cheque is stored so that it can be retrieved later if there is any query
about the payment.
| |
The clearing process is quite complicated and can take up to seven days to complete. This means that someone who has been paid by cheque may have to wait for a whole week until the payment is actually received. If the person who wrote out the cheque does not have enough money to make the payment then it can be very difficult for the person who received it to obtain the money.
Advantages and Disadvantages of Using Cheques
| For People Paying By Cheque | For People Receiving Payment by Cheque | ||||
| Advantages |
|
For most purposes it is usually better to pay by debit or credit card than by cheque.
Periodically each customer at a bank will recieve a statement which lists the transactions (payments and receipts) that have occurred on his account. A statement is usually printed for each customer every month, 3 months or year and then posted to him. A statement will list all of the transactions that have occured on the customer's account since the last statement was produced.
The information that is included on a statement is :
1.
| The name and address of the customer.
| 2.
| The customer's account number.
| 3.
| The start and end date of the period that the statement covers.
| 4.
| A list of transactions that have taken place in the time period covered by the statement,
sorted by date.
| |
Statements are generated from a bank's accounts database. Every day a query is used to select the accounts that need to have statements printed. Then, for each account which requires a statement another query is used to select the transactions that have occurred on the account since the last statement was printed. The gathered information is put together into pages as a report.
A large bank may have to print one million statements every day, so it is important that each statement is printed very quickly. Therefore statements are printed on very fast laser printers. The printed pages are folded by machine and put into envelopes. Envelopes with clear windows are used so that the address printed on the top of the statement can be seen through the envelope.
The Bankers Automatic Clearing System (BACS) is used by companies to automatically transfer money from one bank account to another.
To make payments using the BACS system a company must have a computer with BACS software installed on it. The company must also have a modem to send details about the payments it wants to make to the bank's computer.
Typically a company will use the BACS system to :
To make a payment by BACS a company must send this information to the bank :
1.
| The account number of the account that the money is being paid from.
| 2.
| The amount that is to be paid.
| 3.
| The account number of the account that the money is being paid into.
| 4.
| The name of the person that the money is being paid to.
| |
The bank's computer will validate the payment details. It does this by checking that the account number that the money is being paid into exists, and by checking that the account belongs to the named person. If the account does not exist or does not belong to the named person than the payment will not be made and an error message will be sent to the company that tried to make the payment.
Most people have to make regular payments for services that they receive. For example :
1.
| People who are buying a house have to make mortgage payments every month.
| 2.
| Most people pay for electricity, telephone and gas services every three months.
| 3.
| Other items such as insurance, television licence and subscriptions can also be
paid for monthly.
| |
Making each of these payments manually would be time consuming and error prone, so instead Direct Debits and Standing Orders can be used to make regular payments automatically.
| Standing Order | Used to make a regular payment of a known amount. e.g. £356.71 every month to pay for a mortgage on a house. |
| Direct Debit | Used to make a regular payment when the amount to pay varies. e.g. used to pay a gas bill every three months when the amount to pay depends upon how much gas you have used. The company that is being paid will request the correct amount from your bank. |
For each account a bank will store a list of regular payments that should be made in its database. Here is a list of regular payments to be made from one account which has been extracted from a bank database :
| Type | Pay To | Sort Code | Account No | Frequency | Payment Day | Next Payment | Amount
| SO
| Bury Bank
| 54-10-23
| 93739202
| Monthly
| 14
| 14/4/2001
| £356.71
| SO
| GW Insurance
| 40-10-75
| 10891026
| Monthly
| 16
| 16/4/2001
| £42.10
| DD
| JB Cellular
| 22-32-12
| 21030129
| Monthly
| 12
| 12/4/2001
| N/A
| DD
| Bolton Gas
| 82-10-04
| 43239309
| 3-Monthly
| 15
| 15/6/2001
| N/A
| Key : SO = Standing Order, DD = Direct Debit
| | |||||||
The database calculates the Next Payment date from the Frequency and Payment Day. A query is used to produce a list of all of the payments that must be made on a particular day. The Pay To, Sort Code and Account No fields are used to identify the account that the money should be transferred into.
Automatic payments like this could not be made if a manual information system was used. The amount of work involved in identifying and making the payments would make it impractical.
Many people now have access to the Internet and can communicate with other computers using the World Wide Web. Using a browser package it is possible to view information generated on other computers.
Banks have used this facility to enable people to access their bank accounts from home. Using the Internet bank customers can :
1.
| Check an account balance and view or print a statement.
| 2.
| Transfer money from one bank account to another.
| 3.
| Pay bills.
| 4.
| Set up or cancel direct debits and standing orders.
| |
Some new banks only operate on the Internet. They do not have branches that you can visit. Because they do not have branches it is much cheaper to run an Internet only bank than to run a traditional bank.
Security is a very important issue when customers are allowed to access their bank account details over the Internet. Most banks require that a customer visits or telephones the bank and completes a form before he can access his account on the Internet.
Once this has been done, a username and password will be needed to access the account. Any information sent from the bank over the Internet will be encrypted so that it is difficult for hackers to steal the information. Additionally a log will be kept which will store information about where customers have accessed their accounts from and what they have done.
Advantages and Disadvantages of Internet Banking
| Advantages |
|
| Disadvantages |
|
| 1. Most people keep money in a bank account because it is safer and more convenient to keep money at a bank than as cash. You can also earn interest on money in a bank.
| 2. | People
use their bank
accounts to :
|
|
Section 43 : Supermarkets |
Supermarkets sell food and other household products to customers. Most supermarkets are very large stores which stock a wide range of products. Customers select the items that they want to buy from shelves as they go around a store. After a customer has selected the items he wants to purchase he takes them to a till where he must pay for them.
A supermarket needs an information system which can :
| 1. | Accurately calculate the cost of a customer's purchases. |
| 2. | Try to ensure that the store does not run out of products that customers want to buy. |
| 3. | Take the payment for goods from customers. |
In most areas of the country customers can choose to shop at several different supermarkets. Therefore the supermarket owners must compete with each other to attract new customers and to keep their existing customers.
A computerised information system can automate many activities that must be carried out in a supermarket.
| Function | Why Computerise? | |
| Stock Database | A computerised information system can store information about stock levels in a database. These can be automatically updated using transaction processing as items are sold. The database can automatically produce orders for items which will run out soon to ensure that they are reordered. These could be sent over the Internet or by FAX to the companies that supply the supermarket. | |
| The Till | Each item has a barcode which is scanned at the till to identify it. The price of each item can then be looked up in the stock database which is connected to the till by a network. The till can automatically calculate the total price of a customer's shopping and print an itemised receipt. | |
| Collecting Payment | The tills in the supermarket can be linked by a WAN to the computers that banks use to store customer account details. Using a debit card money can be transferred automatically from a customer's bank account to the supermarket's account to pay for goods. | |
| Collecting Information About Customers | If a loyalty card system is set up then the supermarket can collect information about its customers as they shop. This can be used for marketing or sold to other companies. | |
A supermarket will store information about the products that are for sale as a file in a database. Other information such as supplier details can be stored in other files in the database if a relational database is used.
Structure of the Products File
Here is a small exert from the products file in a supermarket stock database :
| Product Code | Item Name | Stock Level | Re-Order Level | Order Quantity | Price | Category | Supplier Code
| 100200019292
| Spicy Pizza 12"
| 123
| 100
| 200
| £2.49
| FR
| PC
| 100212422323
| Canned Tomatoes 400g
| 742
| 500
| 1000
| £0.24
| TV
| BW
| 102313538763
| Frozen Peas 1lb
| 41
| 30
| 50
| £0.89
| FR
| FV
| 403244976252
| Freshly Squeezed Orange 1L
| 32
| 10
| 25
| £2.59
| JU
| JL
| |
The purpose of each field in the file is listed below :
Information in the category and supplier code fields is coded to speed up data input, reduce storage space and make reports more compact.
Updating the Products File
The products file can be updated for several different reasons. The most common ones are :
| Reason | How Updated |
| Item Sold | Whenever an item is sold the "Stock Level" will be automatically reduced by a computerised till. |
| Delivery | When new items are delivered to the supermarket, the "Stock Level" field of each delivered item will be increased because the supermarket will now have more of the item. This change will be made manually by the person who accepts the delivery. |
| Change in Details | Sometimes an item's details will change. For example the price of the item may go up or the size of the can that the product is supplied in may change. These updates will be carried out manually by a computer operator. |
| Stock Check | Periodically a worker will count the quantity of an item that is actually available on the shelves in the supermarket. If this differs from the "Stock Level" listed on the computer then the database field must be updated to reflect the actual stock level. |
Supermarkets need up-to-date information about the goods they have sold and the goods that they currently have in stock. Therefore transaction processing systems are used, with all updates to the stock database taking place very quickly.
Other Files
The products file will be the most important file in the stock database. Other files could be used to store information such as :
| File | Purpose | Possible Structure | Links To Other Files | |||||
| Suppliers File | Stores information about each supplier that the company purchases items from. |
| Linked to the product file by the "Supplier Code" field. | |||||
| Categories File | Stores information about the different categories of product that the supermarket sells. |
| Linked to the product file by the "Category" field. |
Further files could store more information such as how many units of each product have been sold on different days and how much money has been taken at each till.
After a customer has selected the items that he wants to purchase he takes them to a till to pay for them. Modern tills in supermarkets are actually small computers which are connected together on a local area network. They are known as Electronic Point of Sale (EPOS) terminals.

The network is used to connect the tills to the computer which stores the stock database.
The Payment Process
When an item is sold its product code is entered into the till (EPOS terminal). The product code is usually printed on the item as a number that a human can read and as a barcode which can be scanned using a barcode reader. The information included in the barcode for a product is country of origin, manufacturer and item code. Sometimes a barcode will not scan so the code must be typed on a small keyboard. |
 |
The entered product code is validated using a check digit that it contains to reduce the likelihood that the product code has been typed or scanned incorrectly.
The code is then looked up in the stock database on the store computer to find the product's price and name. If the product code has been successfully scanned and looked up then the till produces three outputs :
The products file in the stock database is updated to show that the item has been sold. The stock level for the product will be reduced.
When all of the items that a customer has chosen have been recorded by the till, the total price of the purchases is calculated and printed on the receipt.
Items Sold By Weight
Some items, such as fresh fruit and vegetables are sold for a certain price per kilogram. These items do not have barcodes printed on them. To find the price per kilogram of an item that is sold by weight the checkout operator must either :
The price per kilo is then looked up in the stock database. The items are weighed on a pair of electronic scales and the computer system automatically calculates the correct price for the item and prints it on the receipt.
Methods Of Paying
A customer can usually pay for his purchases with cash, by cheque or using a debit or credit card. If the customer chooses to pay with a debit or credit card then the till will establish a connection with the computer at the customerís bank to make an EFTPOS transaction.
System Flowchart
Most supermarkets use a transaction processing system to record sales. This means that the products file in the stock database is updated very shortly after each sale takes place. The operation of the sales process is shown in this system flowchart :

A backup copy of each sale will be stored in a transaction log file so that the data can be recovered if the products file is corrupted.
Advantages Of Using Computerised Tills
The use of computerised tills instead of manual tills brings benefits for customers and the owners of a supermarket. Some of these are :
| For Customer | For Store |
|
|
When the stock level of an item becomes low, more of the item needs to be reordered by the supermarket. A supermarket will reorder more of an item before the item is completely sold out because ordered items may not be delivered to the supermarket until a few days after an order is placed.
This is a small exert from the products file in a supermarket stock database :
| Product Code | Item Name | Stock Level | Re-Order Level | Order Quantity | Price | Category | Supplier Code
| 100200019292
| Spicy Pizza 12"
| 123
| 100
| 200
| £2.49
| FR
| PC
| 100212422323
| Canned Tomatoes 400g
| 226
| 500
| 1000
| £0.24
| TV
| BW
| 102313538763
| Frozen Peas 1lb
| 12
| 30
| 50
| £0.89
| FR
| FV
| 403244976252
| Freshly Squeezed Orange 1L
| 32
| 10
| 25
| £2.59
| JU
| JL
| |
The Canned Tomatoes and Frozen Peas need to be reordered. This is because the stock level of these products has fallen below the re-order level at which an order for a new delivery should be placed.
Using Queries and Reports to Print Orders
A database query can be used to automatically select the products which need to be reordered. The criteria for the query will need to be :
Stock Level < Re-Order Level
The items found can be presented neatly as a report listing all of the items that need to be reordered. Here is an example reorder report :

The report only lists the products which need to be reordered. For each product the Product Code, name, quantity to order and supplier code is listed.
A More Sohisticated Printed Reordering System
If a relational database was used then the query could also look up the names and addresses of the suppliers in a supplier file and include these on the report.
A more sohisticated report layout could group together all of the products which need to be ordered from one supplier and print a page for each different supplier. Here is an example reorder report which has been produced to send to Frozen Vegetable Supplies Ltd :

The report could be posted to the supplier of sent by FAX.
Electronic Reordering
An alternative to sending printed orders to suppliers is to send orders electronically. This could be achieved using email or a custom written computer program. Orders could be transmitted from the supermarket to the supplier using a modem and telephone line. This would speed up the ordering process, meaning that goods could be delivered more quickly.

An electronic ordering system is particularly likely to be used if the supermarket is one of a group of supermarkets in a chain. In this case, most of the supermarket's products woud be ordered from a central warehouse which was owned by the same company as the supermarket.
Setting the Reorder Level
An automatic reordering system will only operate properly if the reorder levels are set appropriately to ensure that the supermarket is resupplied with items before it runs out of them. The appropriate reorder level for an item will depend upon :
For example, suppose a supermarket sold on average 150 bottles of orange squash a day and it took three days for a new supply of orange to be delivered. Then to ensure that the supermarket did not run out of orange the reorder level would need to be at least :
3 * 150 = 450
In reality the reorder level would probably be higher than this in case the demand for orange was unusually high whilst the supermarket was waiting for a delivery.
The appropriate reorder level for each item could be set manually by the supermarket's manager, based on his experience. Alternatively it could be calculated by the computer, based on previous sales information and delivery times.
Setting the Order Quantity
The order quantity, i.e. the amount of the item that will be ordered, should be enough to keep the supermarket stocked for a number of days. However most supermarkets do not like to have too much of an item in stock as only limited storage space is available for goods.
The stock level field in the stock database stores a record of how many units of a particular item should be in stock at the current time. This level is adjusted automatically :
However stock can sometimes be added or removed from the supermarket without this being recorded on the database. For example :
| Reason | Explanation |
| Theft | An item could be stolen from the store. This would be removed from the stock, but the database stock level would not be decreased. |
| Checkout Operator Error | When goods are sold they are removed from the stock database as their barcodes are scanned. If a customer purchased a large number of items then the checkout operator could easily forget to scan one of the items by mistake. The missed item would be removed from the stock, but the database stock level would not be decreased. |
| Delivery Error | The person who accepts the delivery of new items at a store could accidently record the number of items or type of items that have been delivered incorrectly. |
The effect of these errors would be that the actual stock level is not the same as the stock level in the database. If the actual stock level was below the stock level in the database then the store could run out of an item before it was reordered.
To reduce the likelihood of this happening a stock check will be carried out periodically. A stock check means that the items that the supermarket sells are counted and the actual stock level of each item is compared to the stock level in the database. If the two do not match then the stock level in the database will be changed to the actual stock level.
It takes a lot of work by members of staff to carry out a complete stock check so this is not done very often, if ever. However stock checks on a small range of items within a store will be carried out regularly.
The Stock Check Device
Stock checks are carried out by a person using a small handheld computer with a built in barcode scanner, keyboard and Liquid Crystal Display (LCD). The computer contains some RAM which is used to store a copy of the information about some of the products, taken from the stock database. The stock check process works like this :
1.
| Before the stock check takes place the information about the products to
be checked is copied from the stock database into the RAM in
the handheld computer.
|
| 2.
| For each item that is to be checked :
|
| ||||||
Any significant differences between the expected and actual stock level will be noted by the computer so that the reasons for them can be investigated.
The handheld computer that is used to collect the information about stock levels is sometimes known as a data logger.
In most areas of the country customers can choose to shop at several different supermarkets. Therefore the supermarkets must compete with each other to attract new customers and to keep their existing customers.
Many supermarkets use a loyalty card scheme to encourage their customers to always shop with them. Under a loyalty card scheme :
Using Loyalty Card Information For Advertising
Whenever a customer uses his loyalty card to shop the supermarket will collect information about how much he spends, where he shops and what products he buys. This information will be used to send targetted advertisements to customers. For example a customer who buys baby food regularly might be sent an advert for childrens clothes or toys.
Sending adverts and offers to only those people who are likely to be interested can significantly reduce the amount of money that a company has to spend on advertising its products. Therefore information about customers' shopping habits is very valuable.
The supermarket could send targetted advertisements out itself or sell information about its customers to other companies. The Data Protection Act controls what use companies can make of this information.
Advantages and Disadvantages of Loyalty Cards
| Advantages of Loyalty Cards | Disadvantages of Loyalty Cards | |
| For Customers | Customers can earn a discount by using a loyalty card when shopping. | Some customers object to supermarkets collecting information about them and using or selling this. They believe it is an invasion of their privacy. |
| For Supermarkets | Supermarkets believe that customers with loyalty cards will shop at their stores more frequently and are less likely to try another supermarket. | A supermarket must set up new computer systems and employ staff to run its loyalty card scheme. The supermarket will have to pay for this. |
Self-Scanning
During busy times queues build up at supermarket tills and customers may have to wait a long time to pay for the goods that they have purchased.
One method that can overcome the problem of long queues is self-scanning. In a supermarket which has a self-scanning system customers scan the barcodes of products as they put them into a trolley using a mini scanner on the trolley.
Ths scanner is connected to the supermarket stock database by a LAN using radio waves. As the products are scanned the total price of the shopping is calculated using the prices in the database. Once the customer has finished shopping the cost of the goods is transferred from his bank account to the supermarket's.
Supermarket employees make occasional checks on the contents of trolleys to ensure that customers are not tempted to put items into their trolleys without scanning them. Before customers are allowed to self-scan they must register with the supermarket so that they can be identified.
Internet Shopping
Some supermarkets now offer their customers the opportunity to shop from home using the Internet. A shopper can log on to a supermarket web site and select the products that he wants to purchase. The supermarket will then deliver these items to him at an agreed time. This is an example of electronic commerce (or e-commerce).
| Advantages of Internet Shopping | Disadvantages of Internet Shopping |
|
|
| 1. Supermarkets sell products to customers. The customers select their goods themselves and then take them to a till to pay for them.
| 2. | A supermarket needs an information system which can :
| ||||||||||||||||||||||||||||||||||||||||||||
Section 44 : Systems Lifecycle |
Developing an information system is a long job. Some of the information systems you develop as part of your GCSE course will take many weeks to complete. Commercial information systems take much longer to develop. A team of many information technology professionals may work on a project for over a year.
Because the development of an information system is such a long process it is important that a structured method is used during the development. The systems lifecycle is the set of stages that are followed when developing an information system. For the purposes of a GCSE course the systems life cycle consists of five stages which must be followed in order. This diagram shows the system life cycle :
The five stages are analysis, design, implementation, testing and evaluation. Modification is not really a stage as such. Modification is changing the information system to correct any problems that you find.
When you tackle a project you should follow the five stages in the systems life cycle, starting with the analysis and ending with an evaluation of the work that you have done. Wherever possible you should complete one stage before going on to the next. You will also be expected to document (i.e. write up) the work that you have done at each stage. After all - you may have tested the system and convinced yourself that it works, but how are you going to convince the person assessing your work ?
When you complete coursework projects for an exam board you may also be expected to produce a user guide so that the person assessing your project can understand how to use it.
Multi-Part Projects
Some projects can be easily divided into a number of distinct tasks such as customer information, payroll, advertising etc. If this is the case then you can tackle each task separately. Try and follow these three steps :
1. | The
systems lifecycle is the set of stages that are
followed when an information system is developed. |
| 2. | There are five stages in the systems lifecycle :
| |||||||||||||||||||
Section 45 : Analysis |
The analysis is the first stage you must tackle when developing an information system. Analysis is the process of deciding what (if anything) the information system should do. It is not concerned with how it will be done. During the analysis you should not discuss which software package you are going to use to produce the system. You do not decide on this until the design stage.
Sometimes it is not clear whether or not it is a good idea to create a new information system to perform a job. If there is an existing system (manual or computerised) doing the same job as the new system will then it may be that a new system would offer few or no benefits over the older system. The analysis should consider whether or not to set up an information system.
The analysis stage of the development of an information system can be broken down into three smaller steps :
| Feasibility Study | |
| Breaking Down The System Into Tasks | |
| Requirements Specification |
The purpose of a feasibility study is to determine whether or not a new information system should be created to solve a problem. The possible advantages of creating a new system must be identified. If there are few advantages then it may not be worth investing in a new system.
Finding Out About Existing Systems
If the job that the information system will carry out is currently being performed by another system then a good starting point for a feasibility study is to examine the existing system. Even if it has already been decided that a new system will be created it is still a good idea to examine an existing system. Any problems with the system can be identified and new ways of performing the job can be considered. A variety of methods can be used to identify how the existing system works. These include :
| Method | Description |
| Interviews | People who operate the current system can be interviewed to find out what they think of it. Interviews can be in more depth than a questionnaire could be. If an interviewee makes a useful point about the system then the person doing the interview can follow the point up to get further information. This is not possible with a questionnaire. |
| Questionnaires | Questionnaires are useful when information about a system has to be gathered from a lot of people. Information can be obtained far more quickly by using questionnaires than carrying out interviews. Because people can remain anonymous they may be more likely to tell the truth than they would in an interview. |
| Observation | Observation of how the current system works and what each person does to use it can give an unbiased view of how the system works. Because the person designing the information system is doing the observation himself it is possible to get first hand information about how the system works. The system developer can identify if any of the workers have been lying about their role in the system. |
| Documentation | Manuals describing how the current system operates can be collected. Any forms used to collect information for the current system or reports produced by the current system can be looked at. |
If there is no existing system then it will be necessary to use other sources of information to decide how a new system should operate. Possible methods of achieveing this include :
Describing An Existing System
Once evidence about the existing system has been collected a description of the system can be produced. In addition to a written description of the system, system flowchart diagrams can be used to show how the existing system operates. Possible improvements to the system can be identified and any advantages of a new system should be noted.
The Decision
At the end of the feasibility study a decision should be made about whether or not to develop a new information system based on the evidence collected.
Usually an information system can be broken down into a number of distinct tasks. For example a system used to manage a car repair garage could be broken down into these tasks :
Breaking down a job into smaller tasks that can be worked on more easily is known as top down design. The work done in the feasibility study should help identify these tasks. From the garage example you can see that some of the tasks are completely unconnected whereas there may be links between the other tasks :
For a small information system the individual tasks can be tackled one at a time. For a large information system different tasks may be worked on by different people. If a task you have identified is still quite large then you may want to break it up into even smaller parts to work on when you produce your design. Continuing to break a task up into smaller parts like this is all part of the top down design process.
From this point on each task should be treated separately. A separate requirements specification, design, implementation, testing and evaluation stage should be produced for each task.
If it is decided that a new information system should be developed then it will be necessary to decide what the system will do. The requirements specification sets out what the new system will do. It will guide the development of the entire project.
A separate requirements specification should be produced for each task that has been identified. Each requirements specification should deal with :
| Introduction | |
| Outputs | |
| Inputs | |
| Desired Outcomes | |
| Alternative Methods |
The information you should include in each section is outlined below. A good analysis will discuss why things are being done and justify them.
Introduction
For each task you need a separate introduction. Whoever assesses your work will not be familiar with the problem that you are tackling and so you should include as much material as possible here. If the assessor does not understand exactly what the task you are tackling is then you are unlikely to gain good marks for the rest of the task.
Outputs
An output is a piece of information produced by an information system. Under the outputs section you should explain what you want the system to tell you. Typical outputs might include :
You should explain what each output is and, if possible, why it is required.
Inputs
An input is a piece of information that is typed into an information system. Based upon the outputs that you want to produce you should be able to decide what information you will need to put into the computer system. This could be :
Desired Outcomes
When you have completed the task you must produce an evaluation of your work. In the evaluation you need to assess the work you have done and compare it to what you hoped to achieve. The results you hope to achieve are known as desired outcomes or performance criteria. To produce a good evaluation you must compare what you have achieved directly to a set of desired outcomes that you produce now. It is therefore vital that you set your desired outcomes out clearly.
The first desired outcomes will be that the outputs you want to obtain are produced correctly. After this desired outcomes should include any other properties that you would like your system to have. Other possible desired outcomes include :
Desired outcomes should be clear and unambiguous. It is difficult to judge if unclear outcomes have been met.
Alternative Methods
This is the first point at which you should consider how you will complete the task. Under this heading you should consider possible methods that could be used to complete the task. You should compare the advantages and disadvantages of :
You need to explain why the computerised solution is most appropriate (if it isn’t choose a different task!).
1. | Analysis is the
process of deciding what (if anything) an information system should do.
|
| 2. | An analysis should include these three steps :
| 3. | The purpose of the
feasibility study is to determine whether or not a new
information system should be created to solve a problem.
Interviews,
questionnaires,
observation and examining
documentation can be used to find out about any
existing system which can then be described using system flowcharts.
The advantages of a new system should be explained and a decision taken on whether or
not to develop a new system.
|
| 4. | Top down
design should be used to break up the new information system into a number of small
tasks which can be tackled separately.
|
| 5. | The requirements specification should set out what the new system will do. It is used to inform the design process and to evaluate the work that has been done once the information system has been created. A separate requirements specification should be created for each task you have identified. Each requirements specification should include these five sections :
|
Section 46 : Design |
Design is the process of deciding how you will set up your information system using the software packages you choose. To produce a good design you need to show how you have arrived at the design you are going to use, and not simply state one design. i.e. you need to justify the choices you have made and perhaps consider alternatives at each step in the design.
The design stage can be broken down into four smaller steps :
| Selecting Software | |
| Selecting Hardware | |
| Planning | |
| Test Plans |
Each task could be tackled in a variety of ways. It is vital that you look at a number of possible alternatives solutions before you start work creating your system. If you do not do this then you could do an awful lot of work only to find out that there was a better, easier way to solve the problem.
You will therefore need to decide which piece of software to use. For example, is a spreadsheet or a database more suitable for keeping records of all of the members of a club ? Factors such as ease-of-use, speed, availability of software, your familiarity with the software, staff training, and the features of a software package will influence your choice.
The three important points you must cover when selecting software are :
One possible way of writing up your software selection is to draw up a table like this example.
In this example a student has to select an appropriate package to write up a science experiment. The write up must include text, a table of results and a graph showing the results.
Having considered the task I have identified a number of different activities that I will need to carry out to write the essay. I have also identified some other activities that would help me write the essay but are not essential. In order of importance these activities are :
I have considered two possible methods of producing the essay. They are (i) using Microsoft® Notepad and (ii) using Microsoft® Works™. Both of these methods are available for me to use. In the table below I have explained how each of the activities can be carried out using each of the methods.
| Activity | Microsoft® Notepad | Microsoft® Works™ |
| Enter and Output Ordinary Text | Text is typed onto the screen. It can be output by selecting Print from the File menu. | Text is typed onto the screen. It can be output by selecting Print from the File menu. |
| Produce Neat Tables | Entries in tables can be lined up neatly using the TAB key. | Tables can be created by Selecting Insert Table from the Insert Menu. Entries are automatically aligned. Borders can be put around the table to improve its presentation. Rows and columns can be easily added or deleted. |
| Draw Graphs | There is no facility to produce a graph. | Works includes a spreadsheet which can be used to produce graphs. They can be cut and pasted into the word processor. |
| Correct Errors | Errors can be corrected before printing by deleting the incorrect text using the DELETE key. Extra information can be added at any point in the document. | Errors can be corrected before printing by deleting the incorrect text using the DELETE key. Extra information can be added at any point in the document. |
| Check Spelling | The essay will have to be read on-screen and any difficult words looked up in the dictionary. If there are any mistakes they can be corrected before the essay is printed. | Spellings can be checked automatically using the Spell Check option. This will identify most mistakes and can suggest the correct spellings. |
| Use Different Styles for Headings | The font can not be altered. Titles can be highlighted by double spacing letters or typing in capitals. | The font and font size can be changed for headings. They can be underlined or made bold to make them stand out more. |
| Number the pages. | The page numbers will have to be typed manually at the bottom of each page. | Page numbers can be included in the footer and will appear on each page. The software works out the number of each page. |
| My Familiarity with the Method | I have used Notepad to edit text files on my PC. | I have previously typed a number of small articles on Microsoft Works. |
The best option is to use Microsoft Works. It will allow me to carry out all the tasks I want to. I can correct my text on screen before printing and Works will help me find my spelling mistakes - saving a lot of time. Tables can be easily created and edited in a range of attractive styles. The spreadsheet can be used to incorporate a graph. A number of different fonts can be used to make titles stand out. Works will also automatically number my pages for me.
Microsoft® Notepad and Microsoft® Works™ are trademarks and/or registered trademarks of Microsoft Corporation in the United States and other countries.
If you have a choice you will also need to choose and justify the hardware (input devices, output devices) you use. As well as justifying your choice of devices, e.g. choosing a printer for an output device, you should also justify the type of device that you are going to use. For example would an ink jet printer or a laser printer be better for a particular job ?
If the hardware that you would prefer to use is not available then you can discuss the hardware you would prefer to use and then explain what hardware you will actually have to use.
You will need to use your common sense to decide what order to design the different parts of the system in. In the documentation you must include evidence that you have produced a design for your system before you created it. The sort of evidence you need to provide will be different for the different parts of the system.
This table gives you some examples of the items you may need to design for a task. It also suggests the sort of evidence that you may want to include for the different types of item designed.
| Type of Task | Items to Include in Plan
| Spreadsheet
|
Database
|
Word | Processing, Graphics or DTP
| |||||||||||||
For most tasks you will also need to describe how the inputs that are to be put into the system will get there. Important points to consider are :
In the desired outcomes section of the analysis you should have made a list of the things that you want your system to do. Before creating the system the last thing you need to do is to come up with a test plan explaining how you will check whether or not your system meets these requirements.
For each requirement that the system should meet you need to describe how you will test if the system does in fact meet the requirement. Each of the tests that you might perform falls into one of two categories :
1. Absolute Tests
An absolute test is a test to which there is a definite pass or fail answer. For example, if you have said that the system should produce a list of all of the books that are out on loan from a library you can test if the system will do this by getting the computer to produce the list and manually checking if it contains the right books or not. You should perform absolute tests with three different types of test data : Typical, Extreme and Erroneous. The table below explains what these different types of data are and gives examples of them for dates and percentages.
| Type | Description | Percentage e.g. | Date e.g.
| Typical Data
| Typical, everyday data which your information system should work with.
| 23, 67
| 23/4/1998, 2/12/2001
| Extreme Data
| Data which is acceptable but is on the edge of the boundaries for which your information system should work.
| 0,100
| 30/6/2001, 29/2/2000
| Erroneous Data
| Data which should not work with you information system. A good information system will
display an error message when erroneous data is entered and will not crash.
| -1, 101, 150
| 31/6/2001, 29/2/2001
| |
2. Subjective (Opinion) Tests
A subjective test is a test in which a judgement must be made by a human about the computer system. e.g. Is the logo that was designed appealing, or is the data collection form easy to understand and complete correctly ? Often there is no definite answer to these questions. The best thing you can do is ask as many people as possible to give you their opinions or to try the system out.
Sometimes you may not be able to think of a way to test a few of the requirements. Or it may be too complicated to test if a requirement is met. It is enough to make sure that you test the majority of the system.
Testing Different Types Of Task
Here are some methods you may use to test whether a computer system works :
| Type of Task | Likely Method of Testing |
| DTP / Word Processing / Graphics | Visual inspection to check that final output matches design, ask other peoples' views on the work - do they understand it, does it achieve its purpose, does it contain all of the required information? |
| Spreadsheet | Perform calculations by hand and compare results to computer output results. |
| Database | Perform queries / reports and check that the records that are output are the correct ones. Check that validation checks accept / reject the correct data. |
For each test you are going to carry out you must state these things in your test plan :
It is quite acceptable for your system to fail some tests. If this happens then you should explain why, and if possible correct the problem(s) then retest. Your system may also fail some tests because you have improved it. For example you may change a poster from its design when you create it because you believe the changes amount to an improvement. If this is the case you must explain why it is an improvement.
Testing can not prove that an information system will work all of the time. But the more testing you do the more confident you can be about how well your system works.
Here is part of a test plan for a project involving a car repair garage. Details of some of the tasks involved in this project can be found here.
| No | Test | Details | Expected Results |
| 1. | Does the stock system correctly warn the owner of which products need to be reordered ? | I will set the stock levels of the parts "Fiesta 1.1 Exhaust", "Peugeot 406 Clutch" and "Astra Left Door Mirror" so that they are below the reorder levels. All other parts will have stock levels above or equal to the reorder levels. I will then print a report listing all of the products that need reordering. | Order report listing only these products :"Fiesta 1.1 Exhaust", "Peugeot 406 Clutch" and "Astra Left Door Mirror". |
| 2. | Stock levels must be automatically adjusted when parts are written on a invoice because they have been used in a repair. | I will set the stock levels of every part to 5 units. I will then fill out an invoice using these parts : 2 * 175 MXT Tyres, 2 * 15 inch windscreen wipers, 4 * spark plugs. I will then print out a stock list. | All of the parts on the stock list should have 5 units in stock except for : 175 MXT Tyres - 3 units, 15 inch windscreen wipers - 3 units, spark plugs - 1 unit. |
| 3. | The advertisement must be clear to read from a distance. | I will get ten people to try and read the advert from a distance of ten metres and ask them if they can tell me about the garage from the advert. | If eight people can tell me most of the information about the garage then I will conclude that the advertisement is clear. |
1. | Design is the process of deciding
how you will set up your information system using the
software packages you choose. |
| 2. | A good design will consider alternative
possibilities at every stage and justify the decisions that are made.
|
| 3. | The design of an information system can be broken down into four smaller steps :
| 4. | In the
software selection you must decide which software packages to use
to create your information system. You should identify the activities that you need to
carry out, determine how well two or three packages can perform these activities and then
make a justified choice of package. One possible way of writing up your software selection
is to draw up a table.
|
| 5. | If you have a choice of different
hardware devices then you will need to select the most
appropriate devices. For example would an ink jet
printer or a laser printer be better for a particular job ?
|
| 6. | The items to include in a
plan will depend upon the type of task that is being
tackled.
|
| 7. | The test plan
should explain how you will test whether or not the information system you create
meets the desired outcomes you listed in the
analysis. The tests you carry out can be
absolute or
subjective and should use
typical,
extreme and
erroneous test data. The test plan should include an
explanation of each test and the expected outputs that each test
should produce.
|
|
Section 47 : Implementation |
Implementation is using appropriate software packages to create the system you have designed. Often students spend far too much time on the implementation. They naturally want to make their system look and operate in as professional a manner as possible. And of course the implementation is by far the most interesting part of the project. But it is a mistake to spend lots of time working on the implementation and neglect the other stages of the project. Remember in most cases the implementation is worth less than half of the marks for a project.
When implementing a system it makes sense to implement the most important parts first.
During the implementation you need to collect evidence to show how the information system was created. If you decide to make any changes from your design then you will need to explain why the changes have been made.
You will not need to do this for your coursework, but if your were producing a system for a real company the last part of the implementation would be to set up the system at their premises for them, manage the changeover from any existing older system to the new one and train staff to use it.
During the implementation stage you need to collect evidence of the work you have done. You need to show that you have used the software packages with a good degree of skill and understanding. You also need to demonstrate that you have solved the problem in an efficient way.
To do this you must obtain printouts of all of the different parts of the solution to the problem. You then need to annotate (write on) these printouts to explain what they mean. An unexplained printout is a waste of paper.
The sort of evidence that you need to obtain will depend upon the task you are working on. This table gives some ideas of what evidence it might be useful to include for a variety of different types of task :
| Type of Task | Useful Printouts |
| Database | Data collection forms. Lists of data entered into the database. Validation checks used. Example reports / queries. |
| Spreadsheet | Spreadsheet including test data. Spreadsheet showing formulae used. Macro sheet listings. |
| DTP / Word Processing / Graphics | Printouts of pages annotated to show where functions such as
centering,
tables,
fonts etc. have been used. Justification of choice of clipart etc. Data files used for mail merging. |
During the implementation stage you need to get printouts of your work at various levels of development. This will demonstrate how you have developed your information system. The evidence you produce during the testing stage should be sufficient to demonstrate that your final version has been implemented properly.
Never throw any printouts you obtain away. You may find later on that they would have provided useful evidence.
During the implementation you will probably find that you need to change your design :
There is nothing wrong with modifying your design part way through implementing the system. If you do this then :
If your were implementing a system for a real company then once you had created it you would need to install it at the company's premises. If your new system was replacing an older existing system you would need to decide how to carry out the changeover from the old to the new system. Data that was stored in the old system may need to be transferred onto the new system (possibly using a standard file format).
If the system you created carried out an essential task for a company then they may be reluctant to simply give up using their old system and replace it with a new one until they were convinced that the new system worked properly. One of four different changeover methods might be followed :
| Method | Description |
| Direct | The old system is scrapped immediately and completely replaced by the new system. This requires minimum effort, but if there are any problems with the new system the data in the old system will not be up-to-date so it will be hard to return to it. Return to the old system would be harder still if the hardware it used was removed. This changeover method is most frequently used on systems that are not essential to the running of a business. |
| Parallel | Until it is decided that the new system works correctly the new and old system are used together. Every time a transaction occurs (e.g. a sale) it is entered into both systems. This is very time consuming but if there are any problems with the new system they can be easily identified by comparing the output of the two systems. It is also easy to revert back to using the old system if the new system does not work as all the data in it will be up-to-date. |
| Phased | The new system is tried out on a small scale to see if it works. For example a supermarket might introduce a new stock control system at just its Bury branch. At the other branches the old system remains in use. When the supermarket is happy the new system works the old system will be gradually replaced at its other stores with the new system. Any problems that occur would only affect the store(s) that the new system was being tried at. |
| Pilot | The new system is run alongside the old system, but only processes some of the data. For example a supermarket might try out a new stock control system on one till in a store, with all sales at this till being recorded by both the old and new systems. Sales at this till may take longer, but the amount of effort required is less than that for a parallel changeover. The results produced by the two systems can be compared to see if the new system appears to work. As the new system is only being used with a small amount of data, problems that might result from processing a realistically large volume of data might not be noticed. |
For a new system to be effective, staff must be trained so that they know how to use it. Without training staff are likely to make mistakes on the new system and will not know how to exploit the new features it provides. Training can be provided to staff in many ways :
1. | Implementation
is using appropriate software packages to create the system that
you have designed.
|
| 2. | During the implementation you must
collect evidence to show that you have used the software
available with an appropriate degree of skill. This evidence will usually take the
form of printouts.
|
| 3. | Printouts should be obtained at
various levels of development of the information system to show how it was built up.
All printouts must be annotated to explain what they mean.
|
| 4. | You may decide to
change your design during the implementation. If you do
this then you must explain why the changes have been made.
|
| 5. | If you create a system for a real company you will need to manage the changeover from an older exsiting system to the new one. Four methods can be
used for this :
|
| 6. | Training is instructing users how to use a new system. This could done through meetings, informally or by using a user guide.
| | |||||||||||||||
Section 48 : Testing |
Testing is trying out your system to see whether or not it works as you said it should in the desired outcomes section of the analysis.
You will almost certainly carry out testing in two ways when you are developing your system :
| Informally | During the implementation stage every time you add a new part to your system or change a part of it you will probably try it out to see if it works or not. |
| Formally | During the design stage you should have created a test plan defining a number of tests you will use to see if the system works or not. You will need to carry out these tests and collect printouts to show that the system works. |
During testing you must collect evidence to show whether or not your system passes the tests set out in the test plan.
You may include evidence of both formal and informal testing in a project report. It is vital that evidence of formal testing using your test plan is included.
You must explain by annotating (writing on) any printouts you produce exactly what the printout shows and how it relates to your test plan.
Note that :
If you carry out a test (whether or not it is included in your test plan) and decide to modify your system then always include evidence of the test in your documentation.
For each test you carry out you should include this information in the testing section of a project :
It is a good idea to try and present an overall summary of the results of all of your tests in a table.
It is very helpful to the person assessing your project if you can summarise the results of testing your work. This can be done quite easily by printing a modified version of your test plan.
Here is an example of how this can be done. The original test plan has been modified. These extra columns are added :
| No | Test | Evidence | Passed ? |
| 1. | Does the stock system correctly warn the owner of which products need to be reordered ? | Page T1 - Low stock list. | Yes |
| 2. | Stock levels must be automatically adjusted when parts are written on a invoice because they have been used in a repair. | Page T2 - Stock list before job. Page T3 - Invoice. Page T4 - Stock list after job. |
Yes |
| 3. | The advertisement must be clear to read from a distance. | Page T5 - Results of survey. | No - The yellow telephone number could not be read on the white background. I changed the colour of the number to red. |
| 3R. | The advertisement must be clear to read from a distance (retest). | Page T6 - Results of survey. | Yes |
The Details and Expected Results columns from the test plan are not included here but if space allows they could be left in. Notice that the test numbers match the numbers in the test plan. These numbers should also be written onto the actual results obtained from each test.
Because test three was failed the advert was modified and retested. The results of this test are recorded with the number 3R.
1. | Testing is
trying out your system to see whether or not it works as you said it should in
the desired outcomes
section of the analysis.
|
| 2. | You must collect
evidence to show that you have carried out every test in your
test plan. The results of these tests must be annotated to explain whether or not
the actual results match the expected results set out in the
test plan.
|
| 3. | If a test is not passed then you
should explain why and if possible correct the problem and then carry out the test again.
|
| 4. | It is very useful if you produce a
summary of the results of your testing.
| |
Section 49 : Evaluation |
The purpose of the evaluation is to review the information system that you have created and decide whether or not it is a good solution to the problem set at the start or the project.
The evaluation should not simply be a summary of the work that you have done throughout the project and how easy or difficult it was to produce each part of the system. Vague statements such as "At first I found the task very hard, but with a lot of work I gradually overcame the difficulties ..." etc are not very useful.
The evaluation must be produced with reference to the original statement of the problem, and the desired outcomes set out in the analysis. Which of the outcomes set out in the analysis does the system meet and which does it not ? How well does it meet these requirements ?
When considering which of the requirements the system meets you may want to discuss :
It does not matter if your system does not do exactly what you wanted it to. What is important is that you identify and point out all of the problems that exist with your system. Be honest !
1. | The purpose of the
evaluation is to review the information
system that you have created and decide whether or not it is a good solution to the
problem set at the start or the project.
|
| 2. | The evaluation must be produced with
reference to the original statement of the problem, and the
desired outcomes set out in the
analysis.
|
| 3. | You must explain which requirements
have or have not been met and how well the requirements are met. Possible improvements
to the system can be suggested.
| |
Section 50 : Documentation |
If your system will be used by other people then you will need to produce a user guide explaining how to use the system. There are many examples of user guides that you can look at to get ideas about what information to include in a user guide and how to lay it out.
Exactly what to put into your user guide will depend upon what the system you have created does. Here are some suggestions for sections / chapters that you might want to include :
Pictures can speak many thousands of words, so try to include as many screen shots as possible, showing the user how to use the system.
You do not need to explain to the user how to use the software packages that you have used to create your information system. You only need to explain how to use the system you have set up. You may assume that the user knows how to use the package that your system has been created with.
It can be difficult to decide whether or not your user guide can be understood by other people. You already know how to use the system, so why not get someone else to read the user guide and see if they can use your system ?
It may be useful to supplement a printed user guide with a help system that the user can access through a computer. Help systems have a number of advantages over printed guides.
In addition to a user guide, new systems are usually supplied with system documentation. System documentation describes the results of the analysis and design of the system, the test plan, and shows how the system has been implemented.
Examples of items that might be included in system documentation are :
System documentation is not intended to be read by the user. It is produced so that later on somebody else can understand how the system works so that they can modify it. This may need to be done to remove a bug that was not noticed during testing or to add extra features that were not originally required. System documentation is also known as technical or maintenance documentation.
A help system explains how to use a software package on the screen. Providing help information on the screen has several advantages over a printed guide :
1. | A new computer system can be supplied with three different types of documentation. They are a user guide,
system documentation and on-screen help.
|
| 2. | A user guide
explains how to use an information system. It is intended to be read the user(s) of the information system.
|
| 3. | You should produce a user guide whenever
you develop an information system which will be used by other people.
|
| 4. | The user guide should explain how to use
your information system, not how to use the software packages
that you have created the system with.
|
| 5. | Possible sections to include in a user
guide are hardware and software requirements, installing, loading, saving, backing up, troubleshooting and contents together
with instructions on what to do with the system when it is loaded.
|
| 6. | System documentation describes the results of the analysis and design
of the system,
the test plan, and shows how the system has been implemented. It is intended to be read by someone who has
to maintain a system, to
fix bugs in it that were not found during testing or to add new features to it.
|
| 7. | System documentation includes items such as the results of the feasibility study, a
system flowchart,
plans for record structures in a database
and
listings of programs or macros.
|
| 8. | A help system explains how to use a software package on the screen. New software packages are provided with help systems in addition to
or instead
of a user guide.
|
| 9. | A help system can have several advantages over a printed user guide. These include lower production costs, more extensive information, the use of sound and animations, a search facility,
context sensitivity and Internet updates.
| |
Section 51 : Thanks |
The author would like to express his gratitude to the following companies who have given their permission to use photographs in this product. To view the photographs please press on the numbers in the table.
| Company | Photographs
| Hewlett Packard |
1, 2,
3, 4,
5, 6 | Microsoft |
1,
2,
3 | Seagate |
1, 2 | |
Many of the product names referred to in the GCSE ICT Companion 04 are trademarks of the companies producing the products. In particular :
Microsoft® Notepad, Microsoft® Works™, MS-DOS® and Windows® are trademarks and/or registered trademarks of Microsoft Corporation in the United States and other countries.
The screen shots used in the user interface article ( 1, 2, 3) are used by permission of Microsoft Corporation.
Section 52 : Legal |
This package is protected by copyright law. Any unauthorised duplication of the package will be prosecuted or pursued in a civil court. The package remains the property of Cedar Education. You are granted a limited licence to use this package subject to the licence agreement detailed below.
Definitions
| The Package | The package consists of all of the files that are supplied on the CD-R. In this notice the term package refers to either the whole package or any part of it. The package is known as "The GCSE ICT Companion 04" or "ICT Companion". |
| The Copyright Owner | The copyright owner of this package is Mr P. Meakin. The package is distributed by Cedar Education. |
| The Purchaser | The purchaser is either the person who originally purchased the package or the person who is now responsible for the duties that the original purchaser used to perform. |
| The Institution | The institution is the organisation that the purchaser works for and on whose behalf the software was purchased. |
| The Public | Any person or group of people who are neither students at nor employees of the institution. |
| We | "We" refers to the copyright owner and Cedar Education. |
| You | "You" is the institution (as defined above). |
Licence Agreement
| 1. | This licence agreement must be read in conjunction with the definitions above. |
| 2. | This licence agreement is between the Copyright Owner and the Institution. |
| 3. | The package is supplied on an "as is" basis. It is not warranted to be fit for any particular purpose, course of study or to be free of defects. |
| 4. | The package may not be copied except by the purchaser. Copies may only be made for the purpose of installing the package according to the terms of this licence. |
| 5. | The package may be installed on either :
The package may not be used on more than sixty computers within the institution at any time. |
| 6. | Additionally the package may also be installed on the home computers of up to sixty students (or other number as specified on the delivery note) currently studying at the institution. The package must be removed from the home computer of any student who leaves the institution. |
| 7. | No part of this package may be placed on any network or computer system to which the public has access. |
| 8. | The package may be made accessible to your students through a web server that can be accessed on the Internet provided that suitable security measures such as a login system are in place to ensure that the general public can not access it. You must register your intent to do this and obtain approval from us by email before making the ICT Companion available in this way. Please provide the URL that the ICT Companion will be accessible at. If we approve your registration you remain responsible for ensuring that access to the ICT Companion is only available to your students. You will be held responsible if you make the ICT Companion available to the public as this is a breach of Copyright Law and may affect our sales. |
| 9. | We have used our reasonable efforts to ensure that the relevancy indicators provided by the course selector and traffic light indicators are correct as at July 2004. However inevitably in such a complex exercise some errors may exist. It remains the responsibility of the teacher and student to check what is required for a particular course of study with the subject specification published by the examining body. We will not be held reposnsible for any failure to do this. |
| 10. | The maximum liability, howsoever arising, of the copyright owner and Cedar Education to the purchaser shall be the amount originally paid by the purchaser to buy the package. |
| 11. | Articles from the package may be printed for use by students at the institution. |
| 12. | The law governing this licence agreement is the law of England. |
Section 53 : Contact |
If you would like to :
then please contact us. Cedar Education can be contacted at :
| Electronic Mail | info@cedar.u-net.com |
| World Wide Web | www.cedar.u-net.com |
| Fax | 01925 75 9583 |
| Post | Cedar Education |
If you are experiencing difficulties when using the ICT Companion then please visit the support section of our website by going to www.cedar.u-net.com and selecting the support option. Solutions to commonly experience problems can be found at the site.
If you have access to the Internet then click here to email Cedar Education.
GCSE ICT Companion 04 - (C) P Meakin 2004