
Computer Networks |
A computer network is a group of computers which are connected together to allow communication between them.

Computer networks can be classified in many different ways. Some important comparisons are :
1.
| Over how wide an area the network is spread. Networks in
small areas are known as local area networks (LANs)
and networks which cover larger areas are known as
wide area networks (WANs).
|
| 2.
| Whether network resources such as file storage space and
printers are controlled
centrally by a server or whether control is distributed
between the network stations on a peer-to-peer network.
|
| 3.
| How the communication links between the stations on the network are arranged. This
arrangement is known as the network topology.
| |
The speed at which data can be sent between different computers on a network is vital. The data transmission rate of a network or connection is commonly referred to as its bandwidth. Many home computers and computer networks have now been linked together to form the Internet.
Computer networks are usually put into one of two classes depending on how large an area the network covers. The two types of network are :
| Examples of LANs | Examples of WANs |
| A typical school computer network. | The Internet. |
| A network of computers used to share book information within a library. | A network of bank cash dispensers. |
| A ticket booking system used by a chain of high street travel agents. | |
| Properties of LANs | Properties of WANs |
| Covers a small area, usually just one site. | Covers a large area, often linking together several sites. |
| Computers connected by NIC and cables. | Computers connected by modems and telephone lines, ISDN, broadband or similar. |
| Fast transmission of data. | Slow transmission of data. |
Computers which are connected to a network are called stations. Stations on a LAN are normally connected to the network using a network interface card (NIC) and some cable. The cable might be made of copper or optical fibres (made of glass fibres).
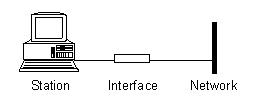
Cables must run all the way around a building that has a LAN installed. Every station on the network must be connected to a cable.
Sometimes a radio transceiver can be used to connect a computer to a LAN instead of a cable. Using a radio means that the computer does not have to be plugged into the network, so it can be moved around more easily.
Connecting computers together at different locations on a WAN is more difficult than connecting computers on a LAN. This is because it is not possible to join two computers which may be thousands of miles away from each other by a simple cable.
Therefore connections to a WAN are usually made over a public network such as the Public Switched Telephone Network (PSTN). The cables that connect the computers are owned by a telephone company. Other companies pay the telephone company money to use its cables to build their WANs.
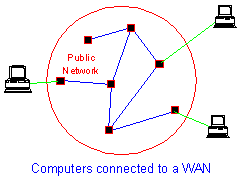
Telephone companies provide many different alternative methods that can be used to connect computers at different locations together. The three most common systems are :
| Method | Description | Speed
| Modem and Telephone Line
| A modem converts digital computer data into analogue form
so that it can be sent across a standard telephone line to another computer.
| Slow
| Terminal Adaptor and ISDN Channel
| A terminal adaptor sends data in digital form down a
special type of connection called an ISDN channel.
| Faster
| Broadband
| An ADSL or Cable Modem sends data in digital form down a telephone line or cable TV connection.
| Very Fast
| | ||||
Modems are often used to connect individual computers to a WAN. A modem can transmit data over a standard telephone line. You can use a modem wherever you can use a telephone.
Because the telephone network was set up before computers were in widespread use, telephone lines were not designed to carry the digital signals that computers use. They were designed to carry human voices in the form of analogue electrical waveforms.
A special device known as a modem must be used to enable a computer to communicate over a telephone line. The modem converts the binary digital data that the computer wants to transmit into an analogue signal for transmission down the telephone line. Another modem must be used at the other end of the telephone line to convert the analogue signal back into a digital one that the receiving computer can understand.
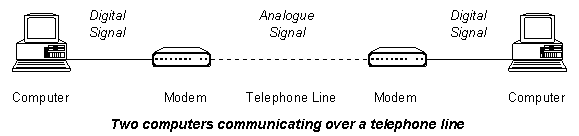
Modulation is the process of converting digital electrical signals generated by a computer into analogue electrical signals which can be transmitted over a telephone line. Demodulation is the process of converting received analogue signals back into digital signals which a computer can understand.
The speed at which data can be transmitted over a telephone line has increased steadily. Most modern modems can receive and transmit data at up to 56.6KBps (kilobits per second). Transmission speeds over a telephone line are very slow compared to other methods. Alternatives such as ISDN and broadband can send data much more quickly.
| Advantages of Modem over ISDN and Broadband |
|
A terminal adaptor can be used to connect computers on a WAN together using an Integrated Services Digital Network (ISDN) channel.
ISDN channels are a more modern form of connection than the public switched telephone network. Data can be transmitted digitally over an ISDN channel, so faster transmission speeds can be achieved than when data is sent using a modem and an analogue telephone line. ISDN channels are not available in all countries.

A single ISDN channel transmits data continuously at 64KBps (kilobits per second). This compares to a maximum speed of 56.6KBps for a modem. More than one ISDN channel can be used at a time to send data between two computers. If two channels were used then a speed of 2*64=128KBps could be achieved. When very fast speeds are required, large numbers of channels (e.g. 32) can be used together or (if available) broadband could be used instead.
| Advantages of ISDN over Modem |
|
The term broadband is commonly used to refer to high speed connections to a WAN such as the Internet. Broadband connections have become available in the UK in the last few years, but whether or not you can use broadband depends upon where you live. A typical broadband system can transmit and receive data at a speed of 560KBps. This means that data can be transmitted ten times more quickly using broadband than using a modem and telephone line. Because broadband connections are fast it is possible to use them for applications which needs to send a lot of data such as video conferencing.
There are two main methods of connecting a computer to a WAN using broadband. They are :
| Method | Description
| ADSL Modem and Telephone Line
| This method is only available at locations that have a telephone line which is connected to an ADSL (Asynchronous Digital Subscribe Line) enabled telephone
exchange. By connecting an ADSL modem to the computer and the telephone line it is possible to access a WAN through the telephone line and use the telephone to make voice calls at the same time.
| Cable Modem and Cable TV
| This method is only available at locations that have a connection to a cable TV network. By plugging a cable modem into the computer and the cable
TV control box it is possible to access a WAN through the cable TV connection.
| |
As well as installing the required hardware it is necessary to contact the company that owns the telephone/cable TV line to get them to enable broadband on a connection before it can be used. A monthly
fee will have to be paid to use the service, but this usually does not depend on how much the connection is used.
| Advantages of Broadband over Modem or ISDN |
|
One of the most important reasons for connecting computers to a network is to let the computers on the network share expensive resources such as file storage space and printers. Access to these resources must be managed in some way. This can be achieved using either a server based network or a peer-to-peer network.
Server Based Networks
The most common type of network used in a business or school environment is a server based network. On a server based network access to shared resources like storage devices and printers is obtained through special server computers. Three different types of computer are usually connected to a server based network :
The file server must ensure that people can only access files that they are permitted to. Most file servers do this by making each user log on with a user name and password before they can access any files. The user name that a user logs on with will determine which files the user can access.
The printer server controls access to shared network printers. Each station on the network can print out on the printer(s) connected to the printer server. If lots of people try to print at the same time then the printer server puts all the documents that are being printed in a queue. The documents are usually printed by the printer server in the order that they were sent by the users.

A large server based network may have more than one file or printer server connected to it.
Peer-to-Peer Networks
Peer-to-peer networks do not have special computers which are used as servers. Instead any computer on the network can load information from the hard disk of any other computer. A computer on the network can use any printer connected to any other computer.
Peer-to-peer networks are cheaper to set up and easier to manage than server based networks. They are however less secure. Because of this peer-to-peer networks are used mainly by small companies who trust their employees and do not have the necessary technical staff to maintain a server based network.

Network topology refers to the layout used to wire the computers together. There are four common topologies. Any topology can be used regardless of whether a network is local or wide area, server based or peer-to-peer.
| Bus (or Line) | Ring |
|
|
|
|
| Star | Hierarchical |
|
|
|
|
Data transmitted through a network or between two hardware devices is carried by a medium. The most common media are described here :
Wired
| Copper Cable
| Copper cable is used to electronically connect together computers on most LANs and in telephone lines. It allows reasonably fast
transmission and extra connections can easily be added to a copper cabled network. Data transmitted along
a copper cable can be corrupted by electrical interference.
| Optical Fibre
| Optical fibre can transmit data much more quickly than copper cables and across longer distances. This is because the data is carried as light rather than electrical signals. Optical fibres are interference
free and transmit data more securely than copper cables. The hardware required to use optical fibres is more complex and expensive than that needed to connect to a network using copper cable.
| Wireless
| Radio
| Radio transmission is sometimes used as a method to directly connect computers (usually laptops) to a LAN. Radio connections are slower than wired connections and more vulnerable
to interference. It is easy to add extra computers to a radio network as no new wiring is required. Computers connected by radio can be moved around whilst remaining connected to the network.
| Microwave
| Microwave transmission is used to connected together two different sites that belong to a WAN. For two sites to be connected by a microwave link there must be a line-of-sight
between them (you must be able to see one site from the other) and they must be within about 30 miles of each other. Operating a microwave link is cheaper than paying to use the telephone network if you have a lot of data
to send but transmissions can be affected by poor weather conditions.
| Satellite
| Satellites provide a versatile but expensive means of transmitting data. Satellites can transmit data very quickly and (subject to a suitably located satellite) to/from anywhere in the world. A suitable satellite
dish and transceiver are required. Data transmitted by satellite is less affected by the weather than data sent by microwave as the signal travels through space rather than through the atmosphere.
| Infra-Red
| Infra-red transmission sends data through the air as invisible light. Infra-red transmission speeds are very slow so this method is not usually used in networks. Instead it is used by hardware devices to
communicate with each other. For example a remote control communicates with a televsion using infra-red and a laptop could print to a printer by infra-red.
| | ||
The most common network topology is the bus (or line) topology. It is cheap and easy to set up a bus network because relatively little cable is required but bus networks are not as reliable as other topologies. If the main cable breaks anywhere along the network the computers connected to it will no longer be able to communicate with each other.
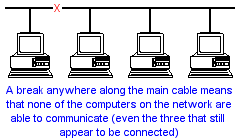
One way to reduce the effect of a cable break is to split the network up into sections using hubs or switches. This diagram shows a bus network that has been split up into three sections :

A sectioned network is more reliable than a standard bus topology. If a cable connecting a computer to a hub breaks then only that one computer will be affected. All of the other computers will continue to be able to use the network (note however that if the main backbone cable fails none of the computers will be able to use the network).
Hubs and switches are also used to connect together the computers at different levels in a hierarchical network.
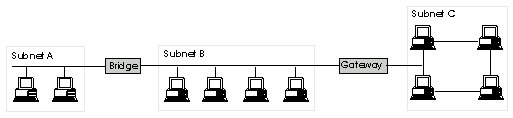
Sometimes a number of LANs can be connected together to make a WAN. For example a company with LANs in each of its offices might choose to connect all these LANs together to make a WAN. If this is done then the workers at the different offices will be able to share information across the network. To connect two networks together one of two pieces of hardware is required :
| Bridge | If the two networks are of the same type they can be connected together using a bridge. The bridge simply copies data that is being transmitted from one network onto the other. |
| Gateway | If the networks are of different types then the job of passing data between them is more complicated. Data that is sent from one network to the other will need to be converted from the format that is used on the sending network into the format that is used on the receiving network. This job is done by a gateway. |
There is no limit to the number of networks you can connect together in this way. In the example below three networks are connected together. Note that computers on Subnet A can talk to computers on Subnet C by sending messages through Subnet B.
In complex network such as the Internet there are many different routes that data could be sent down to travel from one computer or subnet to another. Devices called routers are used to determine what route to send data along.
Computers connected to a network are more vulnerable to security threats than stand-alone computers. This is because :
For this reason extra security measures are usually applied to computers connected to a network. These may be implemented by a network operating system. Likely network security measures include :
| Network Security Measures | ||
| User Names and Passwords | The use of a user name and password system restricts who can access what data on a networked computer system. Users often have to log on to a file server before they can use a computer connected to a network. | |
| File Access Rights | File access rights specify what actions a user can take on a file or directory. The rights that a user has will depend upon the user name he is logged on with. | |
| Logs | When a user name and password system is in use a log can be kept of who has done what on a computer system. This may deter unwanted activity and will help track down anyone who has made unauthorised used of a computer. | |
| Encryption | Encryption is the coding of data so that it can not be read without being decoded first. Data is often encrypted as it is transmitted around a network so that if it is intercepted it can not be read. | |
| Firewall | A firewall is used to control and monitor data sent between two networks or between a home computer and a network. Firewalls can limit the types of data that are allowed to pass between networks and identify and block both viruses and attempts to hack into a network. | |
Ensuring security is even more essential when a computer is connected to a public network such as the Internet. Standard security measures such as backing up and using a virus checker should also be used on computers connected to a network.
Here are some of the advantages and disadvantages of networking a group of computers togther :
| Advantages |
|
GCSE ICT Companion 04 - (C) P Meakin 2004